KEEP IN TOUCH
Subscribe to our mailing list to get free tips on Data Protection and Cybersecurity updates weekly!







The Iranian-backed MuddyWater hacking group is conducting a new malicious campaign targeting private Turkish organizations and governmental institutions.
This cyber-espionage group (aka Mercury, SeedWorm, and TEMP.Zagros) was linked this month to Iran’s Ministry of Intelligence and Security (MOIS) by the US Cyber Command (USCYBERCOM).
The hacking group has been attributed to attacks against entities in Central and Southwest Asia and numerous public and privately-held organizations from Europe, Asia, and North America in the telecommunications, government (IT services), oil, and airline industry sectors.
When conducting attacks, the threat actors use various file types like PDFs, XLS files, and Windows executables to deploy obfuscated PowerShell-based downloaders and gain initial access to targeted networks.
A new report by researchers at Cisco Talos links MuddyWater to recent attacks targeting Turkish private organizations and governmental agencies.
The attacks start with spear-phishing that uses files with Turkish language names and pretend to come from the country’s Health or Interior ministry.
Also Read: Unbelievable Facts About NRIC Check Digit Algorithm
As part of the attack, the MuddyWater threat actors use two infection chains that begin with delivering a PDF file. In the first case, the PDF features an embedded button that fetches an XLS file upon clicking it.
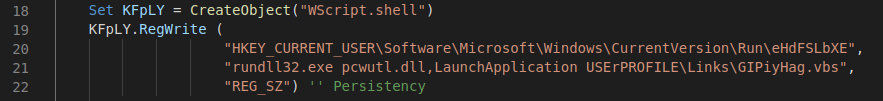
These files are typical XLS documents that carry malicious VBA macros which initiate the infection process and establish persistence by creating a new Registry key.
On the same stage, a VBScript is fetched with a PowerShell downloader and executed through a “living off the land” DLL to evade detection, retrieving the primary payload from the C2.
Also Read: Top 5 Importance Of Website Maintenance Singapore
.jpg)
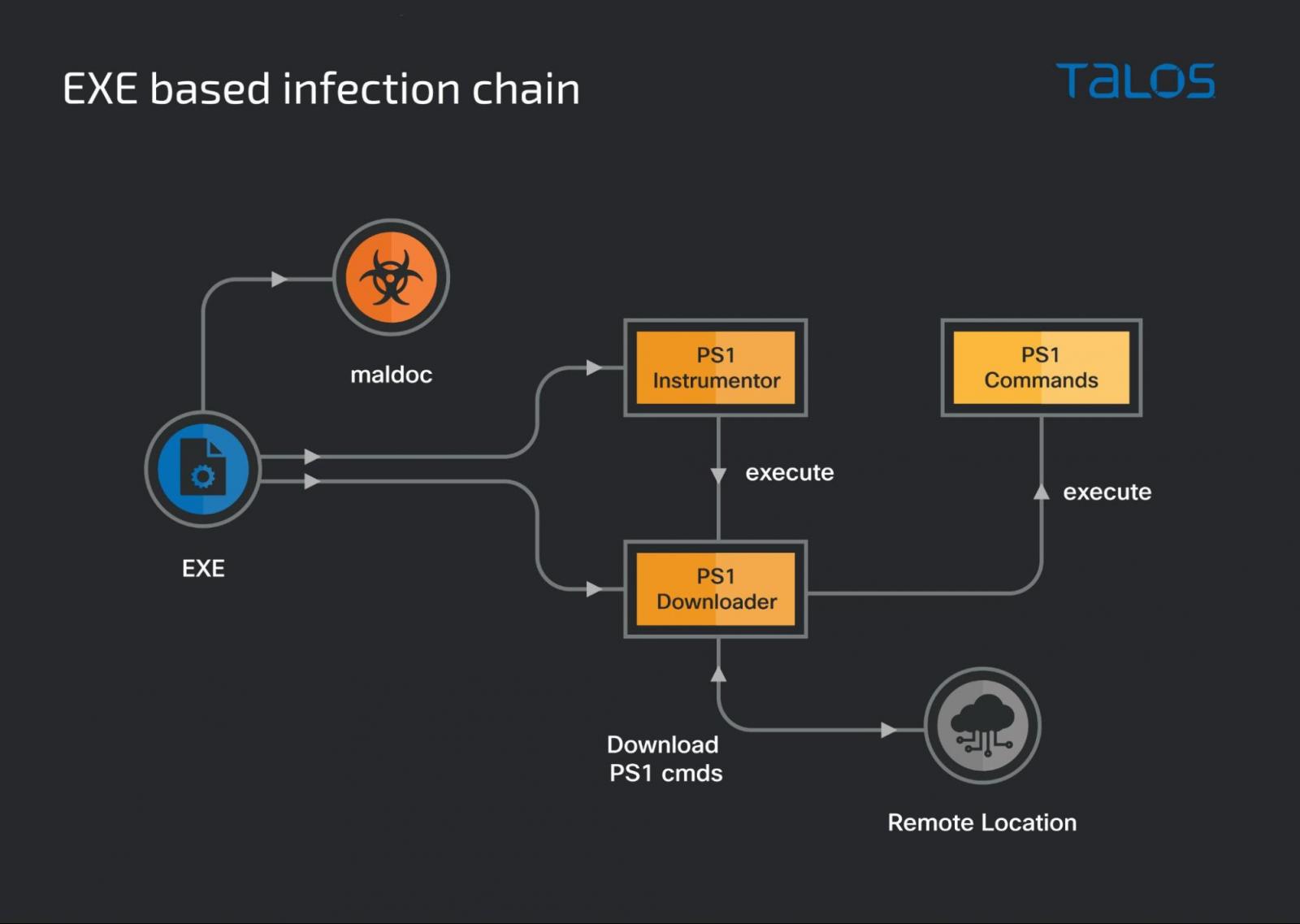
The second infection chain uses an EXE file instead of an XLS, but it still employs the PowerShell downloader, the intermediate VBScript, and adds a new registry entry for persistence.
One notable difference in this campaign compared to older ones is the use of canary tokens to track code executions and any subsequent infections on neighboring systems.
The token hides inside the malicious attachment or the email itself and alerts the threat actors when the victim opens the lure and executes the macro.
“The malicious VBA macros consisted of the same set of functionalities for creating the malicious VBS and PS1 scripts, and achieving persistence across reboots,” explains the Cisco Talos report.
“However, there was one interesting addition to the macro functionality now. The latest versions of the VBA code deployed could make HTTP requests to a canary token from canarytokens.com.”
These tokens can also be used as anti-analysis tools, providing timestamps to the actors and making it easy to identify research/analysis-induced inconsistencies.
Finally, if the token sends requests but the payload isn’t fetched, it’s an indication that the payload server is blocked, giving the actors valuable information on the situation and driving them to seek alternative delivery methods.
The researchers attribute these attacks to the MuddyWater group based on the observed technical indicators, tactics, procedures, and C2 infrastructure.
Notably, the Turkish authorities identified some of the C2 IP addresses used in this campaign from previous attacks and are listed in official threat advisories.
Cisco has additional strong evidence that points to Iranian actors in the form of code and metadata similarities and other indicators that they didn’t publish due to intelligence sharing sensitivities.