KEEP IN TOUCH
Subscribe to our mailing list to get free tips on Data Protection and Cybersecurity updates weekly!







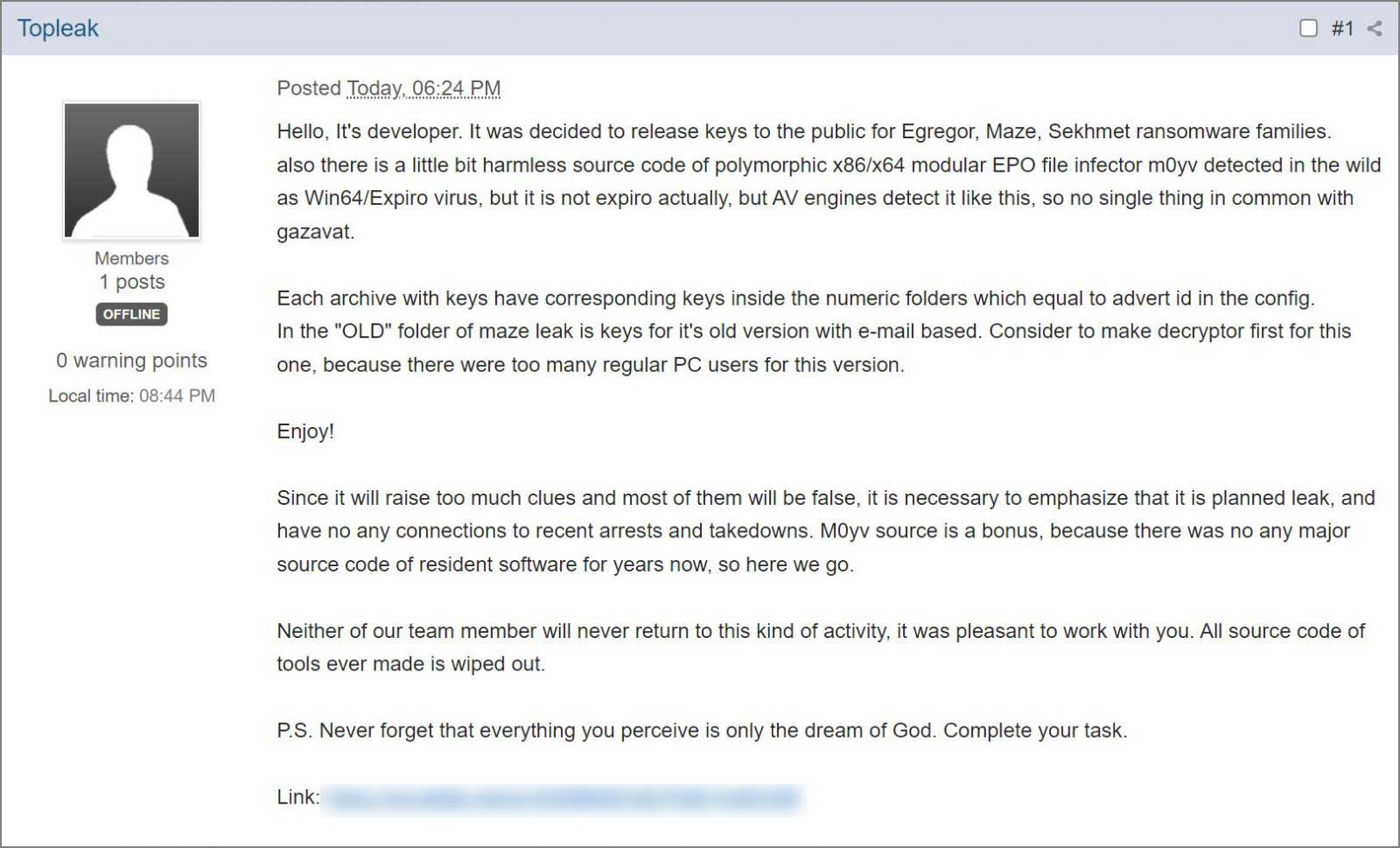
We saw the Maze ransomware developers reemerge briefly this week as they shared the master decryption keys for the Egregor, Maze, and Sekhmet ransomware operations.
After the Maze ransomware operation began shutting down in October 2020, it was always hoped that they would publicly release decryption keys to allow remaining victims to recover their files.
Tuesday night, almost fourteen months later, the alleged ransomware developer released the decryption keys in a BleepingComputer forum post.
