KEEP IN TOUCH
Subscribe to our mailing list to get free tips on Data Protection and Cybersecurity updates weekly!







A phishing kit has been released that allows red teamers and wannabe cybercriminals to create effective single sign-on phishing login forms using fake Chrome browser windows.
When signing into websites, it is common to see the option to sign with Google, Microsoft, Apple, Twitter, or even Steam.
For example, the login form for DropBox allows you to login using an Apple or Google account, as shown below.
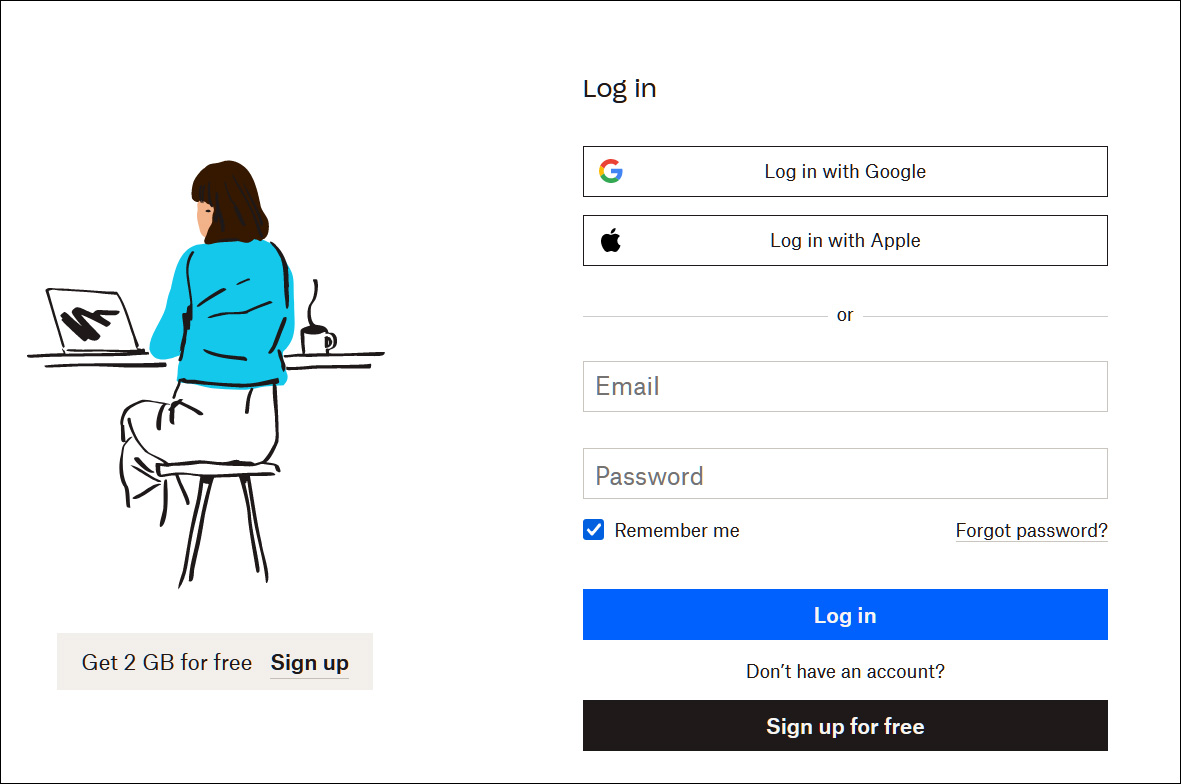
When clicking the Login in Google or App buttons, a single-sign-on (SSO) browser window will be displayed, prompting you to enter your credentials and login with the account.
These Windows are stripped down to only show the login form and an address bar showing the URL of the login form.
Also Read: PDPA compliance for the social service sector
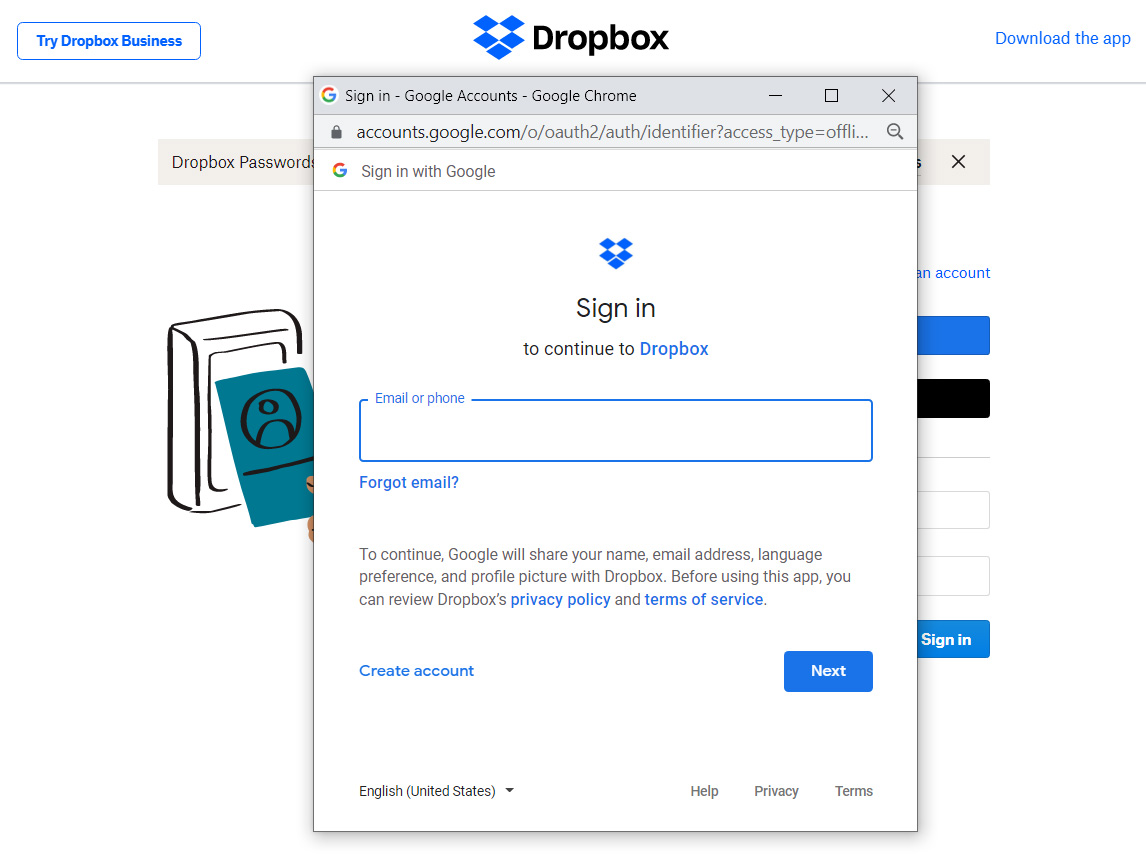
While this address bar is disabled in these SSO windows, you can still use the displayed URL to verify that a legitimate google.com domain is being used to sign you into the site. This URL further adds to the trust of the form and will make you feel comfortable entering your login credentials.
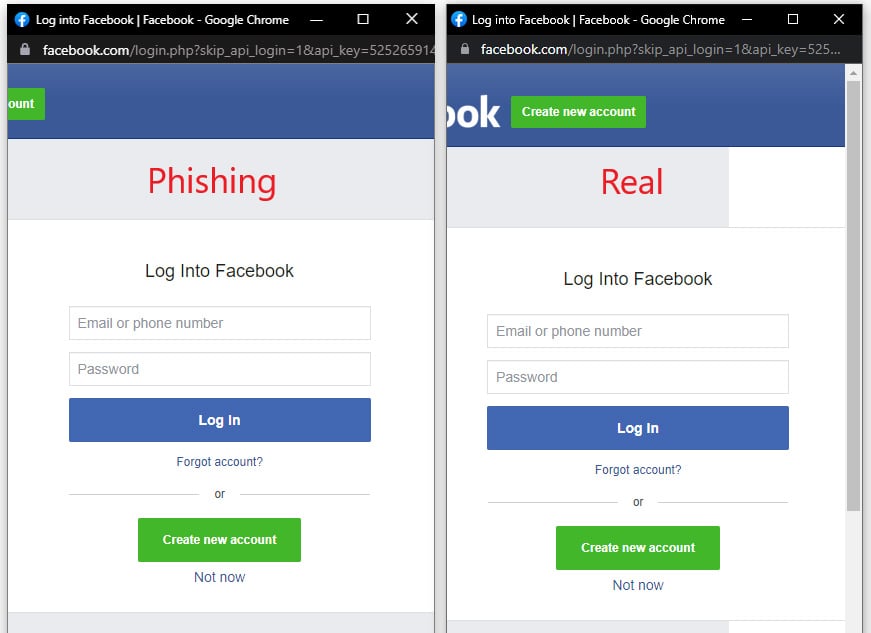
Threat actors have attempted to create these fake SSO windows using HTML, CSS, and JavaScript in the past, but there is usually something a little off about the windows, making them look suspicious.
This is where a new “Browser in the Browser (BitB) Attack” comes into play that uses premade templates to create fake but realistic, Chrome popup windows that includes custom address URLs and titles that can be used in phishing attacks.
