KEEP IN TOUCH
Subscribe to our mailing list to get free tips on Data Protection and Cybersecurity updates weekly!







The widespread malware known as Qbot (aka Qakbot or QuakBot) has recently returned to light-speed attacks, and according to analysts, it only takes around 30 minutes to steal sensitive data after the initial infection.
According to a new report by DFIR, Qbot was performing these quick data-snatching strikes back in October 2021, and it now appears that the threat actors behind it have returned to similar tactics.
More specifically, the analysts report that it takes half an hour for the adversaries to steal browser data and emails from Outlook and 50 minutes before they jump to an adjacent workstation.
Also Read: How often should you pen test?
As shown in the following diagram, Qbot moves quickly to perform privilege escalation immediately following an infection, while a full-fledged reconnaissance scan takes place within ten minutes.
.jpg)
The initial access is typically achieved via an Excel (XLS) document that uses a macro to drop the DLL loader on the target machine.
This payload then executes to create a scheduled task via the msra.exe process and elevates itself to system privileges.
Additionally, the malware adds the Qbot DLL to Microsoft Defender’s exclusion list, so it won’t be detected when injection into msra.exe happens.
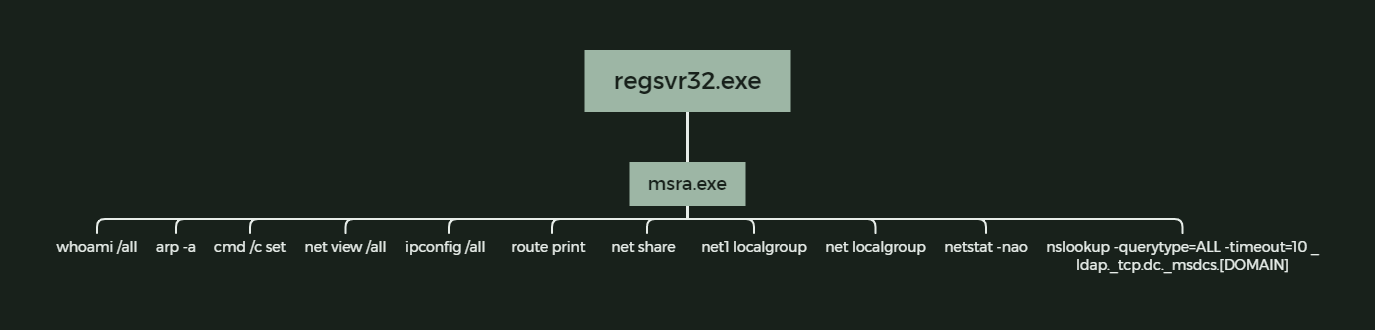
The malware steals emails in half an hour after the initial execution, which are then used for replay-chain phishing attacks and to be sold to other threat actors.
Also Read: What is a data protection officer? Through the lens of a Master DPO
Qbot steals Windows credentials from memory using the LSASS (Local Security Authority Server Service) injections and from web browsers. These are leveraged for lateral movement to other devices on the network, initiated at an average of fifty minutes after first execution.
.jpg)
Qbot moves laterally to all workstations in the scanned environment by copying a DLL to the next target and remotely creating a service to execute it.
At the same time, the previous infection is cleared, so the machine that just had its credentials exfiltrated is disinfected and appears normal.
Moreover, the services created on the new workstations have the ‘DeleteFlag’ parameter, which causes them to be removed upon system reboot.
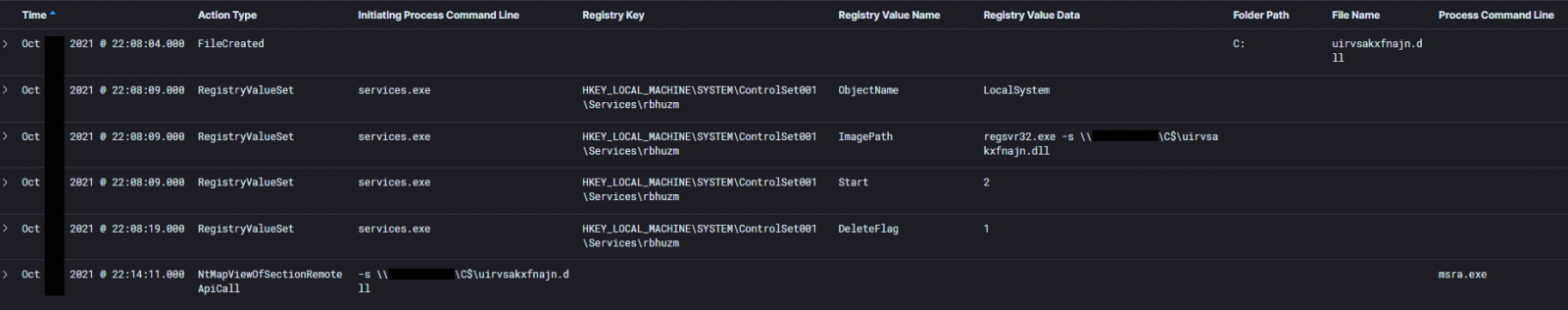
The lateral movement takes place rapidly, so if there’s no network segmentation to protect the workstations, the situation becomes very challenging for defense teams.
Also, the Qbot threat actors often like to use some of the compromised systems as first-tier proxy points for easy address masking and rotation, and use multiple ports for SSL communication with the C2 server.
The impact of these expeditious attacks isn’t limited to data loss, as Qbot has also been observed to drop ransomware payloads onto compromised corporate networks.
A Microsoft report from December 2021 captured the versatility of Qbot attacks, making it harder to evaluate the scope of its infections accurately.
However, no matter how a Qbot infection unfolds precisely, it is essential to keep in mind that almost all begin with an email, so this is the main access point that organizations need to strengthen.
Today’s announcement by Microsoft that they will be blocking macros in downloaded documents by default by removing the ‘Enable Content’ and ‘Enable Editing’ buttons will go a long way to protecting users from Qbot phishing attacks.