KEEP IN TOUCH
Subscribe to our mailing list to get free tips on Data Protection and Cybersecurity updates weekly!







Security researchers have noticed a malicious campaign that used Windows event logs to store malware, a technique that has not been previously documented publicly for attacks in the wild.
The method enabled the threat actor behind the attack to plant fileless malware in the file system in an attack filled with techniques and modules designed to keep the activity as stealthy as possible.
Researchers at Kaspersky collected a sample of the malware after being a company product equipped with technology for behavior-based detection and anomaly control identified it as a threat on a customer’s computer.
Also Read: 7 Simple Tips On How To Create A Good Business Card Data
The investigation revealed that the malware was part of a “very targeted” campaign and relied on a large set of tools, both custom and commercially available.
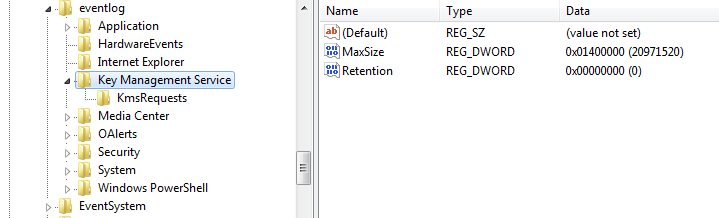
One of the most interesting parts of the attack is injecting shellcode payloads into Windows event logs for the Key Management Services (KMS), an action completed by a custom malware dropper.
Denis Legezo, lead security researcher at Kaspersky, says that this method has been used “for the first time ‘in the wild’ during the malicious campaign.”
The dropper copies the legitimate OS error handling file WerFault.exe to ‘C:\Windows\Tasks’ and then drops an encrypted binary resource to the ‘wer.dll’ (Windows Error Reporting) in the same location, for DLL search order hijacking to load malicious code.
DLL hijacking is a hacking technique that exploits legitimate programs with insufficient checks to load into memory a malicious Dynamic Link Library (DLL) from an arbitrary path.
Legezo says that the dropper’s purpose is to loader on the disk for the side-loading process and to look for particular records in the event logs (category 0x4142 – ‘AB’ in ASCII. If no such record is found, it writes 8KB chunks of encrypted shellcode, which are later combined to form the code for the next stager.
“The dropped wer.dll is a loader and wouldn’t do any harm without the shellcode hidden in Windows event logs” – Denis Legezo, lead security researcher at Kaspersky
The new technique analyzed by Kaspersky is likely on its way to becoming more popular as Soumyadeep Basu, currently an intern for Mandiant’s red team, has created and published on GitHub source code for injecting payloads into Windows event logs.
Based on the various techniques and modules (pen-testing suites, custom anti-detection wrappers, final stage trojans) used in the campaign, Legezo notes that the entire campaign “looks impressive.”
Also Read: How Bank Disclosure Of Customer Information Work For Security
He told BleepingComputer that “the actor behind the campaign is rather skilled by itself, or at least has a good set of quite profound commercial tools,” indicating an APT-level adversary.
Among the tools used in the attack are the commercial penetration testing frameworks Cobalt Strike and NetSPI (the former SilentBreak).
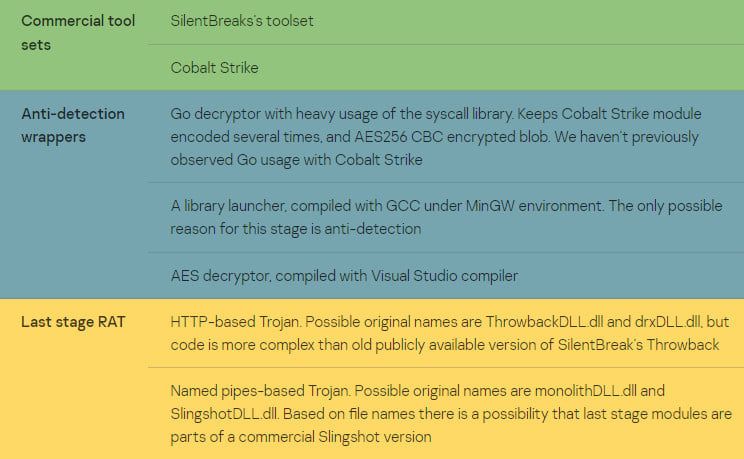
While some modules in the attack are believed to be custom, the researcher notes that they may be part of the NetSPI platform, for which a commercial license was unavailable for testing.
For instance, two trojans named ThrowbackDLL.dll and SlingshotDLL.dll may be tools with the same name known to be part of the SilentBreak penetration testing framework.
“We started the research from the in-memory last stager and then, using our telemetry, were able to reconstruct several infection chains” – Denis Legezo
The investigation tracked the initial stage of the attack to September 2021 when the victim was tricked into downloading a RAR archive from the file sharing service file.io.
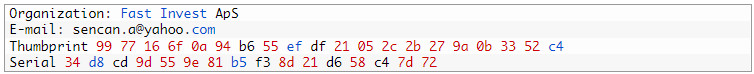
The threat actor then spread the Cobalt Strike module, which was signed with a certificate from a company named Fast Invest ApS. The certificate was used to sign 15 files and none of them were legitimate.
In the majority of cases, the ultimate purpose of the targeted malware with such last stager functionality is obtaining some valuable data from the victims, the researcher told BleepingComputer.
While studying the attack, Kaspersky did not find any similarities with previous campaigns associated with a known threat actor.
Until a connection with a known adversary is made, the researchers track the new activity as SilentBreak, after the name of the tool most used in the attack.