KEEP IN TOUCH
Subscribe to our mailing list to get free tips on Data Protection and Cybersecurity updates weekly!







The new data wiper malware deployed on Ukrainian networks in destructive attacks on Wednesday right before Russia invaded Ukraine earlier today was, in some cases, accompanied by a GoLang-based ransomware decoy.
“In several attacks Symantec has investigated to date, ransomware was also deployed against affected organizations at the same time as the wiper. As with the wiper, scheduled tasks were used to deploy the ransomware,” Symantec revealed today.
“It appears likely that the ransomware was used as a decoy or distraction from the wiper attacks. This has some similarities to the earlier WhisperGate wiper attacks against Ukraine, where the wiper was disguised as ransomware.”
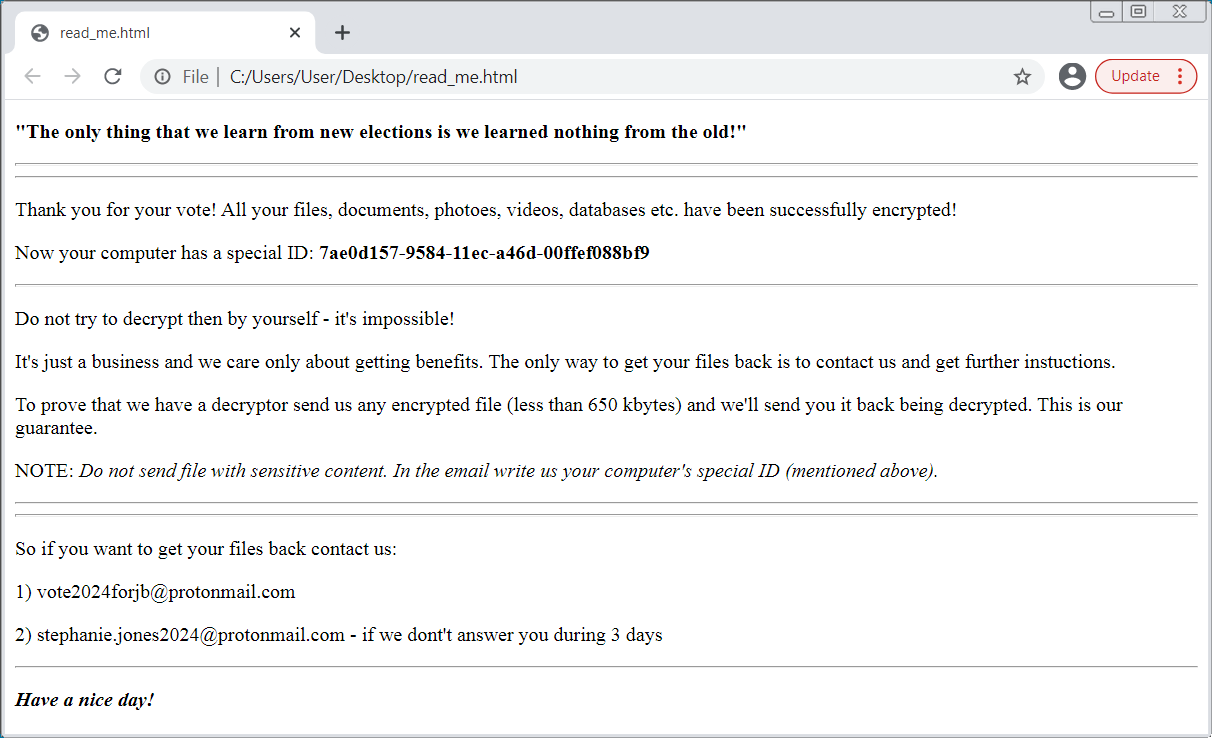
The ransomware decoy also dropped a ransom note on compromised systems, with a political message saying that “The only thing that we learn from new elections is we learned nothing from the old!”
Also Read: Privacy policy template important tips for your business
The ransom note instructs the victims to reach out to two email addresses (i.e., [email protected] and [email protected]) to get back their files.
The wiper, dubbed HermeticWiper by SentinelOne principal threat researcher Juan Andres Guerrero-Saade, was dropped in yesterday’s attacks targeting Ukrainian organizations, and it also ended up on systems outside Ukraine’s borders.
Targets that were hit by wiper attacks also included finance and government contractors from Ukraine, Latvia, and Lithuania, as Vikram Thakur, Technical Director at Symantec Threat Intelligence, told BleepingComputer.
While the cyberattacks occurred yesterday, cybersecurity firm ESET noted that the HermeticWiper malware had a compilation date of December 28th, 2021, which hints at the attacks having been planned.
Also Read: 4 easy guides to data breach assessment
Symantec found evidence of attackers gaining access to victims’ networks well in advance by exploiting Microsoft Exchange vulnerabilities as early as November 2021 and installing web shells before deploying the wiper malware.
For instance, “an organization in Lithuania was compromised from at least November 12, 2021, onwards,” Symantec said.
The wiper malware uses EaseUS Partition Manager drivers to corrupt compromised devices’ files before rebooting the computer. As security researcher Silas Cutler also found, the data wiper also trashes the device’s Master Boot Record, rendering all infected devices unbootable.
This was the second data wiper used against Ukrainian networks since the start of the year. As Microsoft disclosed in January, a destructive data-wiping malware dubbed WhisperGate and camouflaged as ransomware was used in attacks targeting Ukrainian organizations.
Just as HermeticWiper, WhisperGate was used to corrupt files and wipe compromised devices’ Master Boost Records, making it impossible to boot into the operating system or access files stored on the hard drive.
Yesterday’s malware attacks came together with DDoS attacks against Ukrainian government agencies and state-owned banks, similar to the one used last week when similar DDoS disruptions affected Ukrainian government sites and banks.
While the Wednesday attacks have not been attributed, the White House linked last week’s DDoS attacks to Russia’s Main Directorate of the General Staff of the Armed Forces (also known as GRU).
Data wipers have also been a tool often used by Russian state-sponsored hacking groups in the past. A wiper attack that hit thousands of Ukrainian businesses with the NotPetya ransomware in 2017 was linked by the US three years later to Russian GRU hackers.
In 2020, Russian GRU hackers believed to be part of the elite Russian hacking group known as Sandworm were formally indicted by the US for the NotPetya attacks.
This month’s DDoS and malware attacks follow a press release from Ukraine’s Security Service (SSU) saying that the country is the target of a “massive wave of hybrid warfare.“