KEEP IN TOUCH
Subscribe to our mailing list to get free tips on Data Protection and Cybersecurity updates weekly!






Privacy by Design is a good practice to be incorporated in the entire design architecture when it comes to making secure products. In this digital age, consumers are wary of their data privacy and security, and businesses that showcase accountability in this regard stand a better chance of keeping their business continuity and product usage safe.
Privacy by Design is an approach applied when creating new systems and technologies. With this, privacy is incorporated into the technology and systems by default, and simply means that the product is designed with privacy as a top priority along with other purposes the system can accommodate.
“Privacy must become integral to organizational priorities, project objectives, design processes, and planning operations. Privacy must be embedded into every standard, protocol and process that touches our lives.”
A formal Privacy by Design framework published in 2009
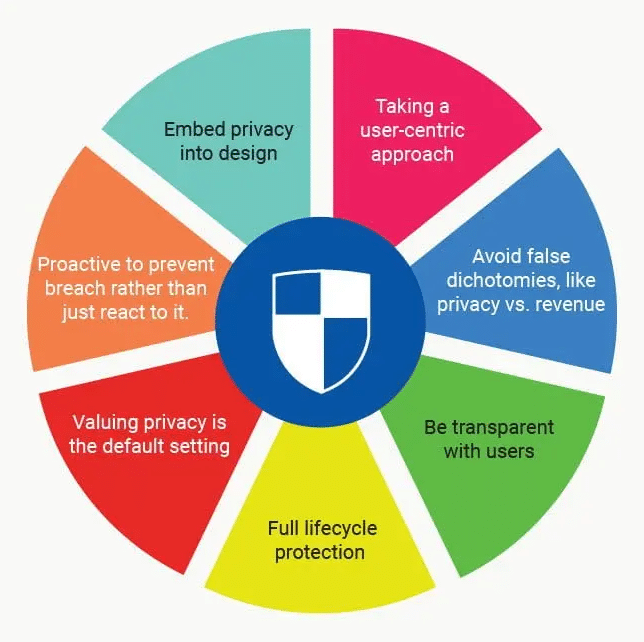
The following 7 Key Principles of Privacy by Design can make you exceptional among businesses and gain higher trust of your customers.
This principle prevents and anticipates privacy breaches before they happen, because privacy has been incorporated into the product. Security is a top priority from the beginning of the design process and adopting a Privacy by Design methodology protects organizations from privacy issues that could hurt the company’s reputation.
This principle is used in a way whereby personal data are automatically protected in any system or business practice. The system is designed to be secure so any person don’t have (to a significant extent), do more work to protect their own privacy. By making Privacy by Design the default, they don’t have to doubt the process, but if they want to take further steps to secure their own data, they can.
Ann Cavoukian, Ph.D, the author of Privacy by Design: The 7 Foundational Principles says privacy should be “integral to the system, without diminishing functionality.” Through embedding privacy into the design, the system will run better rather than trying to add it on later. Privacy must be integrated in a holistic and innovative way, making user experiences better.
People should always have the option to deny access to their data and still be able to use the product. Of course, some features are impossible to work without specific data, so that’s okay as long as the user understands. However, don’t ever limit access to functionality by forcing your users to give their data.
Information is secured and protected when it enters the system, is retained safely, and then properly destroyed. Privacy by Design considers security from start to finish.
Accountability, openness and compliance are essential for an effective and secure system. The level of security it provides creates trust and holds your organization accountable by being clear about your system. Moreover, the system improves by allowing users and other involved parties to see how information moves through your system.
The stakes of letting it fall into the wrong hands are extremely high especially if you are dealing with customer’s private information. Additionally, your system must be enhanced for your users and all of their needs; you should make user privacy your top concern.
Privacy by Design should be seamlessly integrated into your system — allowing it to work smoothly and securely from day one. Privacy by Design starts by emphasizing privacy and security throughout the system design process.
You must first do a privacy audit on your system, broken down from start to finish. Look at how privacy has been embedded into your current system, identify weak-points, and create new user-friendly solutions. Implementing Privacy by Design on an existing system or product may be time consuming and difficult because you have to completely deconstruct and analyze the system you have in place.
Contact Privacy Ninja for a non-obligatory consultation and we will identify and share the areas for improvements in your organization.