KEEP IN TOUCH
Subscribe to our mailing list to get free tips on Data Protection and Cybersecurity updates weekly!







Microsoft announced today that it will make it difficult to enable VBA macros downloaded from the Internet in several Microsoft Office apps starting in early April, effectively killing a popular distribution method for malware.
Using VBA macros embedded in malicious Office documents is a very popular method to push a wide range of malware families in phishing attacks, including Emotet, TrickBot, Qbot, and Dridex.
“This change only affects Office on devices running Windows and only affects the following applications: Access, Excel, PowerPoint, Visio, and Word,” the Microsoft Office Product Group said today.
Also Read: The Data Protection Act of Singapore and how it affects businesses
“The change will begin rolling out in Version 2203, starting with Current Channel (Preview) in early April 2022.”
After this change rolls out, Office users will no longer be able to enable macros with a click of a button after they’re automatically blocked.
This will automatically thwart attacks that deliver malware on home and enterprise networks via malicious Office docs, including various information-stealing trojans and malicious tools used by ransomware gangs.
Now, until the new autoblock defaults go into effect, when Office opens a document, it checks if it is tagged with a “Mark of the Web” (MoTW), which means it was downloaded from the Internet.
If this tag is found, Microsoft opens the document in read-only mode, blocking the exploit unless users click on the ‘Enable Editing’ or ‘Enable Content’ button shown at the top of the document.
By removing these buttons, which allow users to remove the MoTW, and blocking macros from untrusted sources by default, most malicious documents will no longer be executed, stopping malware attacks abusing this weakness in their tracks.
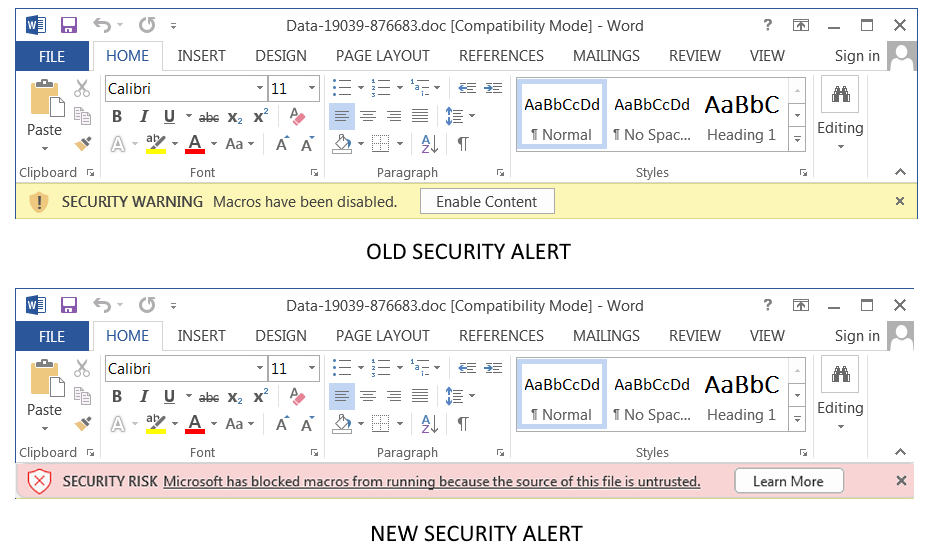
“SECURITY RISK: Microsoft has blocked macros from running because the source of this file is untrusted,” reads the new warning.
Also Read: What is cybersecurity? 5 best cybersecurity practices to follow
According to Microsoft, this significant security improvement will roll out to other Office update channels such as Current Channel, Monthly Enterprise Channel, and Semi-Annual Enterprise Channel at a later date.
This update will also be pushed to Office LTSC, Office 2021, Office 2019, Office 2016, and Office 2013 users at a future date.
“We will continue to adjust our user experience for macros, as we’ve done here, to make it more difficult to trick users into running malicious code via social engineering while maintaining a path for legitimate macros to be enabled where appropriate via Trusted Publishers and/or Trusted Locations,” said Tristan Davis, a Partner Group Program Manager for Microsoft’s Office Platform.
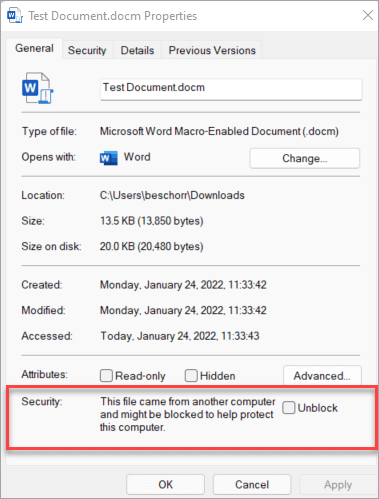
After the Office update rolls out and blocks one-click enabling macros in documents downloaded from the Internet, you will still be able to enable them by going into the documents’ properties and checking the “Unlock” button on the bottom right.
You can find more info on the security risk behind macros, safe practices to thwart phishing and malware attacks, as well as instructions on how to enable these macros if you’re sure they’re safe on this support page.
Last month, Microsoft also said Excel 4.0 (XLM) macros will be disabled by default to protect customers from malicious documents designed to infect them with malware.
That change was first announced in October when Redmond first revealed that it would disable XLM macros in all tenants if the users or the admins hadn’t manually toggled the feature on or off.