KEEP IN TOUCH
Subscribe to our mailing list to get free tips on Data Protection and Cybersecurity updates weekly!







Microsoft says a massive series of phishing attacks has targeted more than 10,000 organizations starting with September 2021, using the gained access to victims’ mailboxes in follow-on business email compromise (BEC) attacks.
The threat actors used landing pages designed to hijack the Office 365 authentication process (even on accounts protected by multifactor authentication (MFA) by spoofing the Office online authentication page.
In some of the observed attacks, the potential victims were redirected to the landing pages from phishing emails using HTML attachments that acted as gatekeepers ensuring the targets were being sent via the HTML redirectors.
After stealing the targets’ credentials and their session cookies, the threat actors behind these attacks logged into the victims’ email accounts. They subsequently used their access in business email compromise (BRC) campaigns targeting other organizations.
“A large-scale phishing campaign that used adversary-in-the-middle (AiTM) phishing sites stole passwords, hijacked a user’s sign-in session, and skipped the authentication process even if the user had enabled multifactor authentication (MFA),” the Microsoft 365 Defender Research Team and Microsoft Threat Intelligence Center (MSTIC) said.
Also Read: How often should you pen test?
“The attackers then used the stolen credentials and session cookies to access affected users’ mailboxes and perform follow-on business email compromise (BEC) campaigns against other targets.”
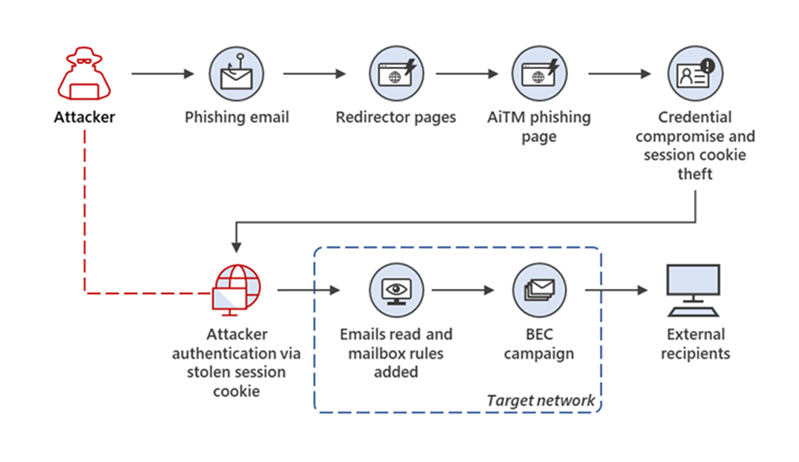
The phishing process employed in this large-scale phishing campaign can be automated with the help of several open-source phishing toolkits, including the widely-used Evilginx2, Modlishka, and Muraena.
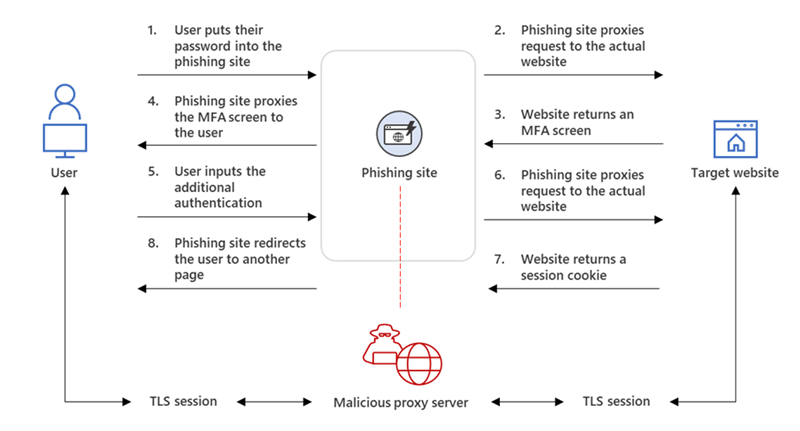
The phishing sites used in this campaign worked as reverse proxies and were hosted on web servers designed to proxy the targets’ authentication requests to the legitimate website they were trying to sign in to via two separate Transport Layer Security (TLS) sessions.
Using this tactic, the attackers’ phishing page acted as a man-in-the-middle agent that intercepts the authentication process to extract sensitive information from hijacked HTTP requests, including passwords and, even more importantly, session cookies.
After the attackers got their hands on the targets’ session cookie, they injected it into their own web browser, which allowed them to skip the authentication process, even if the victims’ had MFA enabled on the compromised accounts.
To defend against such attacks, Microsoft recommends using “phish-resistant” MFA implementations with certificate-based authentication and Fast ID Online (FIDO) v2.0 support.
Also Read: What is a data protection officer? Through the lens of a Master DPO
Other recommended best practices that would boost protection include monitoring for suspicious sign-in attempts and mailbox activities, as well as conditional access policies that would block attackers’ attempts to use stolen session cookies from non-compliant devices or untrusted IP addresses.
“While AiTM phishing attempts to circumvent MFA, it’s important to underscore that MFA implementation remains an essential pillar in identity security,” Redmond added.
“MFA is still very effective at stopping a wide variety of threats; its effectiveness is why AiTM phishing emerged in the first place.”
Additional technical details and indicators of compromise linked to this campaign are available at the end of Microsoft’s report.