KEEP IN TOUCH
Subscribe to our mailing list to get free tips on Data Protection and Cybersecurity updates weekly!







A new and powerful malware named ‘Mars Stealer’ has appeared in the wild, and appears to be a redesign of the Oski malware that shut down development abruptly in the summer of 2020.
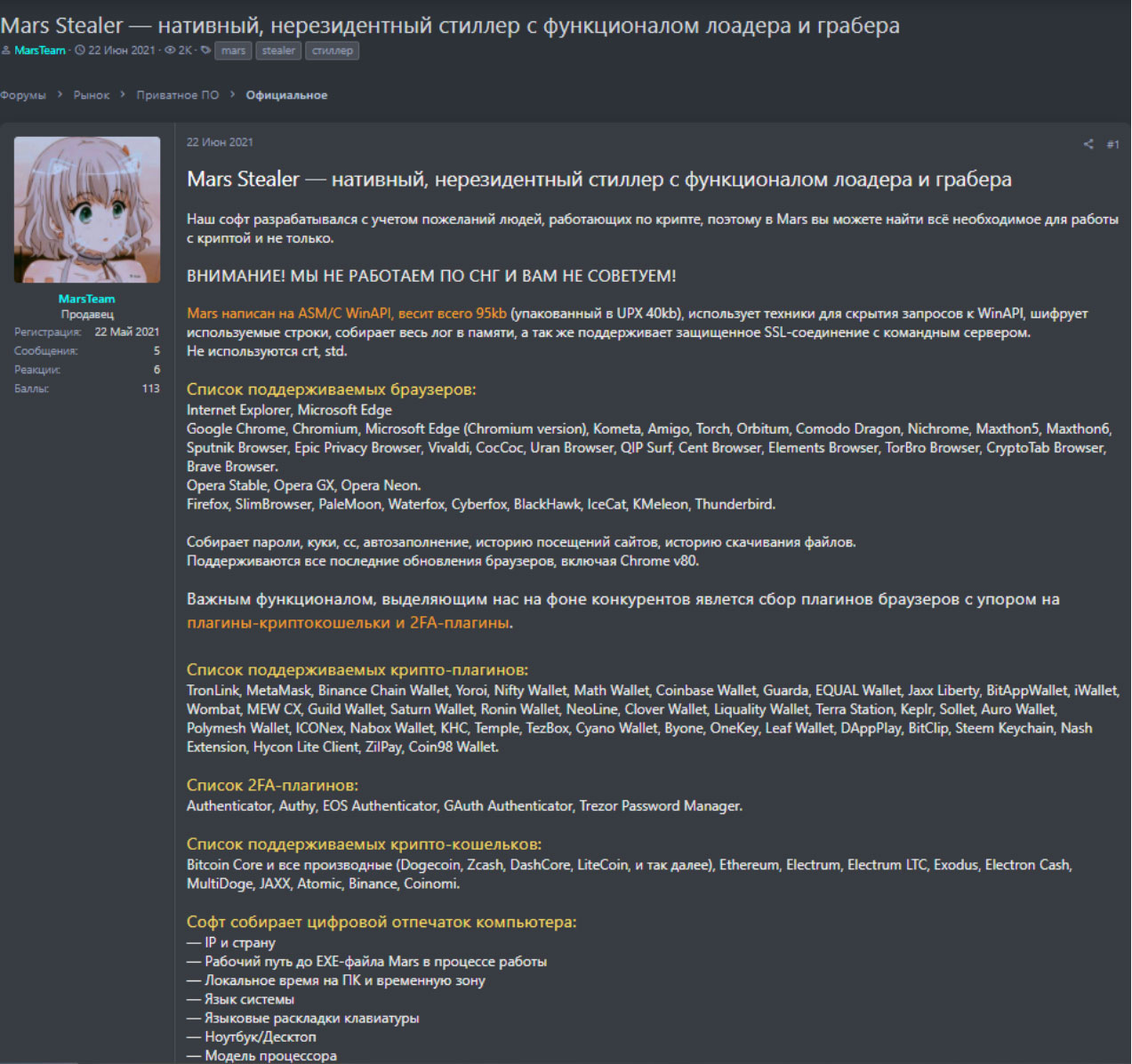
Mars Stealer is an information-stealing malware that steals data from all popular web browsers, two-factor authentication plugins, and multiple cryptocurrency extensions and wallets.
