KEEP IN TOUCH
Subscribe to our mailing list to get free tips on Data Protection and Cybersecurity updates weekly!







Mobile security company Zimperium has released its annual mobile threat report where security trends and discoveries in the year that passed lay the groundwork for predicting what’s coming in 2022.
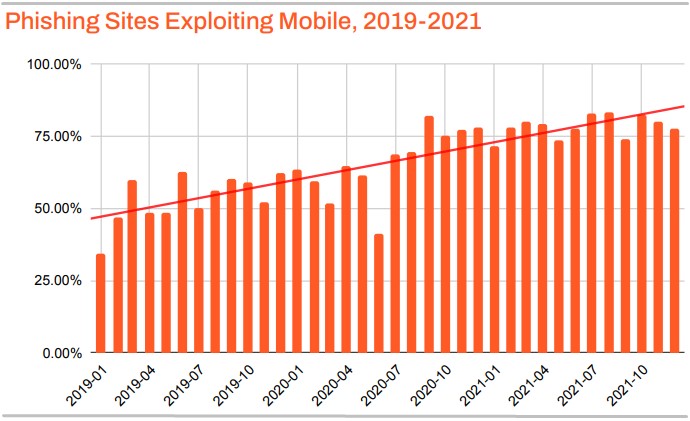
In general, the focus of malicious actors on mobile platforms has increased compared to previous years, mainly due to the push of the global workforce to remote working.
This focus manifested in more significant malware distribution volumes, phishing and smishing attacks, and more efforts to discover and leverage zero-day exploits.
Zero-day vulnerabilities are publicly disclosed or actively exploited bugs with no fixes available from the vendor or developers. As it is vital to fix zero-day bugs, vendors typically rush to release security updates once they are disclosed.
Also Read: 12 Benefits of Data Protection for Business Success
However, according to Zimperium’s client stats and a survey conducted for the report, only about 42% of people working in BYOD (bring your own device) environments applied high-priority fixes within two days from their release.
Roughly one-third required up to a week, while a significant 20% hadn’t patched their mobile devices before reaching the two-week mark.
In 2021, actors focused more on remote workforce or on-premise mobile devices, leading to increased malicious network scans and man-in-the-middle (MiTM) attacks. These attacks are aimed at stealing sensitive information that plays a crucial role in more significant attacks against corporate networks.
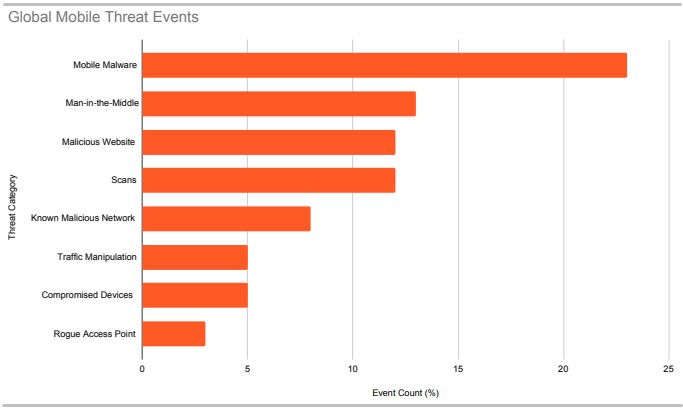
The most prevalent threats for each region of the world in 2021 were the following:
Globally, mobile malware was a problem encountered in 23% of all endpoints protected by Zimperium in 2021, followed by MiTM (13%), malicious websites (12%), and scans (12%).
The mobile operating systems market is dominated by a duopoly of Android and iOS, so inevitably, all comparisons under any spectrum revolve around those two.
Concerning security in 2021, Android appears to be generally more vulnerable than iOS, but the latter tends to have more serious vulnerabilities.
Also Read: Privacy policy template important tips for your business
Judging by volume, Android had 574 vulnerabilities discovered in 2021, a notable reduction from the 859 in 2020, while 79% of them were characterized by low attack complexity. This categorization denotes flaws that are easy to exploit.
Of the 574 Android flaws, 135 (23%) had a CVSS score higher than 7.2, while 18 were rated as critical.
On iOS, security researchers found 357 new vulnerabilities in the year that passed, but only 24% of them are considered low complexity bugs.
Moreover, only 63 (17%) have a CVSS severity rating higher than 7.2, but 45 of the flaws are critical, which means leveraging them may result in significant compromise to a device.
This makes iOS a more challenging but lucrative target because the flaws are difficult to put into action, but the payoff is greater.
This hypothesis is confirmed by the zero-day stats for 2021, with iOS vulnerabilities accounting for 64% of all 17 exploited zero-day attacks targeting mobile devices in 2021.
