KEEP IN TOUCH
Subscribe to our mailing list to get free tips on Data Protection and Cybersecurity updates weekly!







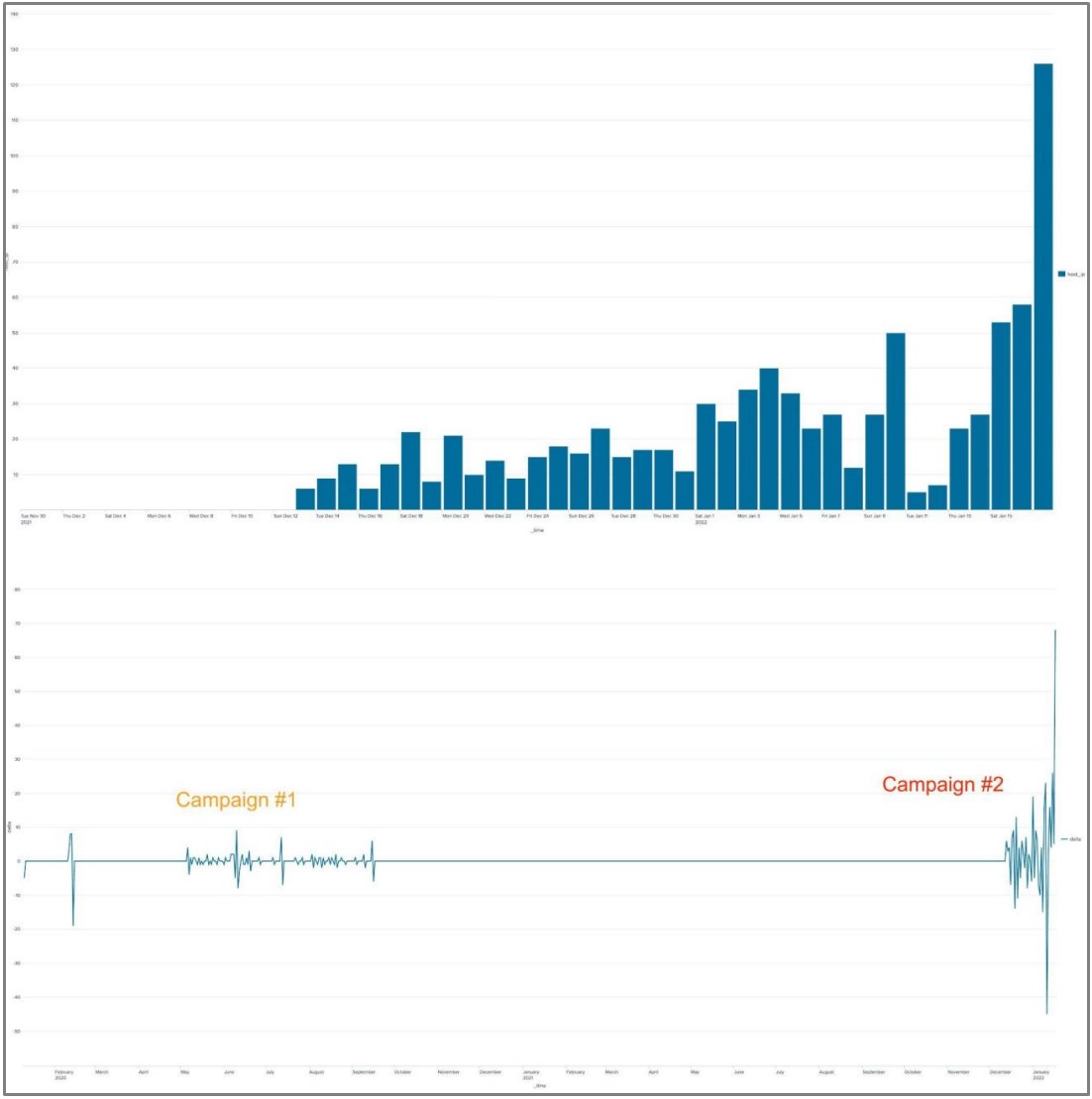
The FritzFrog botnet that’s been active for more than two years has resurfaced with an alarming infection rate, growing ten times in just a month of hitting healthcare, education, and government systems with an exposed SSH server.
Discovered in August 2020, the malware is written in Golang and is considered to be a sophisticated threat that relies on custom code, runs in memory, and is decentralized — peer-to-peer (P2P), so it does not need a central management server.
