KEEP IN TOUCH
Subscribe to our mailing list to get free tips on Data Protection and Cybersecurity updates weekly!







An ongoing large-scale phishing campaign is targeting customers of Citibank, requesting recipients to disclose sensitive personal details to lift alleged account holds.
The campaign uses emails that feature CitiBank logos, sender addresses that look genuine at first glance, and content that is free of typos.
The CitiBank customers targeted in these attacks are informed that their account has been put on hold due to a suspicious transaction or a login attempt from someone else.
Also Read: How Being Data Protection Trained Can Help With Job Retention
Because of this, the attackers claim they should take urgent action to verify their accounts to avoid permanent suspension.
.jpg)
If the embedded button is clicked, the victims are taken to a website that looks deceptively like a real Citibank portal, where they are requested to sign in to their online account.
Of course, any user ID and password pairs entered on this website go directly to the threat actors, who may then use the stolen credentials to compromise banking accounts and empty balances.
.jpg)
Bitdefender has been tracking this campaign and shared the associated report with BleepingComputer before publication, and reports the following statistical findings:
Apart from the tactic of creating urgency to cause the recipients to miss obvious signs of fraud and jump into action, phishing actors are also using lures promising enormous winnings.
Also Read: Top 25 Data Protection Statistics That You Must Be Informed
More specifically, Bitdefender has identified another large-volume phishing campaign whose distribution culminated between February 11 and 15, 2022, presenting the recipients with a chance to claim financial compensation from the United Nations.
The trick employed in this case is to recognize the recipient as a scam victim, one of the 150 who was deemed eligible for a compensation of $5,000,000 through Citibank.
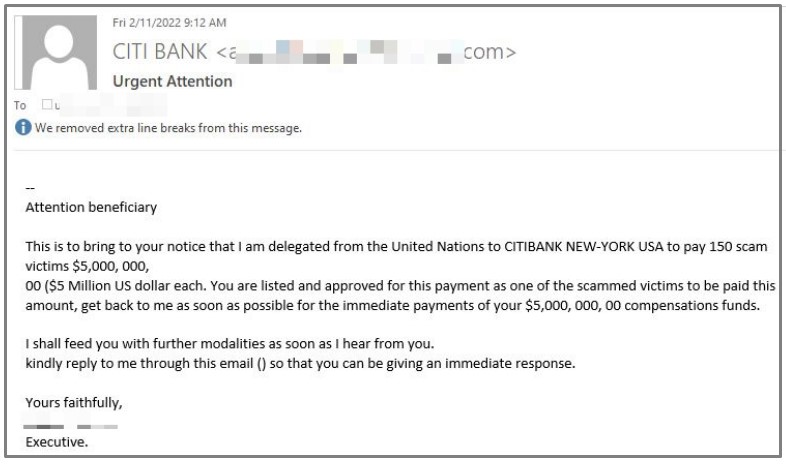
In other cases, the threat actors are doubling the amount to $10,500,000 and attempt to include more details in the email to convince the victim of its validity.
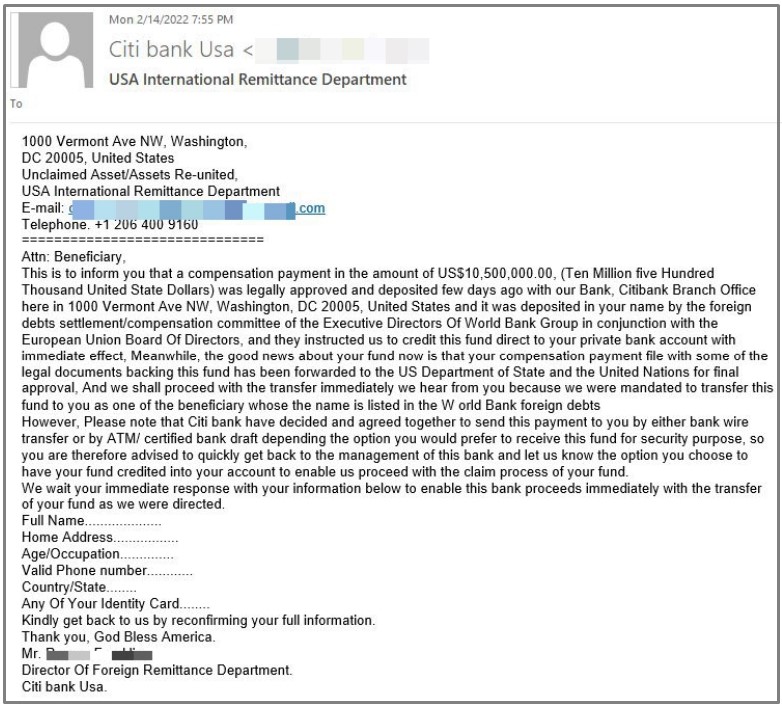
However, in both cases, the fraud should be pretty obvious, as this is neither how compensations work nor at the level they would be awarded in reality.
For the category of people who believe in these emails, the scammers request them to fill out their full name, address, age, phone number, and a scanned copy of their national ID card.
In this campaign, the details stolen by the victims cannot be directly used for fraudulent transactions but can be instead sold to other criminals on cybercrime markets.
Banks rarely ever inform users of important developments on their account via SMS or email, so whenever you receive a message making bold claims, call your bank and ask to speak to an agent.
Do not call phone numbers provided in the email but, instead, visit the bank’s official website and source it from the contact page details.
Finally, never click on buttons embedded in the email body and always double-check the URL you are on when preparing to enter login credentials.