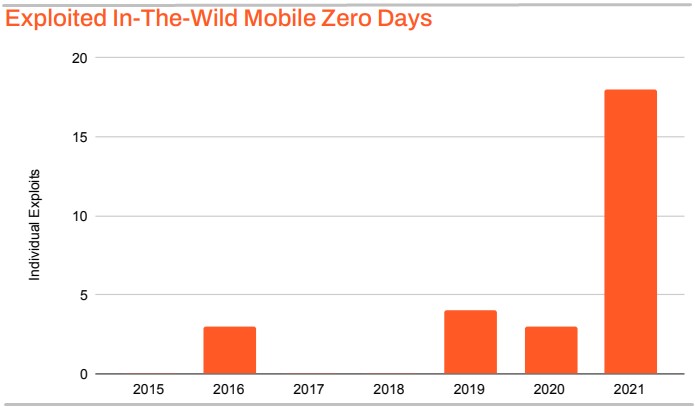
“In 2021, 11 separate zero-day exploited in-the-wild vulnerabilities were revealed targeting Apple iOS and Apple WebKit, accounting for 19% of all zero-day exploits for the year,” reads Zimperium’s report.
Zimperium also analyzed the most popular apps in financial, healthcare, retail, and lifestyle categories on Google Play Store and the Apple App Store. The conclusion is that apps are points of significant security liability for mobile devices.
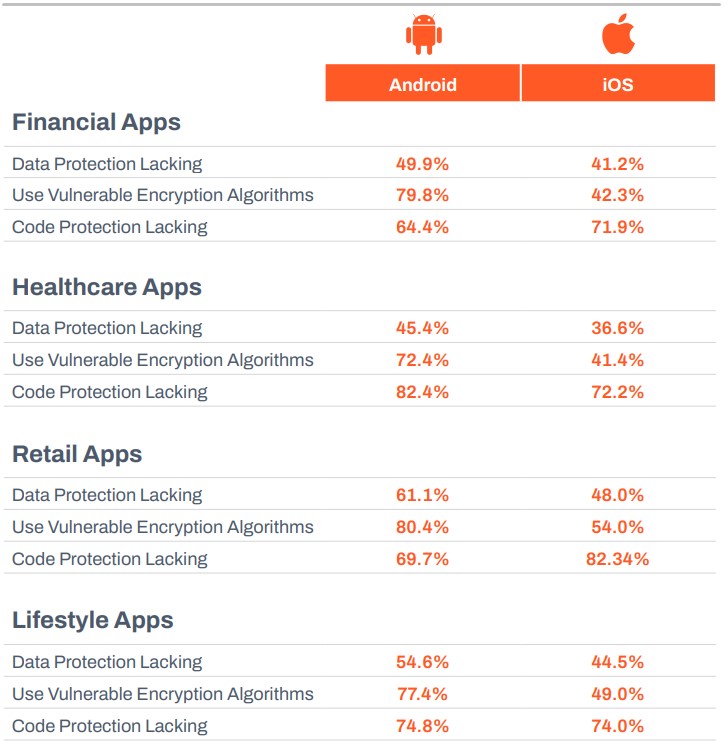
Most notably, 80% of financial apps for Android use vulnerable encryption, while 82% of retail apps on iOS don’t feature any code protection.
As the importance of mobile devices in life and work continues to grow and the number of smartphone users reaches new highs, threat actors are expected to keep up their efforts to attack users on the go.
Even with semiconductor shortages causing supply problems for 2022, smartphone shipments are forecasted to be 1.43 billion. Unfortunately, many of these devices will be the weakest link in the security chain of large organizations, and hence they will be targeted by skilled hackers.
Zimperium’s survey revealed that 84% of security professionals today had enabled Microsoft Office 365 on mobile, with 38% of them being in the process of securing these deployments on a second phase.
This stat perfectly reflects how many organizations sacrificed strict security controls to support productivity and business continuity during times of dramatic changes.
Compared to previous years, both Google (Android) and Apple (iOS) has come a long way regarding security, and their mobile systems are robust enough to rule out easy exploits.
Today, threat actors are forced to discover and chain multiple vulnerabilities to achieve meaningful goals, so these attacks are getting much harder to carry out.
Some of the most notable mobile security discoveries and fixes in the year that passed are:
While it’s too early to know exactly what is coming in 2022, we should expect more of the same.
As such, the key to keeping your devices safe is to reduce the number of installed apps to the absolute minimum. Unfortunately, the more apps you use, the greater the risk for your data.
Finally, keep your mobile OS up to date by applying the available security updates, and for Android, use an AV tool, activate Play Protect, and review app permissions regularly.