KEEP IN TOUCH
Subscribe to our mailing list to get free tips on Data Protection and Cybersecurity updates weekly!





A report released today dives deep into technical aspects of a Linux backdoor now tracked as Bvp47 that is linked to the Equation Group, the advanced persistent threat actor tied to the U.S. National Security Agency.
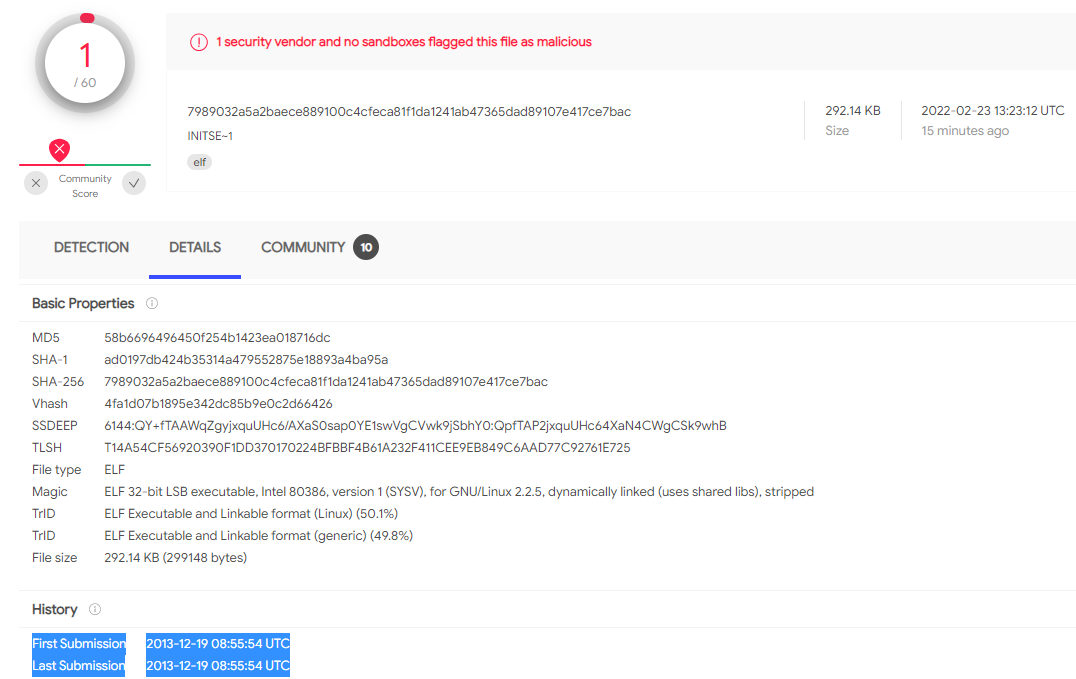
Bvp47 survived until today almost undetected, despite being submitted to the Virus Total antivirus database for the first time close to a decade ago, in late 2013.
Until this morning, only one antivirus engine on Virus Total detected the Bvp47 sample. As the report spread in the infosec community, detection started to improve, being flagged by six engines at the moment of writing.
Also Read: Privacy policy template important tips for your business
The Advanced Cyber Security Research team at Pangu Lab, a Chinese cybersecurity company, says that it found the elusive malware in 2013, during a “forensic investigation of a host in a key domestic department.”
The Bvp47 sample obtained from the forensic investigation proved to be an advanced backdoor for Linux with a remote control function protected through the RSA asymmetric cryptography algorithm, which requires a private key to enable.
They found the private key in the leaks published by the Shadow Brokers hacker group between 2016-2017, which contained hacking tools and zero-day exploits used by NSA’s cyberattack team, the Equation Group.
Some components in the Shadow Brokers leaks were integrated into the Bvp47 framework – “dewdrop” and “solutionchar_agents” – indicating that the implant covered Unix-based operating systems like mainstream Linux distributions, Juniper’s JunOS, FreeBSD, and Solaris.
