KEEP IN TOUCH
Subscribe to our mailing list to get free tips on Data Protection and Cybersecurity updates weekly!







Microsoft says BlackCat ransomware affiliates are now attacking Microsoft Exchange servers using exploits targeting unpatched vulnerabilities.
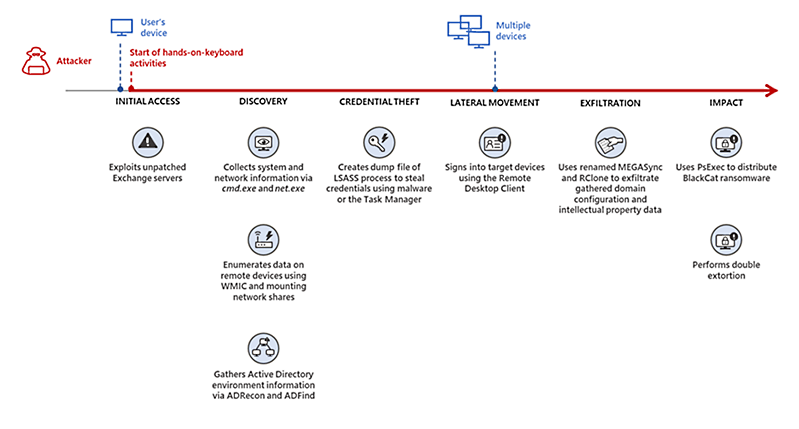
In at least one incident that Microsoft’s security experts observed, the attackers slowly moved through the victim’s network, stealing credentials and exfiltrating information to be used for double extortion.
Two weeks after the initial compromise using an unpatched Exchange server as an entry vector, the threat actor deployed BlackCat ransomware payloads across the network via PsExec.
“While the common entry vectors for these threat actors include remote desktop applications and compromised credentials, we also saw a threat actor leverage Exchange server vulnerabilities to gain target network access,” the Microsoft 365 Defender Threat Intelligence Team said.
Also Read: Guarding against common types of data breaches in Singapore
Although it didn’t mention the Exchange vulnerability used for initial access, Microsoft links to a security advisory from March 2021 with guidance on investigating and mitigating ProxyLogon attacks.
Also, while Microsoft did not name the ransomware affiliate who deployed BlackCat ransomware in this case study, the company says several cybercrime groups are now affiliates of this Ransomware as a Service (RaaS) operation and are actively using it in attacks.
One of them, a financially motivated cybercrime group tracked as FIN12, is known for previously deploying Ryuk, Conti, and Hive ransomware in attacks mainly targeting healthcare organizations.
However, as Mandiant revealed, FIN12 operators are much faster as they sometimes skip the data theft step and take less than two days to drop their file-encrypting payloads across a target’s network.
“We’ve observed that this group added BlackCat to their list of distributed payloads beginning March 2022,” Microsoft added.
“Their switch to BlackCat from their last used payload (Hive) is suspected to be due to the public discourse around the latter’s decryption methodologies.”
BlackCat ransomware is also being deployed by an affiliate group tracked as DEV-0504 that typically exfiltrates stolen data using Stealbit, a malicious tool the LockBit gang provides its affiliates as part of its RaaS program.
Also Read: Upholding privacy by design principles: Why does it matter?
DEV-0504 has also used other ransomware strains starting with December 2021, including BlackMatter, Conti, LockBit 2.0, Revil, and Ryuk.
To defend against BlackCat ransomware attacks, Microsoft advises organizations to review their identity posture, monitor external access to their networks, and update all vulnerable Exchange servers in their environment as soon as possible.
In April, the FBI warned in a flash alert that the BlackCat ransomware had been used to encrypt the networks of at least 60 organizations worldwide between November 2021 and March 2022.
“Many of the developers and money launderers for BlackCat/ALPHV are linked to Darkside/Blackmatter, indicating they have extensive networks and experience with ransomware operations,” the FBI said at the time.
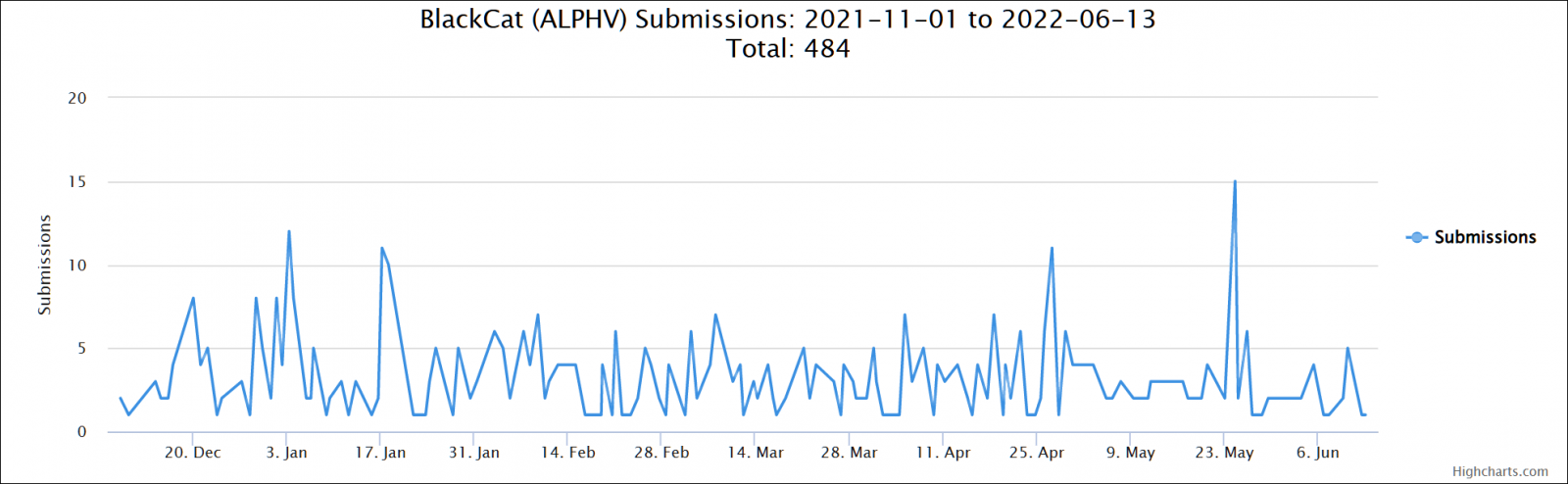
However, the real number of BlackCat victims is most likely a lot higher given that more than 480 samples have been submitted on the ID-Ransomware platform between November 2021 and June 2022.
In its April alert, the FBI also asked admins and security teams who detect BlackCat activity within their networks to share any related incident info with their local FBI Cyber Squad.
Helpful information that would help track down and identify the threat actors using this ransomware in their attacks includes “IP logs showing callbacks from foreign IP addresses, Bitcoin or Monero addresses and transaction IDs, communications with the threat actors, the decryptor file, and/or a benign sample of an encrypted file.”