KEEP IN TOUCH
Subscribe to our mailing list to get free tips on Data Protection and Cybersecurity updates weekly!







The Federal Bureau of Investigation (FBI) has released technical details and indicators of compromise associated with LockBit ransomware attacks in a new flash alert published this Friday.
It also provided information to help organizations block this adversary’s attempts to breach their networks and asked victims to urgently report such incidents to their local FBI Cyber Squad.
The LockBit ransomware gang has been very active since September 2019 when it launched as a ransomware-as-a-service (RaaS), with gang representatives promoting the operation, providing support on Russian-language hacking forums, and recruiting threat actors to breach and encrypt networks.
Two years later, in June 2021, LockBit announced the LockBit 2.0 RaaS on their data leak site after ransomware actors were banned from posting on cybercrime forums [1, 2].
Also Read: PDPC Data Intermediary: Guidelines for businesses to know
With the relaunch, the ransomware gang redesigned Tor sites and overhauled the malware, adding more advanced features, including the automatic encryption of devices across Windows domains via Active Directory group policies.
The gang is now also trying to remove the intermediaries by recruiting insiders to provide them with access to corporate networks via Virtual Private Network (VPN) and Remote Desktop Protocol (RDP).
In January, it was discovered that LockBit also added a Linux encryptor targeting VMware ESXi servers to its toolkit.
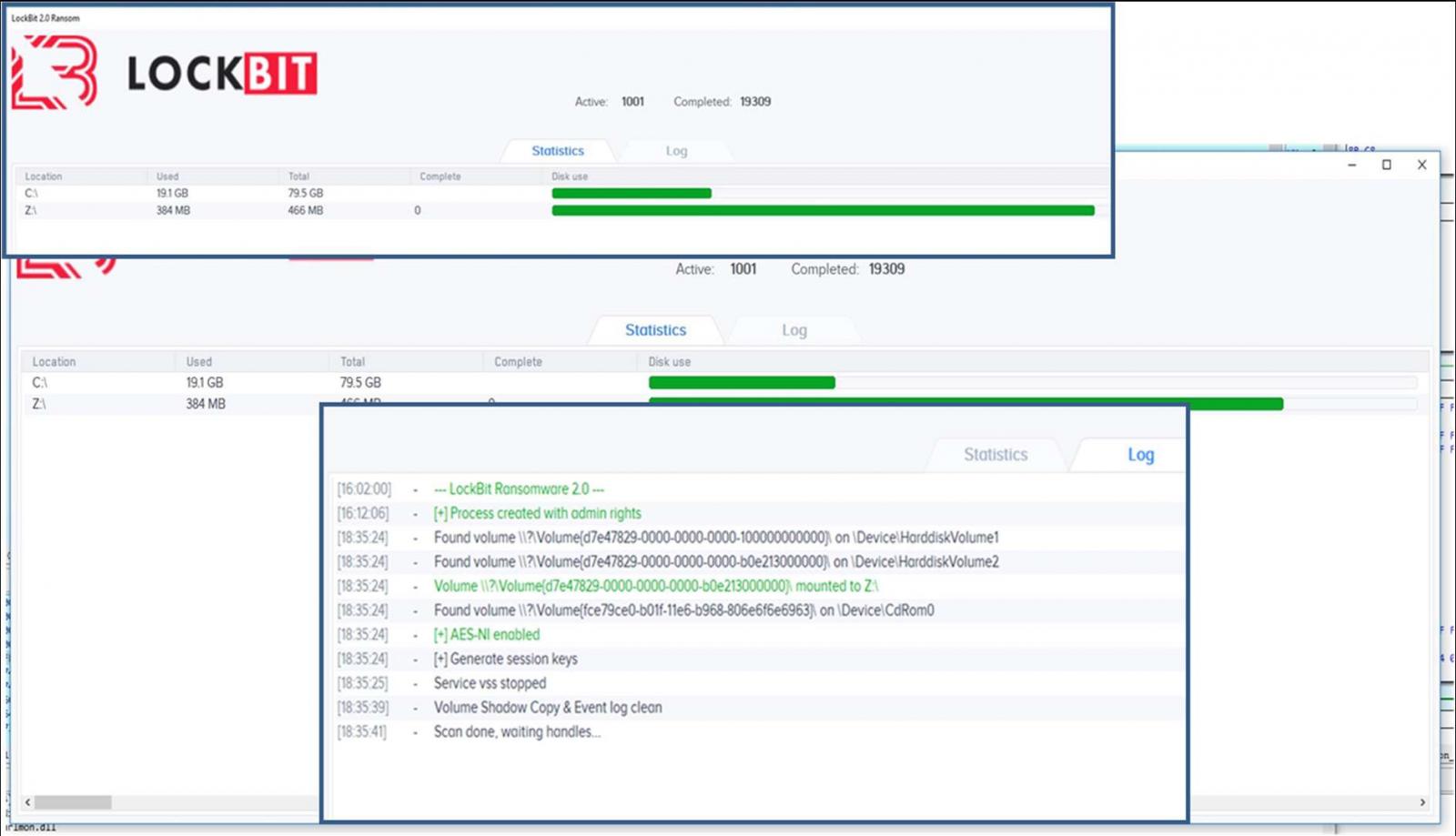
Among the technical details on how LockBit ransomware works, the FBI also revealed that the malware comes with a hidden debug window that can be activated during the infection process using the SHIFT + F1 keyboard shortcut.
Once it shows up, it can be used to view real-time information on the encryption process and trach the status of user data destruction.
This week’s advisory follows an alert issued by the Australian cybersecurity agency in August 2021 warning of quickly escalating LockBit ransomware attacks.
Days later, Accenture, a Fortune 500 company and one of the world’s largest IT services and consulting firms, confirmed to BleepingComputer that it was breached after LockBit threatened to leak data stolen from its network and asked for a $50 million ransom.
Two months later, Accenture also disclosed a data breach in October SEC filings after “extraction of proprietary information” during the August attack.
While the FBI didn’t say what prompted this flash alert, it did ask admins and cybersecurity professionals to share information on LockBit attacks targeting their companies’ networks.
Also Read: 10 Biggest cybersecurity trends in 2022 that businesses should know
“The FBI is seeking any information that can be shared, [including] boundary logs showing communication to and from foreign IP addresses, a sample ransom note, communications with the threat actors, Bitcoin wallet information, the decryptor file, and/or a benign sample of an encrypted file,” the federal agency said.
“The FBI encourages recipients of this document to report information concerning suspicious or criminal activity to their local FBI field office.
“By reporting any related information to FBI Cyber Squads, you are assisting in sharing information that allows the FBI to track malicious actors and coordinate with private industry and the United States Government to prevent future intrusions and attacks.”
The FBI also provides mitigations that would help defenders guard their networks against LockBit ransomware attack attempts:
Admins can also hinder ransomware operators’ network discovery efforts by taking these measures:
The FBI also added that it does not encourage paying ransoms and advises companies against it since it’s not guaranteed that paying will protect them from future attacks or data leaks.
Moreover, giving into ransomware gangs’ demands further finances their operations and motivates them to target more victims. It also incentivizes other cybercrime groups to join them in conducting illegal activities.
Despite this, the FBI acknowledged that a ransomware attack’s fallout might force companies to consider paying ransoms to protect shareholders, customers, or employees. The law enforcement agency strongly recommends reporting such incidents to a local FBI field office.
Even after paying a ransom, the FBI still urges to promptly report ransomware incidents as it will provide critical info that would allow law enforcement to prevent future attacks by tracking ransomware attackers and holding them accountable for their actions.