KEEP IN TOUCH
Subscribe to our mailing list to get free tips on Data Protection and Cybersecurity updates weekly!







A malware named Electron Bot has found its way into Microsoft’s Official Store through clones of popular games such as Subway Surfer and Temple Run, leading to the infection of roughly 5,000 computers in Sweden, Israel, Spain, and Bermuda.
The malware, spotted and analyzed by cyber-intelligence firm Check Point, is a backdoor that gives the adversaries complete control over compromised machines, supporting remote command execution and real-time interactions.
The goal of the threat actors is social media promotion and click fraud, which they achieve by controlling social media accounts on Facebook, Google, YouTube, and Sound Cloud, as Electron Bot supports new account registration, commenting, and liking on these platforms.
Also Read: Completed DPIA Example: 7 Simple Helpful Steps To Create
The operation was first discovered at the end of 2018 when an early Electron Bot variant was submitted to the Microsoft Store as “Album by Google Photos,” published by a spoofed Google LLC entity.
Since then, the malware authors have added several new features to their tool and advanced detection evasion capabilities like dynamic script loading.
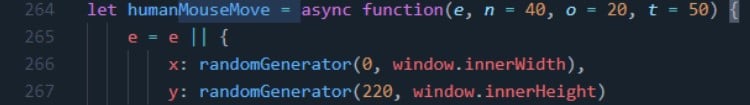
The malware is written in Electron, hence the name, and it can emulate natural browsing behavior and perform actions as if it’s a real website visitor.
For this, it opens a new hidden browser window using the Chromium engine in the Electron framework, sets the appropriate HTTP headers, renders the requested HTML page, and finally performs mouse movement, scrolling, clicks, and keyboard typing.
Electron Bot’s primary goals in the ongoing campaign analyzed by the Check Point researchers are:
These functions are offered as services to those who want to increase their online profits illegitimately, so the gains for the malware operators are indirect.
Also Read: 12 Benefits of Data Protection for Business Success
As for attribution, Check Point reports finding evidence pointing to the actors being based in Bulgaria, but besides that, nothing is known about the malicious actors’ identity or location.
The infection chain begins with the victim installing one of the laced apps from within the Microsoft Store, an otherwise trustworthy source of software.
.jpg)
Upon launching the application, a JavaScript dropper is loaded dynamically in the background to fetch the Electron Bot payload and install it.
The malware launches at the next system startup, connects to the C2 (Electron Bot[.]s3[.]eu-central-1[.]amazonaws.com or 11k[.]online), retrieves its configuration, and executes any commands in the pipeline.
Because the main scripts are loaded dynamically at run time, the JS files dropped on the machine’s memory are very small and seemingly innocuous.
.jpg)
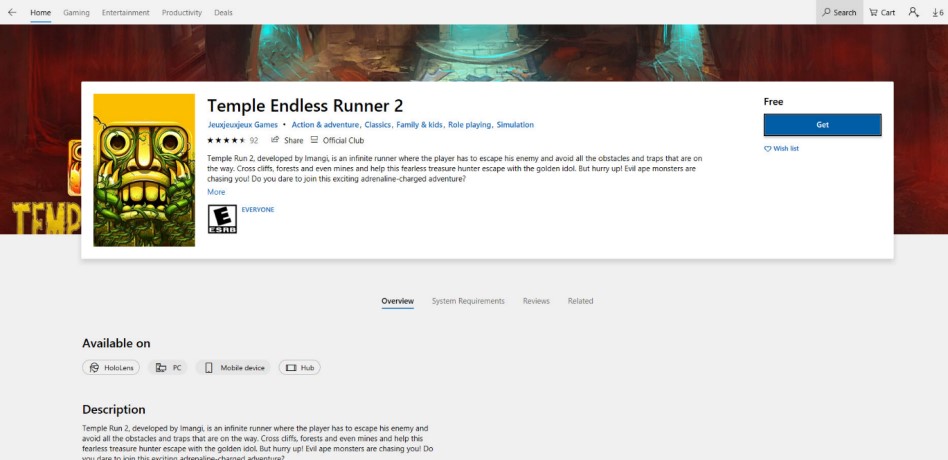
All laced games identified by Check Point featured the expected functionality while the malicious operations unfolded in the background.
This results in having positive user reviews on the Microsoft Store. For instance, Temple Endless Runner 2, which was published on September 6, 2021, has close to a perfect five-star rating from 92 reviews.
Of course, the crooks constantly refresh their lures and use different game titles and apps to deliver the malware payloads to unsuspecting victims.
For now, users may take note of the publishers who released confirmed malicious game apps using the following names:
It is important to emphasize that while the existing version of Electron Bot isn’t causing catastrophic damage to the infected machines, the threat actors may easily modify the code to fetch a second-stage payload like a RAT or even ransomware.
Check Point suggests that Windows users avoid downloading applications with a low review count, scrutinize the developer/publisher details, and ensure that the app name is correct and not typo-squatted.