Basically, this attack creates fake browser windows within real browser windows (Browser in the Browser) to create convincing phishing attacks.
The Browser in the Browser attack templates was created by security researcher mr.d0x, who released the templates on GitHub. These templates include those for Google Chrome for Windows and Mac and dark and light mode variants.
Also Read: Email spoofing: Avoiding them through good cyber hygiene practices
mr.d0x told BleepingComputer that the templates are very simple to use in creating convincing Chrome windows to display single sign-on login forms for any online platform.
The researcher said that redteamers could simply download the templates, edit them to contain the desired URL and Window title, and then use an iframe to display the login form.
It is also possible to add the HTML for the login form directly into the template, but mr.d0x told BleepingComputer that you would need to align the form properly using CSS and HTML.
Kuba Gretzky, the creator of the Evilginx phishing toolkit, tested the new method and showed how it worked perfectly with the Evilginx platform, meaning it could be adapted to steal 2FA keys during phishing attacks.
mr.d0x told BleepingComputer that this is not a new technique and that Zscaler reported it being used by fake gaming sites in 2020 to steal Steam credentials.
However, now that premade templates for fake Chrome windows are available, redteamers can use them to create convincing phishing sign-in forms to test the defense of their clients or their own company’s employees.
For those who wish to try out the new Browser in the Browser phishing attack, you can grab the templates from GitHub.