While the developer says they had always planned to publish the keys, it is generally believed that they did it now as a gesture of goodwill due to the recent arrests and server seizures.
Using these keys, cybersecurity firm Emsisoft created a decryptor allowing victims to recover their files for free.
The other big news is the sentencing of a Netwalker ransomware affiliate from Canada, who obtained more than $27.6 million by attacking companies worldwide. After pleading guilty, the affiliate was sentenced to six years and eight months in prison.
This week’s other interesting ransomware news includes publishing LockBit 2.0 ransomware technical details by the FBI, a free decryptor for the TargetCompany ransomware, and Puma announcing a data breach due to the Kronos ransomware attack.
Also Read: This Educator Aims to Make Good Cyber Hygiene a Household Practice
Contributors and those who provided new ransomware information and stories this week include: @Seifreed, @billtoulas, @malwareforme, @VK_Intel, @BleepinComputer, @FourOctets, @DanielGallagher, @serghei, @malwrhunterteam, @jorntvdw, @fwosar, @Ionut_Ilascu, @PolarToffee, @LawrenceAbrams, @demonslay335, @struppigel, @chainalysis, @emsisoft, @Avast, @LadislavZezula, @coveware, @ddd1ms, @BrettCallow, @pcrisk, @USCERT_gov, and @CISAgov.
The Black Cat ransomware gang, also known as ALPHV, has confirmed they are former members of the notorious BlackMatter/DarkSide ransomware operation.
The Federal Bureau of Investigation (FBI) has released technical details and indicators of compromise associated with LockBit ransomware attacks in a new flash alert published this Friday.
The numerous law enforcement operations leading to the arrests and takedown of ransomware operations in 2021 have forced threat actors to narrow their targeting scope and maximize the efficiency of their operations.
Czech cybersecurity software firm Avast has released a decryption utility to help TargetCompany ransomware victims recover their files for free.
Sportswear manufacturer Puma was hit by a data breach following the ransomware attack that hit Kronos, one of its North American workforce management service providers, in December 2021.
PCrisk found new STOP ransomware variants that append the .cuag and .avyu extensions.
Also Read: The 5 Phases of Penetration Testing You Should Know
Sebastien Vachon-Desjardins, a Canadian man charged by the US for his involvement in NetWalker ransomware attacks, was sentenced to 6 years and 8 months in prison after pleading guilty before an Ontario judge to multiple offenses linked to attacks on 17 Canadian victims.
The master decryption keys for the Maze, Egregor, and Sekhmet ransomware operations were released last night on the BleepingComputer forums by the alleged malware developer.
Emsisoft created a decryptor allowing Maze, Sekhmet, and Egregor victims to recover their files for free.
PCrisk found a new Phobos ransomware variant that appends the .ZOZL extension.
In 2021, cybersecurity authorities in the United States,[1][2][3] Australia,[4] and the United Kingdom[5] observed an increase in sophisticated, high-impact ransomware incidents against critical infrastructure organizations globally. The Federal Bureau of Investigation (FBI), the Cybersecurity and Infrastructure Security Agency (CISA), and the National Security Agency (NSA) observed incidents involving ransomware against 14 of the 16 U.S. critical infrastructure sectors, including the Defense Industrial Base, Emergency Services, Food and Agriculture, Government Facilities, and Information Technology Sectors. The Australian Cyber Security Centre (ACSC) observed continued ransomware targeting of Australian critical infrastructure entities, including in the Healthcare and Medical, Financial Services and Markets, Higher Education and Research, and Energy Sectors. The United Kingdom’s National Cyber Security Centre (NCSC-UK) recognizes ransomware as the biggest cyber threat facing the United Kingdom. Education is one of the top UK sectors targeted by ransomware actors, but the NCSC-UK has also seen attacks targeting businesses, charities, the legal profession, and public services in the Local Government and Health Sectors.
Sure enough, we updated our ransomware numbers a few times throughout 2021, reflecting new payments we hadn’t identified previously. As of January 2022, we’ve now identified just over $692 million in 2020 ransomware payments — nearly double the amount we initially identified at the time of writing last year’s report.
One month later, there was good news: The Department of Justice announced that it had managed to seize $2.3 million worth of Bitcoin from Colonial’s ransom payment following an FBI investigation. Chainalysis is proud to say that our tools aided the FBI, and that we can now share details of how investigators tracked the funds following the attack.
Karsten Hahn found a .NET ransomware that impersonates REvil by copying the ransom note and Tor site.
PCrisk found new STOP ransomware variants that append the .iips and .ccps extensions.