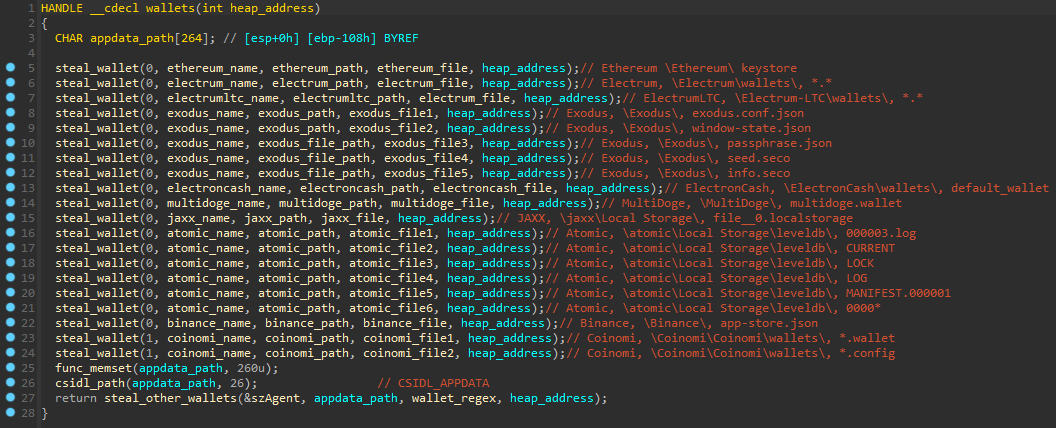
Additionally, the malware can exfiltrate files from the infected system and relies on its own loader and wiper, which minimizes the infection footprint.
Also Read: The 12 Important Details for Employment Contract Template
In July 2020, the developers behind the Oski information-stealing trojan suddenly shut down their operation after no longer responding to buyers and the closing of their Telegram channel.
Fast forward almost a year later, and a new information-stealing malware called ‘Mars Stealer’ began to be promoted on Russian-speaking hacking forums.
After security researcher @3xp0rt obtained a sample, the researcher discovered that the Mars Stealer is a redesigned version of Oski malware with enhanced functionality.
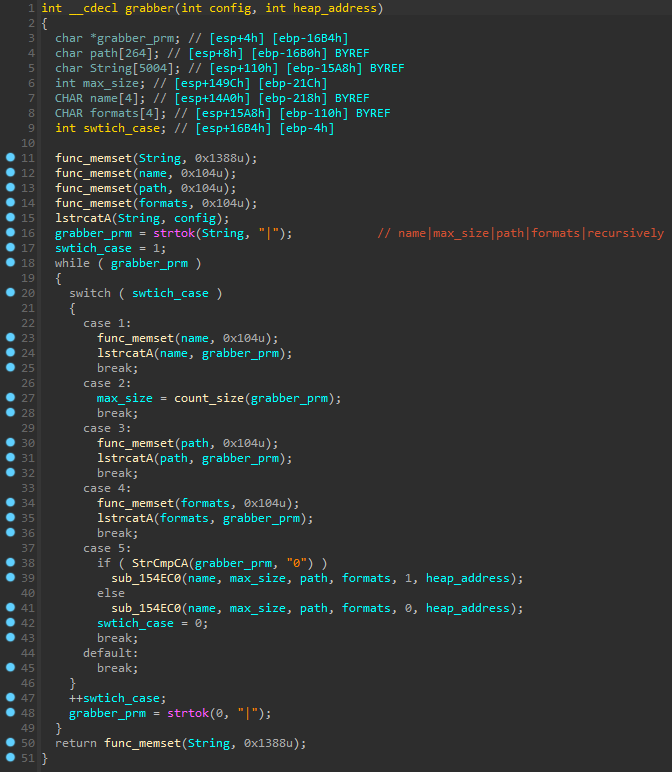
Mars Stealer uses a custom grabber that retrieves its configuration from the C2 and then proceeds to target the following applications:
Internet apps: Google Chrome, Internet Explorer, Microsoft Edge (Chromium Version), Kometa, Amigo, Torch, Orbitium, Comodo Dragon, Nichrome, Maxxthon5, Maxxthon6, Sputnik Browser, Epic Privacy Browser, Vivaldi, CocCoc, Uran Browser, QIP Surf, Cent Browser, Elements Browser, TorBro Browser, CryptoTab Browser, Brave, Opera Stable, Opera GX, Opera Neon, Firefox, SlimBrowser, PaleMoon, Waterfox, CyberFox, BlackHawk, IceCat, K-Meleon, Thunderbird.
