KEEP IN TOUCH
Subscribe to our mailing list to get free tips on Data Protection and Cybersecurity updates weekly!







Cryptocurrency platform Wormhole has recovered upwards of $326 million stolen in this week’s crypto hack, thanks to a major bailout.
Being a cross-chain crypto platform, Wormhole allows users to transfer cryptocurrency across different blockchains, such as Ethereum, Solana, and Binance Smart Chain, among others.
It does this by locking the original token in a smart contract and then minting a “wrapped” version of the stored token that can be transferred to another blockchain.
Also Read: Free Guide For Appointing A Data Protection Officer (2020)
Wormhole has announced a successful recovery of all funds stolen in this week’s $326 million hack, and the crypto platform is back up.
Sharing a timeline of the incident, the company states a detailed incident report will follow:
On February 2nd, Wormhole had announced a temporary shut down of its crypto platform as it investigated an exploit on their network.
The same day, the company confirmed that Wormhole’s network had indeed been exploited for 120,000 wrapped Ethereums (wETH) and they were working on restoring the lost funds.
Blockchain analytics company, Elliptic had previously revealed that Wormhole attempted to offer the attacker a $10 million bug bounty—should the latter agree to return the stolen funds. But, the effort failed to reach fruition, with over $265 million worth of ETH still remaining in the attacker’s wallet, as seen by BleepingComputer today.
Granted, the company has now restored the lost Ethereum, the funds didn’t appear out of thin air.
Wormhole’s bailout from this loss was made possible by industry partner, Jump Crypto, part of the Jump Trading Group that also owns the venture capital (VC) firm, Jump Capital.
“[Jump Crypto] believes in a multichain future and that [Wormhole] is essential infrastructure,” says the company. “That’s why we replaced 120k ETH to make community members whole and support Wormhole now as it continues to develop.”
Also Read: Free PDPA Singapore Checklist 2020
Not much info has been given out by Wormhole just yet as to how attackers managed to steal the funds, or the nature of the vulnerability exploit.
Analysis of illicit transactions by renowned cryptocurrency security researcher Samczsun revealed that Wormhole wasn’t properly validating all input accounts on its platform.
This enabled attackers to spoof “guardian” signatures and mint 120,000 ETH on the Solana blockchain out of thin air. Out of these funds, attackers were able to bridge 93,750 back to Ethereum, according to the researcher.
Samczsun specifically pointed out the flaw existed in the ‘verify_signatures’ function which is designed to “take a set of signatures provided by the guardians and pack it into a `SignatureSet`.” But, the researcher explains, the function failed to conduct any of the verification checks.
Another researcher smartcontracts analyzed the GitHub commit history for the Wormhole open source project and revealedthat the code changes supposedly fixing the bug were pushed to the repository about nine hours before the hack took place:
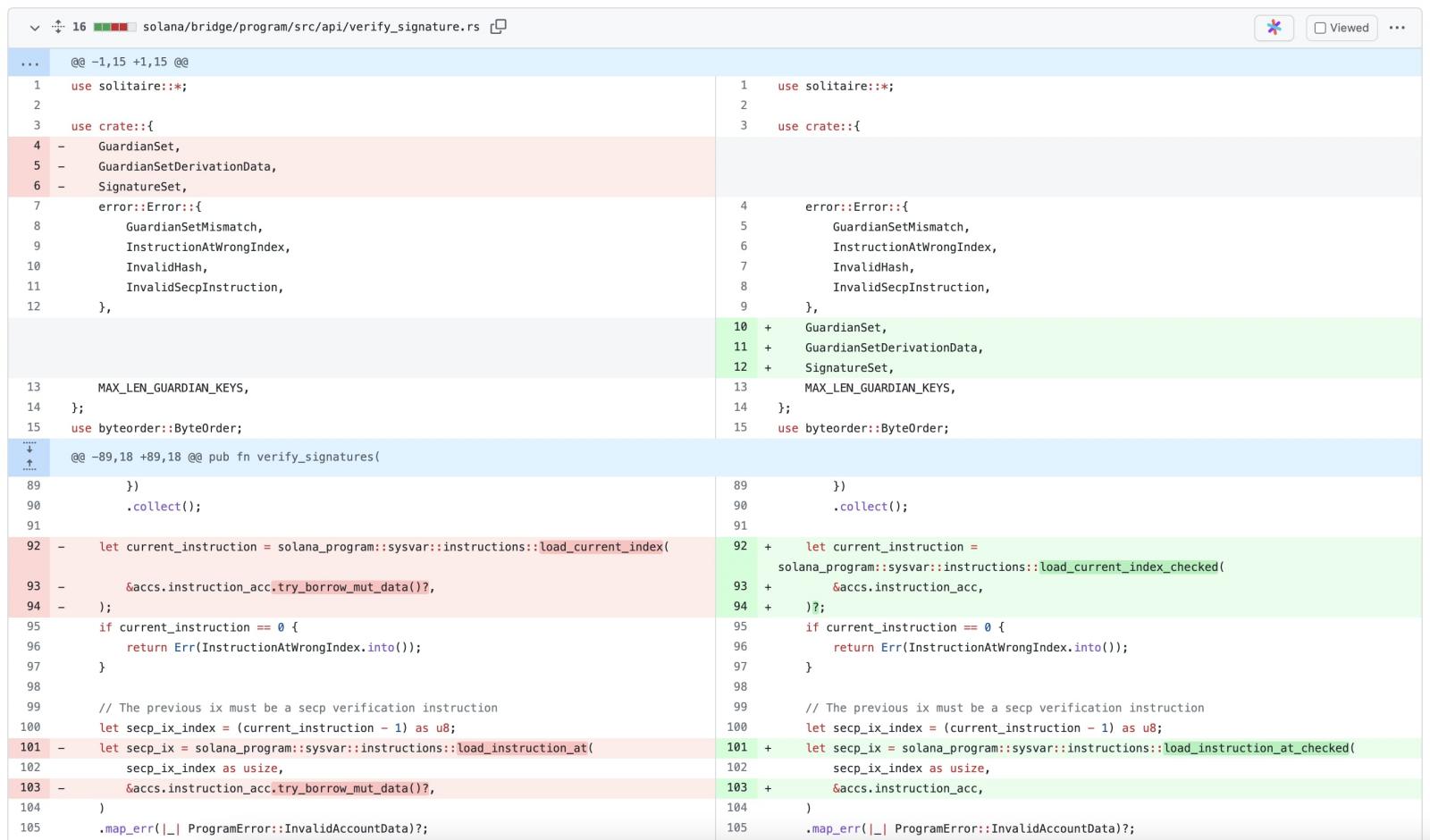
“Possible that an attacker was keeping an eye on the repository and looking out for suspicious commits,” says the researcher.
Interestingly, smartcontracts also concludes that the code change wasn’t a deliberate bug patch—it was likely rolled out inadvertently by Wormhole developers looking to simply bump up their Solana dependency version.
Public knowledge of pending security updates or outdated dependencies that are yet to be replaced (e.g. through a GitHub pull request) can give sharp-eyed adversaries a heads up, leading to exploitation of these flaws before they are patched.
In Wormhole’s case, the pull request to update the platform’s Solana version had been open since January 13th, as seen by BleepingComputer. But, the actual source code changes in GitHub took place on February 1st—hours before the attack on production systems.
In recent times, cryptocurrency exchanges and DeFi protocols have become popular targets of threat actors.
Last month, cryptocurrency exchange Crypto.com suffered a $34 million hack in which 483 of its customer accounts were affected. The same month DeFi platform Qubit Finance also faced an $80 million loss from a cyber attack.