KEEP IN TOUCH
Subscribe to our mailing list to get free tips on Data Protection and Cybersecurity updates weekly!







A cross-site scripting (XSS) Zimbra security vulnerability is actively exploited in attacks targeting European media and government organizations.
Zimbra is an email and collaboration platform that also includes instant messaging, contacts, video conferencing, file sharing, and cloud storage capabilities.
According to Zimbra, more than 200,000 businesses from over 140 countries are using its software, including over 1,000 government and financial organizations.
Also Read: How to Register Data Protection Officer (DPO) in ACRA Bizfile+
“At the time of writing, this exploit has no available patch, nor has it been assigned a CVE (i.e., this is a zero-day vulnerability),” the researchers said.
“Volexity can confirm and has tested that the most recent versions of Zimbra—8.8.15 P29 & P30—remain vulnerable; testing of version 9.0.0 indicates it is likely unaffected.”
Volexity says that so far, it only observed a single, previously unknown threat actor it tracks as TEMP_Heretic (believed to be Chinese) exploiting the zero-day in spear-phishing campaigns to steal emails.
However, the vulnerability can also enable attackers to perform other malicious actions “in the context of the user’s Zimbra webmail session,” including:
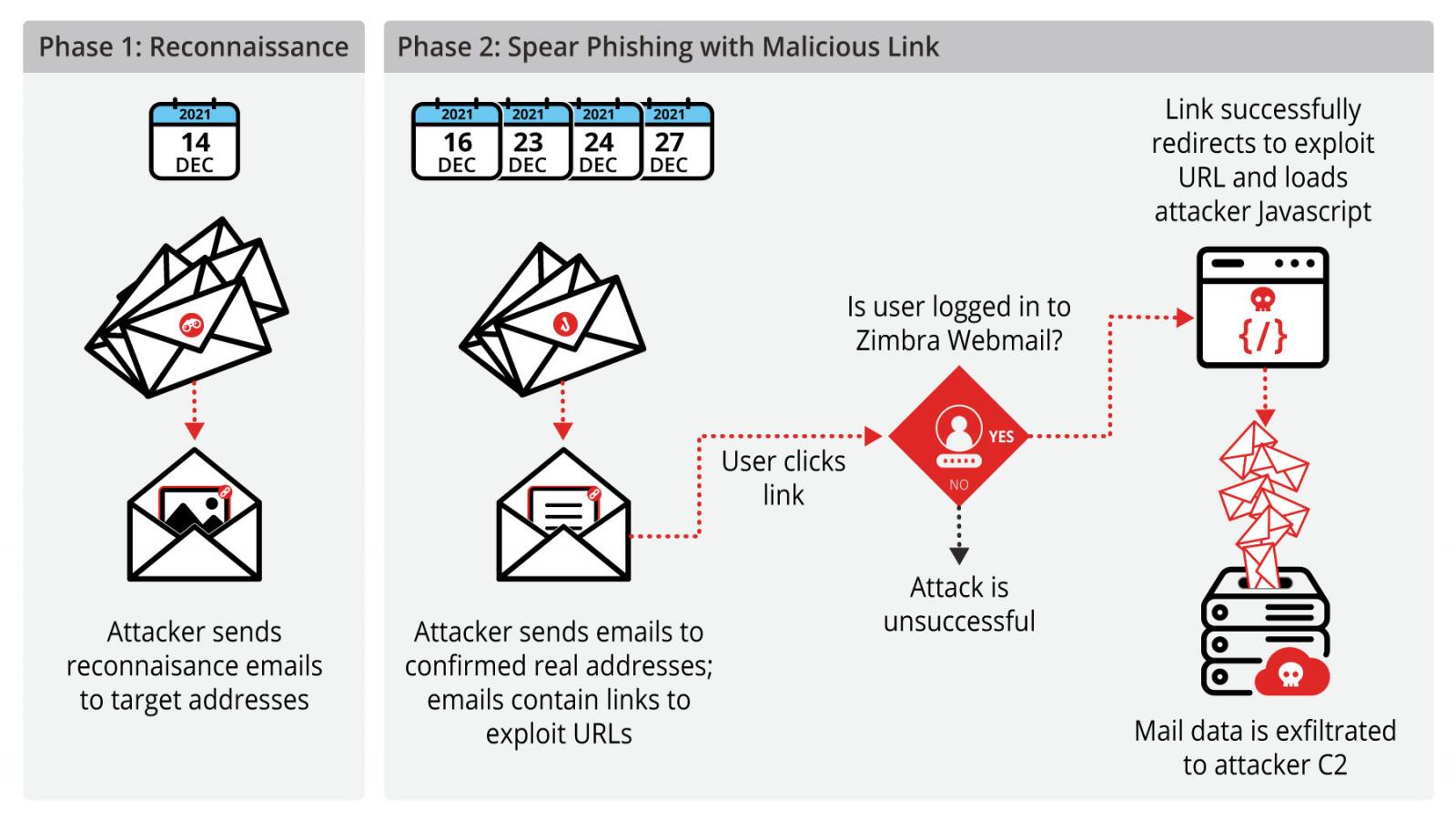
Since exploitation started in December, Volexity has seen TEMP_Heretic checking for live email addresses using reconnaissance emails with embedded remote images.
In the next attack stage, the threat actors sent spear-phishing emails with malicious links and various themes (e.g., interview requests, invitations to charity auctions, and holiday greetings) in multiple waves between December 16 and December 2021.
Also Read: Cost of GDPR Compliance for Singapore Companies
“Upon clicking the malicious link, the attacker infrastructure would attempt a redirect to a page on the targeted organization’s Zimbra webmail host, with a specific URI format which—if the user is logged in—exploits a vulnerability allowing an attacker to load arbitrary JavaScript in the context of a logged-in Zimbra session,” the researchers added.
The malicious code allowed the attackers to go through emails in the victims’ mailboxes and exfiltrate email contents and attachments to attacker-controlled servers.
“At the time of this writing, there is no official patch or workaround for this vulnerability. Volexity has notified Zimbra of the exploit and hopes a patch will be available soon,” the company said.
“Based on BinaryEdge data, approximately 33,000 servers are running the Zimbra email server, although the true number is likely to be higher.”
Volexity recommends taking the following measures to block attacks exploiting this zero-day:
A disclosure timeline and indicators of compromise (IoCs), including domains and IP addresses linked to the campaign (dubbed EmailThief), are available at the end of the report Volexity published today.
A Zimbra spokesperson was not available for comment when contacted by BleepingComputer earlier today.