2FA apps: Authenticator, Authy, EOS Authenticator, GAuth Authenticator, Trezor Password Manager.
Crypto extensions: TronLink, MetaMask, Binance Chain Wallet, Yoroi, Nifty Wallet, Math Wallet, Coinbase Wallet, Guarda, EQUAL Wallet, Jaox Liberty, BitAppWllet, iWallet, Wombat, MEW CX, Guild Wallet, Saturn Wallet, Ronin Wallet, Neoline, Clover Wallet, Liquality Wallet, Terra Station, Keplr, Sollet, Auro Wallet, Polymesh Wallet, ICONex, Nabox Wallet, KHC, Temple, TezBox Cyano Wallet, Byone, OneKey, Leaf Wallet, DAppPlay, BitClip, Steem Keychain, Nash Extension, Hycon Lite Client, ZilPay, Coin98 Wallet.
Crypto wallets: Bitcoin Core and all derivatives (Dogecoin, Zcash, DashCore, LiteCoin, etc), Ethereum, Electrum, Electrum LTC, Exodus, Electron Cash, MultiDoge, JAXX, Atomic, Binance, Coinomi.
Also Read: Is it Illegal to Email Someone Without Their Permission?
Moreover, Mars Stealer will capture and send the following basic information to the C2:
The only notable omission from the targeted application list is Outlook, which the malware authors will likely add in future releases.
Mars Stealer is a lean malware of just 95 KB in size, which attempts to evade security by using routines that hide API calls and string-encryption techniques using a combination of RC4 and Base64.
The information it collects is wrapped in memory, while all connections with the C2 are done with the SSL (Secure Sockets Layer) protocol, so they’re encrypted.
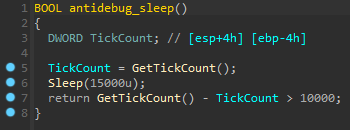
Moreover, the Mars Stealer code contains Sleep function intervals to perform timing checks that would result in a mismatch if a debugger is used.
Finally, the malware can remove itself after the user data has been exfiltrated or when the operator decides to wipe it.
Mars Stealer also checks if a user is based in countries historically part of the Commonwealth of Independent States, which is common for many Russian-based malware.
If the device’s language ID matches Russia, Belarus, Kazakhstan, Azerbaijan, Uzbekistan, and Kazakhstan, the program will exit without performing any malicious behavior.
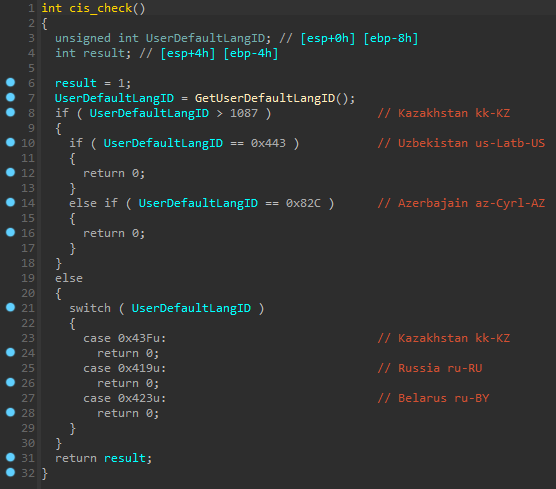
Moreover, the malware has to have a compilation date no older than a month than the system time; otherwise, it exits the execution process.
Currently, Mars Stealer is sold for $140 to $160 (extended version) on hacking forums, so it will likely get in the hands of numerous threat actors and be used in attacks in the future.