KEEP IN TOUCH
Subscribe to our mailing list to get free tips on Data Protection and Cybersecurity updates weekly!







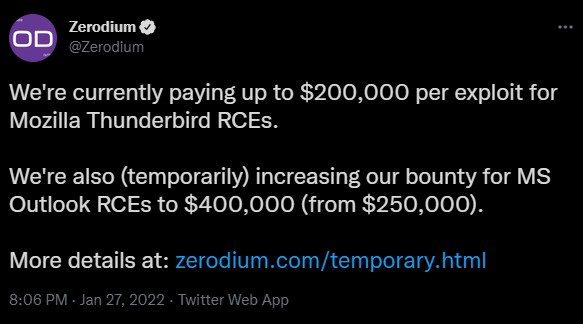
Exploit broker Zerodium has announced a pay jump to 400,000 for zero-day vulnerabilities that allow remote code execution (RCE) in Microsoft Outlook email client.
The new payout is not permanent, the company says in a short tweet, but the end date for submissions is still to be disclosed.
Also Read: How to Send Mass Email Without Showing Addresses: 2 Great Workarounds
Zerodium’s regular bounty for RCE vulnerability in Microsoft Outlook for windows is $250,000, expected to be “accompanied by a fully functional and reliable exploit.”
For $400,000, Zerodium is awaiting an exploit that achieves remote code execution without any interaction, the so-called ‘zero-click,’ when Microsoft’s email client is receiving or downloading messages.
“We are temporarily increasing our payout for Microsoft Outlook RCEs from $250,000 to $400,000. We are looking for zero-click exploits leading to remote code execution when receiving/downloading emails in Outlook, without requiring any user interaction such as reading the malicious email message or opening an attachment” – Zerodium
The company is not ruling out a bounty for exploits that require an email to be opened or read, although the submitter will get a lower, undisclosed payout.
Zerodium is also reminding that it currently offers up to $200,000 for exploits leading to remote code execution in Mozilla Thunderbird, the same amount offered since 2019.
The same conditions apply for the exploit payouts for Mozilla Thunderbird as in the case of Microsoft Outlook. An RCE in an email client would grant attackers access to all available accounts.
While the company did not specify an end date for submitting zero-click Microsoft Outlook exploits, the period may be quite long.
Also Read: CCTV Law Singapore Edition: Know Your Rights and Responsibilities
On March 31, 2021, Zerodium announced that it was temporarily tripling the bounty for WordPress RCE exploits and the offer still stands today.
The regular payout for an exploit in the most popular open-source content management system (CMS) is $100.000.
At the moment, only WordPress, Mozilla Thunderbird, and Microsoft Outlook are listed as active on the page with temporarily increased bounties.
Recently expired temporary offers are for RCE and sandbox escape in Google Chrome (both up to $400,000), and RCE in VMware vCenter server (up to $150,000).