KEEP IN TOUCH
Subscribe to our mailing list to get free tips on Data Protection and Cybersecurity updates weekly!






A new version of the CryptBot info stealer was seen in distribution via multiple websites that offer free downloads of cracks for games and pro-grade software.
CryptBot is a Windows malware that steals information from infected devices, including saved browser credentials, cookies, browser history, cryptocurrency wallets, credit cards, and files.
The latest version features new capabilities and optimizations, while the malware authors have also deleted several older functions to make their tool leaner and more efficient.
Security analysts at Ahn Lab reported that the threat actors are constantly refreshing their C2, dropper sites, and the malware itself, so CryptBot is currently one of the most shifting malicious operations.
Also Read: Facts About Accountability PDF That You Need to Know About
According to the Ahn Lab report, the CryptBot threat actors distribute malware through websites pretending to offer software cracks, key generators, or other utilities.
To gain wide visibility, the threat actors utilize search engine optimization to rank the malware distribution sites at the top of Google search results, providing a stable stream of prospective victims.
According to screenshots shared of the malware distribution sites, the threat actors use both custom domains or websites hosted on Amazon AWS.
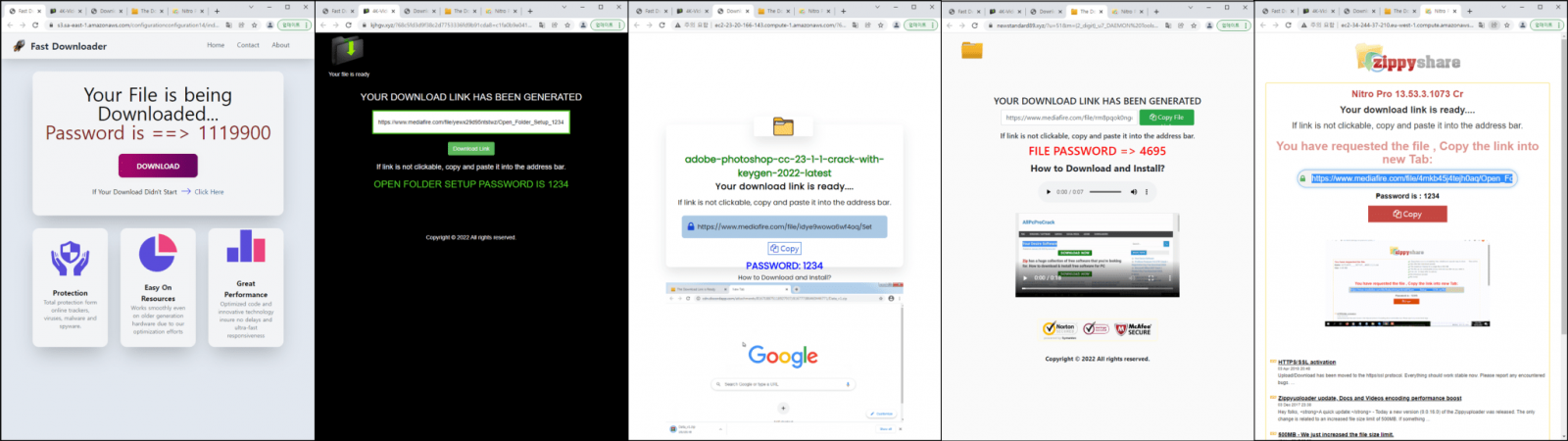
The malicious websites are constantly being refreshed, so there’s a wide variety of ever-shifting lures to draw users onto the malware distribution sites.
Visitors of these sites are taken through a series of redirections before they end up on the delivery page, so the landing page could be on a compromised legitimate site abused for SEO poisoning attacks.
We have seen the same malware operators using fake VPN sites to deliver CryptBot to victims in previous years, so search engine abuse isn’t a new trick.
Also Read: 5 Brief Concepts Between Data Protection Directive vs GDPR
Fresh samples of CryptBot indicate that its authors want to simplify its functionality and make the malware lighter, leaner, and less likely to be detected.
In this context, the anti-sandbox routine has been removed, leaving only the anti-VM CPU core count check in the newest version.
Also, the redundant second C2 connection and second exfiltration folder were both removed, and the new variant only features a single info-stealing C2.
“The code shows that when sending files, the method of manually adding the sent file data to the header was changed to the method that uses simple API. user-agent value when sending was also modified,” explains ASEC’s report
“The previous version calls the function twice to send each to a different C2, but in the changed version, one C2 URL is hard-coded in the function.”
Another feature the CryptBot’s authors have scrapped is the screenshot function and the option of collecting data on TXT files on the desktop, which were too risky and perhaps easily detected during exfiltration.
On the other hand, the latest version of CryptBot brings some targeted additions and improvements that make it a lot more potent.
In previous versions, the malware could only successfully exfiltrate data when deployed against Chrome versions between 81 and 95.
This limitation arose from implementing a system that looked for user data in fixed file paths, and if the paths were different, the malware returned an error.

Now, it searches on all file paths, and if user data is found anywhere, it exfiltrates them regardless of the Chrome version.
Considering that Google rolled out chrome 96 in November 2021, CryptBot remained ineffective against most of its targets for roughly three months, so fixing this problem was well overdue for its operators.
As CryptBot primarily targets people searching for software cracks, warez, and other methods of defeating copyright protection, simply avoiding the downloading of these tools will prevent infection by this malware and many others.