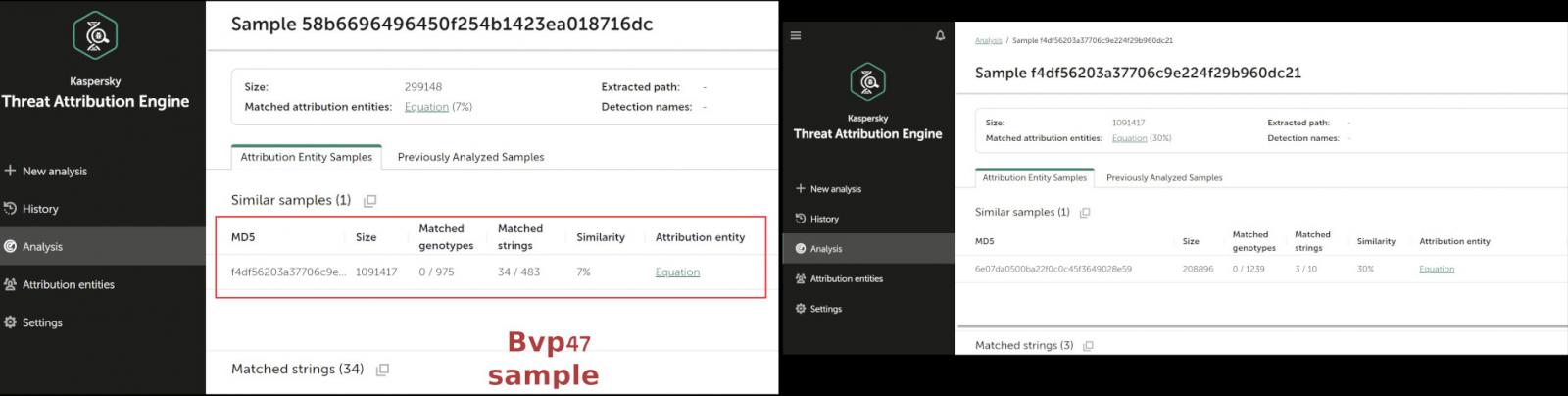
Apart from Pangu Lab attributing the Bvp47 malware to the Equation Group, automated analysis of the backdoor also shows similarities with another sample from the same actor.
Kaspersky’s Threat Attribution Engine (KTAE) shows that 34 out of 483 strings match those from another Equation-related sample for Solaris SPARC systems, which had a 30% similarity with yet another Equation malware submitted to Virus Total in 2018 and posted by threat intel researcher Deresz on January 24, 2022.
Also Read: 4 easy guides to data breach assessment
Costin Raiu, director of Global Research and Analysis Team at Kaspersky, told BleepingComputer that Bvp47’s code-level similarities match a single sample in the company’s current malware collection.
This indicates that the malware was not used extensively, as it usually happens with hacking tools from high-level threat actors, who use them in highly targeted attacks.
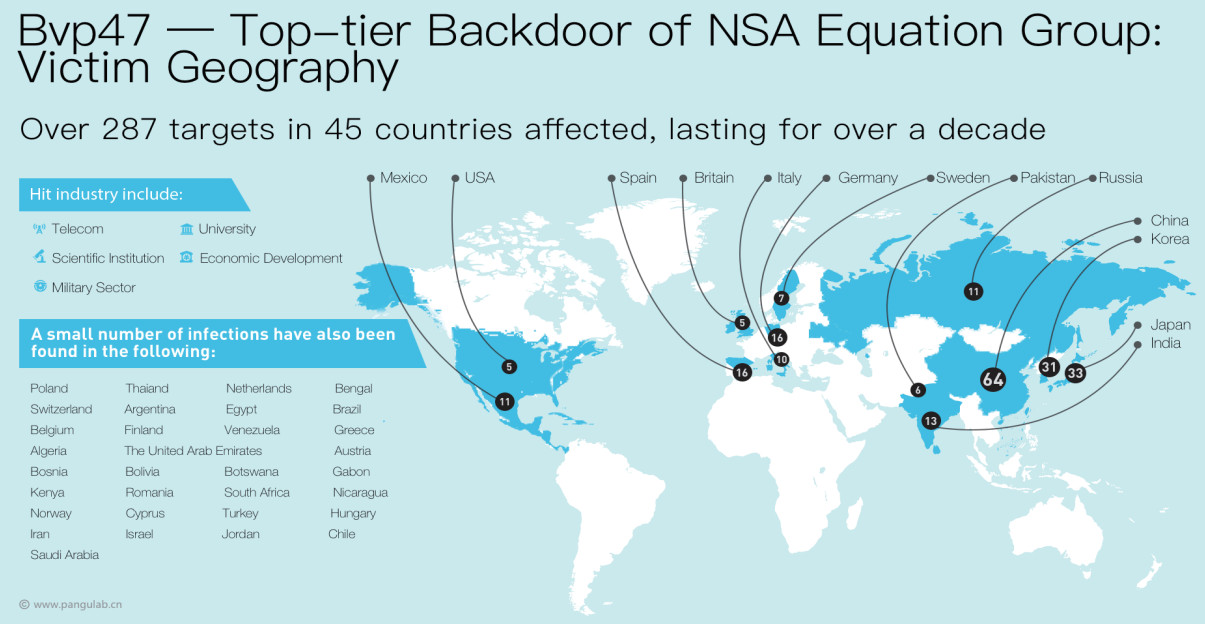
In the case of the Bvp47 Linux backdoor, Pangu Lab researchers say that it was used on targets in the telecom, military, higher-education, economic, and science sectors.
