KEEP IN TOUCH
Subscribe to our mailing list to get free tips on Data Protection and Cybersecurity updates weekly!







The Chinese hacking group Deep Panda is targeting VMware Horizon servers with the Log4Shell exploit to deploy a novel rootkit named ‘Fire Chili.’
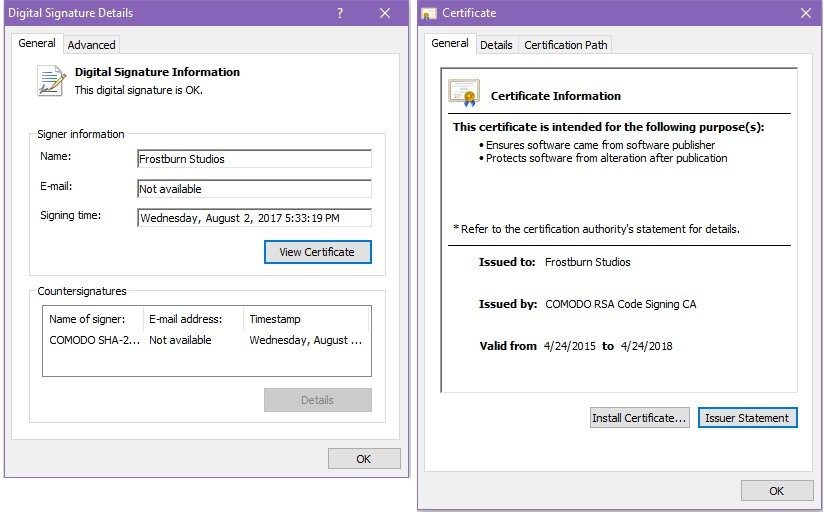
The rootkit is digitally signed using a certificate from Frostburn Studios (game developer) or one from Comodo (security software) to evade detection by AV tools.
Analysts at Fortinet who tracked Deep Panda’s recent activity believe the certificates have been stolen from the mentioned software developers.
Deep Panda is a notorious Chinese APT focusing on cyber-espionage operations that has been active for many years now. The FBI had arrested one of its members back in 2017 after linking him with the exploitation of three zero-day vulnerabilities.
In a recent Deep Panda campaign discovered by Fortinet, the hacking group is deploying the new ‘Fire Chili’ rootkit to evade detection on compromised systems.
Also Read: Top 25 Data Protection Statistics That You Must Be Informed
A rootkit is malware typically installed as a driver that hooks various Windows APIs to hide the presence of other files and configuration settings in the operating system. For example, by hooking Windows programming functions, a rootkit can filter data to not display malicious file names, processes, and Registry keys APIs to Windows programs requesting the data.
In the attacks, the rootkit is signed by valid digital certificates allowing it to bypass detection by security software and load into Windows without any warnings.
Upon launch, Fire Chili performs basic system tests to ensure it’s not running on a simulated environment and checks that the kernel structures and objects to be abused during operation are present.
Fortinet reports that the most recent supported operating system version for Fire Chili is Windows 10 Creators Update, released in April 2017.
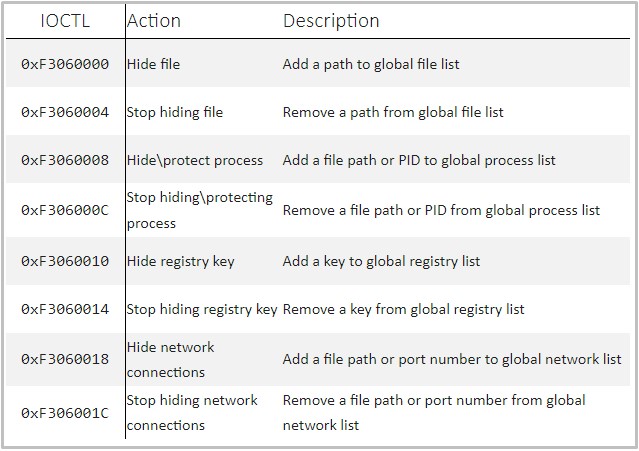
The goal of the rootkit is to keep file operations, processes, registry key additions, and malicious network connections hidden from the user and any security software that could be running on the compromised machine.
For this hiding function, the malware uses IOCTLs (input/output control system calls) that are pre-populated with the malicious artifacts and can be dynamically configured.
For example, to hide malicious TCP connections from netstat, the rootkit intercepts routine IOCTL calls to the device stack, retrieves the complete list of network connections, filters out its own, and finally returns a sanitized structure.
Also Read: Completed DPIA Example: 7 Simple Helpful Steps To Create
While looking into the latest Deep Panda campaign, Fortinet found several overlaps with Winnti, another notorious Chinese hacking group known for using digitally signed certificates.
Also, Winnti is known for persistently targeting gaming companies, so they could have stolen those certificates during one of their successful campaigns.
“The reason these tools are linked to two different groups is unclear at this time. It’s possible that the groups’ developers shared resources, such as stolen certificates and C2 infrastructure, with each other. This may explain why the samples were only signed several hours after being compiled.” – Fortinet
Sophisticated hacking collectives that focus on cyberespionage, and not so much for financial profit, are more likely to be backed or even coordinated by government handlers, so this overlap is hardly surprising.