KEEP IN TOUCH
Subscribe to our mailing list to get free tips on Data Protection and Cybersecurity updates weekly!







Security researchers tracking the mobile app ecosystem have noticed a recent spike in trojan infiltration on the Google Play Store, with one of the apps having over 500,000 installs and available to download.
Most of these apps belong to a family of trojan malware used in various scams, resulting in financial losses and also loss of sensitive personal information.
Additionally, a new Android trojan built as a WhatsApp mod has been spotted in the wild, circulating via shady websites promoted by social media posts, forums, and SEO poisoning.
These findings come from Dr. Web, who published the details in their January 2022 review of virus activity on mobile devices.
Also Read: 5 ways on how to destroy documents securely to prevent data breach
The threats discovered on the Play Store by Dr. Web’s analysts include cryptocurrency management apps, social benefit aid tools, Gasprom investment clones, photo editors, and a launcher themed after iOS 15.

Most fake investment apps prompt the victims to create a new account and deposit money supposedly for trading, which is simply diverted to the scammer’s bank account. Other apps try to trick the user into signing up for expensive subscriptions.
The majority of the apps reported by Dr. Web have been removed from the Play Store, so while they might have been popular and widely downloaded, we don’t have any numbers to share.
Bleeping Computer was able to find one of the reported apps that’s still available on the Play Store, Top Navigation, which has over 500,000 installations, making this a significant concern due to its widespread use.
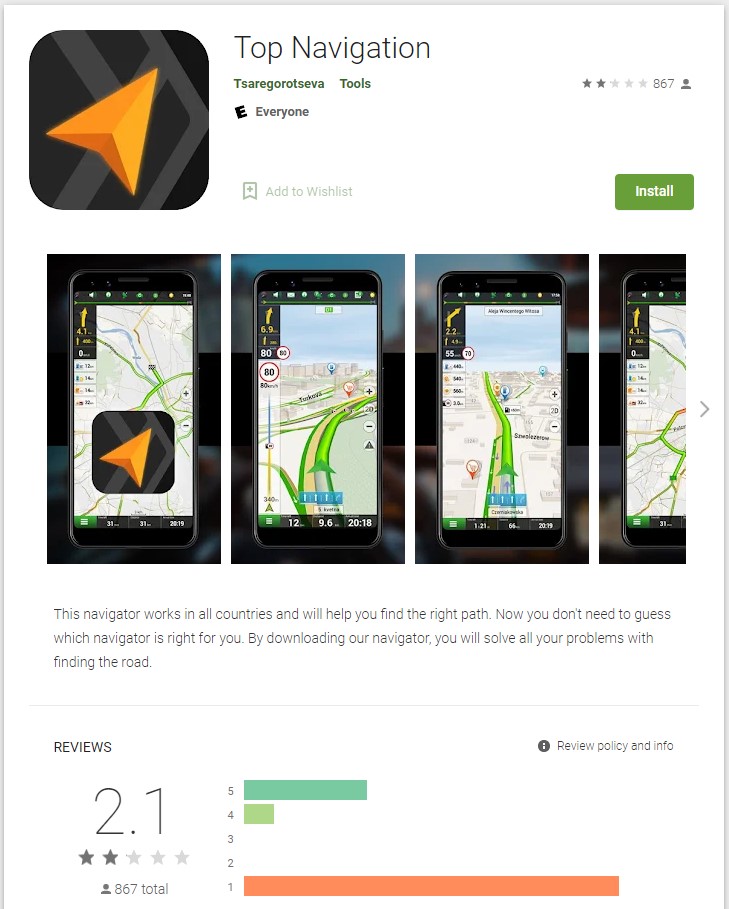
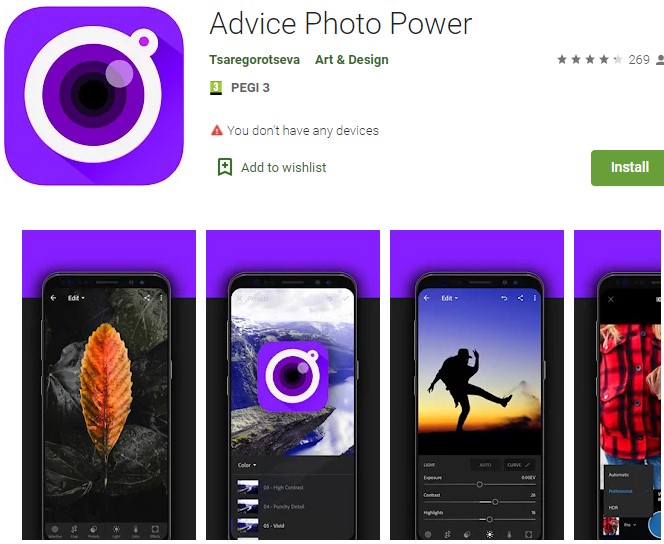
By checking the developer, Tsaregorotseva, we found a second app on the Play Store, Advice Photo Power, with over 100,000 downloads.
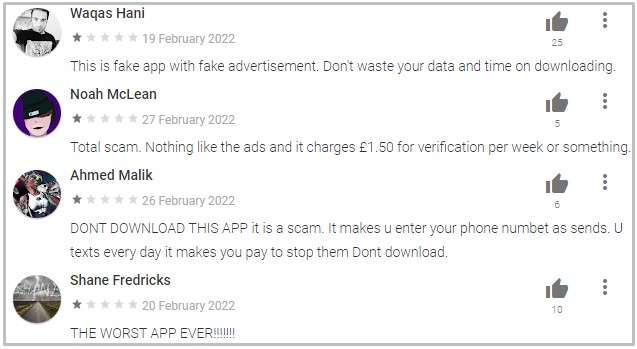
The user reviews under the app describe tactics that resemble subscription scams, charging $2 per week for verification or ad removals, yet offering nothing in return.
Also Read: 7 Useful Tools On How To Find Company Contact Information
As the report details, apps found by Dr. Web will load affiliate service sites and enable paid subscriptions through the Wap Click technology after tricking the victim into entering their phone number.
According to Dr. Web’s report, the most significant threat in January 2022 was trojanized versions of unofficial WhatsApp mods named GBWhatsApp, OBWhatsApp, or WhatsApp Plus. These mods offer Arabic language support, home screen widgets, separate bottom bar, hide status options, call blocking, and the ability to auto-save received media.
These mods are popular in the online communities because they offer additional features not available in the vanilla WhatsApp.

However, in the trojanized versions, bundled malware attempts to snatch notifications from the Google Play Store and the Samsung Galaxy Store apps via the Flurry stat service.
Moreover, the trojan downloads an additional APK from a URL received from the command and control server and requests the user install it under the guise of an update for OBWhatsApp.
This new app is then used to display dialog boxes arbitrarily, featuring content dynamically set and updated remotely, allowing the attackers to redirect users to malicious sites.
Staying safe from these apps is a matter of avoiding APK downloads from obscure sources, checking user reviews, scrutinizing permission requests upon installation, and monitoring battery and internet data consumption afterward.
Also, make sure to check the status of Google Play Protect regularly and add a second layer of protection by using a mobile security tool from a reputable vendor.