They note that the malware hit more than 287 organizations in 45 countries and went largely undetected for over 10 years.
Pangu Lab’s incident analysis involved three servers, one being the target of an external attack and two other internal machines – an email server and a business server.
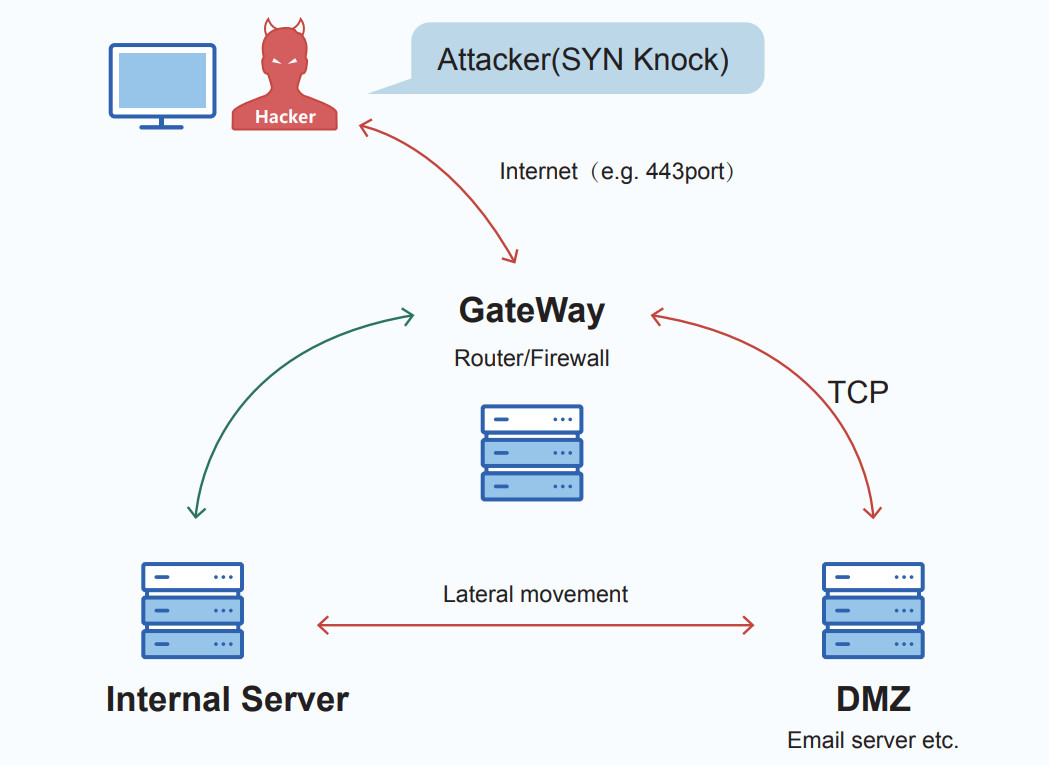
According to the researchers, the threat actor pivoted established a connection between the external server and the email server via a TCP SYN packet with a 264-byte payload.
“At almost the same time, the [email] server connects to the [business] server’s SMB service and performs some sensitive operations, including logging in to the [business] server with an administrator account, trying to open terminal services, enumerating directories, and executing Powershell scripts through scheduled tasks” – Pangu Lab
The business server then connected to the email machine to download additional files, “including the Powershell script and the encrypted data of the second stage.”
An HTTP server is started on one of the two compromised machines, serving two HTML files to the other. One of the files was a base64-encoded PowerShell script that downloads “index.htm,” which contains asymmetrically encrypted data.
A connection between the two internal machines is used to communicate encrypted data via “its own protocol,” Pangu Lab researchers say in their report.
The researchers were able to restore the communication between the servers and summarized it into the following steps, where machine A is the external system and V1/V2 are the email and business server, respectively:
Referring to the above communication technology between the three servers, the researchers assess that the backdoor is the creation of “an organization with strong technical capabilities.”