Researchers at internet security company Akamai spotted a new version of the FritzFrog malware, which comes with interesting new functions, like using the Tor proxy chain.
Also Read: A Closer Look: The Personal Information Protection Law in China
The new botnet variant also shows indications that its operators are preparing to add capabilities to target WordPress servers.
Akamai calls FritzFrog a “next-generation” botnet because it combines features that make it stand out from other threats in the same category.
The malware is better equipped to evade detection and keep a low profile due to using a “completely proprietary” P2P protocol for communications.
It relies on an extensive dictionary for brute-force attacks to find SSH credentials, which allows it to compromise a larger number of devices.
FritzFrog is constantly updating the list of targets and breached machines are constantly updated and its node distribution system ensures an equal number of targets to each node to keep the botnet balanced.
Also Read: Battling Cyber Threats in 4 Simple Ways
Akamai global network of sensors detected 24,000 attacks but the botnet claimed only 1,500 victims so far. Most of the infected hosts are in China, but among the compromised systems are in a European TV network, a Russian healthcare firm, and various universities in East Asia.
.jpg)
The actors have implemented a filtering list to skip low-powered devices such as Raspberry Pi boards, while the malware now contains code that lays the groundwork for targeting WordPress sites.
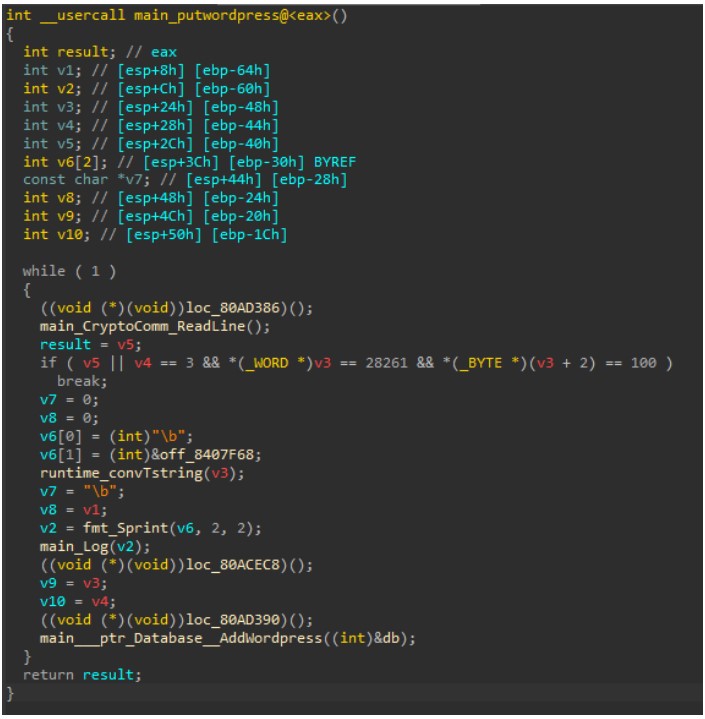
Considering that the botnet is known for cryptocurrency mining, this function is a curious addition. However, Akamai assumes that the actors have found other monetization avenues, such as deploying ransomware, or data leaks. Currently, this capability is inactive as it is being worked on.
The researchers note that FritzFrog is constantly under development, bugs being fixed on a daily basis, sometimes multiple times a day.
Another novelty in the latest FritzFrog sample is proxying outgoing SSH connections through Tor, obscuring the network structure and limiting the visibility from infected nodes to the botnet network. Although this feature looks complete, the developers have yet to activate it.
Finally, the copying system (used to infect new systems) is now based on SCP (security copy protocol), replacing the cat command present in the previous version.
At this time, the threat analysts at Akamai don’t have a definitive attribution for the operation of FritzFrog, but the evidence points to China.
Because the malware incorporates unique code components, some can be traced to unique GitHub repositories set up by Shanghai-based users.
Moreover, the wallet addresses linked to the second campaign’s mining operations were also used in the Mozi botnet, which was eventually confirmed to originate from China.
Finally, roughly 37% of all of FritzFrog’s active nodes are located in China, which may mean that the actor operates from there.
FritzFrog targets any device that exposes an SSH server, so admins of data center servers, cloud instances, and routers need to stay vigilant.
Akamai shares the following indicators of FritzFrog running on a system:
Akamai’s security recommendations are: