KEEP IN TOUCH
Subscribe to our mailing list to get free tips on Data Protection and Cybersecurity updates weekly!







A set of seven vulnerabilities collectively tracked as Access:7 have been found in PTC’s Axeda agent, a solution used for remote access and management of over 150 connected devices from more than 100 vendors.
Three of the security issues received a severity score of at least 9.4 (critical) and could be exploited for remote code execution on devices running a vulnerable version of the Axeda agent.
Developed by Parametric Technology Corporation (PTC), the Axeda platform through locally deployed agents provides telemetry data from IoT devices on the network and the option for remote service.
Axeda agents can run on a wide variety of connected systems, devices in the healthcare industry being more prevalent, which makes them attractive targets for supply-chain attacks.
Also Read: How To Secure Your WiFi Camera: 4 Points To Consider
Security researchers at Forescout’s Vedere Labs and CyberMDX- a Forescout company since February 1st, found that all Axeda agent versions lower than 6.9.3 are vulnerable to a set of seven security flaws.
Dubbed Access:7, the impact of these issues ranges from information disclosure and denial-of-service (DoS) to remote code execution.
| CVE-ID | Description | Impact | Severity Score |
|---|---|---|---|
| CVE-2022-25249 | The Axeda xGate.exe agent allows for unrestricted file system read access via a directory traversal on its web server | information disclosure | 7.5 |
| CVE-2022-25250 | The Axeda xGate.exe agent can be shutdown remotely by an unauthenticated attacker via an undocumented command | denial-of service (DoS) | 7.5 |
| CVE-2022-25251 | The Axeda xGate.exe agent supports a set of unauthenticated commands to retrieve information about a device and modify the agent’s configuration | RCE | 9.4 |
| CVE-2022-25246 | The AxedaDesktopServer.exe service uses hard-coded credentials to enable full remote control of a device | RCE | 9.8 |
| CVE-2022-25248 | The ERemoteServer.exe service exposes a live event text log to unauthenticated attackers | information disclosure | 5.3 |
| CVE-2022-25247 | The ERemoteServer.exe service allows for full file-system access and remote code execution | RCE | 9.8 |
| CVE-2022-25252 | All Axeda services using xBase39.dll can be crashed due to a buffer overflow when processing requests | denial-of service (DoS) | 7.5 |
The Axeda Platform provides connected device manufacturers a development kit that lets them “generate a configured agent installation for a product line,” Forescout says.
This way, manufacturers get telemetry data, and devices can receive service remotely. One agent can represent one or more devices, depending on where it sits: if placed at a gateway, it can serve multiple products, or assets, behind the gateway.
Also Read: How Formidable is Singapore Cybersecurity Masterplan 2020?
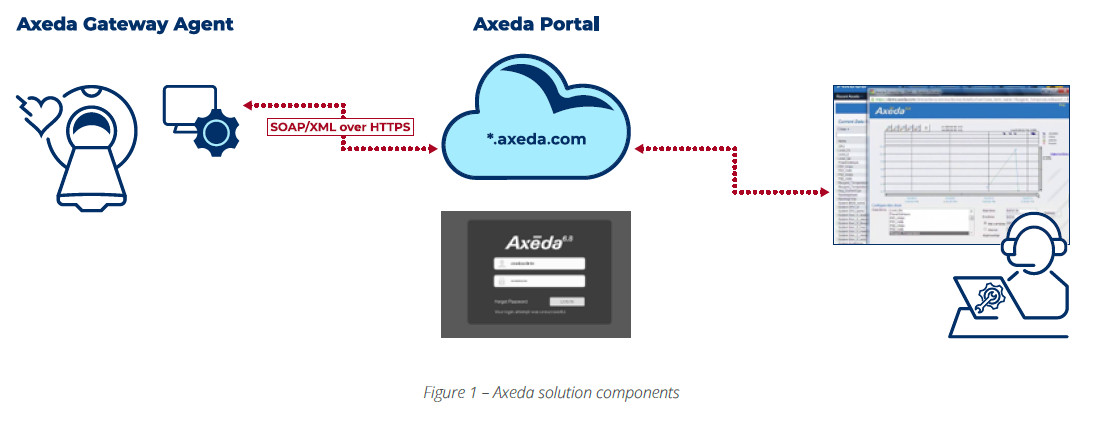
It is worth noting that PTC phased out Axeda in favor of a different, more flexible platform called ThingWorx. Nevertheless, Axeda is still in use by customers in various sectors.
Anonymous customer data that Forescout collects through its Device Cloud solution shows more than 2,000 unique devices running Axeda on their networks.
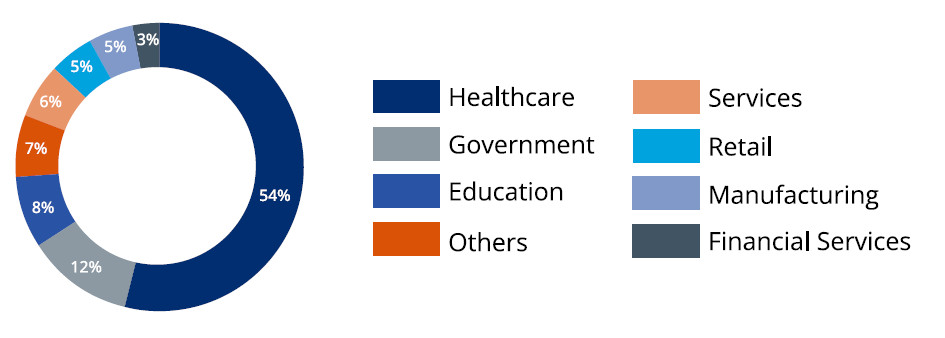
In a report today, Forescout explains that in the case of medical devices, even the less severe Access:7 vulnerabilities can have a significant impact.
For instance, an attacker gaining read access by exploiting CVE-2022-25249 on an imaging or lab device – where Axeda agents are more present, as per Forescount data – could steal protected health information (PHI) or diagnostics about a patient and sell it on for a profit if it’s a high-value victim.
Similarly, exploiting a bug like CVE-2022-25250 a threat actor could shut down the Axeda agent on a device in a targeted attack, making remote service impossible. This can lead to the healthcare unit interrupting therapy or diagnosing a patient.
With a critical vulnerability like CVE-2022-25246 (hardcoded credentials for remote access), Forescout highlights that the password “for a VNC connection is the same across all models or model families for a vendor.”
The researchers underline that the VNC connection can also be used to modify medical information, which could have severe consequences on the patient (e.g. Mistreatment).
Alternatively, adversaries could leverage this advantage to plant malicious code that gives them persistence on the network for future attacks.
Forescout’s Vedere Labs and CyberMDX discovered the Access:7 set of security vulnerabilities and both companies participated in the responsible disclosure.
This was a long process, as is the case with supply chain vulnerabilities that involve a large number of devices and vendors. In this case, 210 days passed from the initial report to the public disclosure.
PTC received a report from CyberMDX on August 10 and then requested proof-of-concept exploits to show that the vulnerabilities can be leveraged in realistic attacks.
In November 2021, PTC notified CISA for coordinated disclosure. In January 2022, PTC started to notify downstream vendors (active customers only).
To reduce risk to a minimum, Forescout created a list of devices currently using or having used Axeda from as many vendors as possible, even if they are inactive Axeda customers, and alerted them of the vulnerabilities.
Axeda has addressed all Access:7 vulnerabilities and device makers should roll out their fixes to customers since patching is the only way to completely mitigate the issues.
If installing the latest versions for the Axeda agent is not possible, Forescout provides the following mitigation advice: