KEEP IN TOUCH
Subscribe to our mailing list to get free tips on Data Protection and Cybersecurity updates weekly!







The WordPress WP HTML Mail plugin, installed in over 20,000 sites, is vulnerable to a high-severity flaw that can lead to code injection and the distribution of convincing phishing emails.
‘WP HTML Mail’ is a plugin used for designing custom emails, contact form notifications, and generally tailored messages that online platforms send to their audience.
The plugin is compatible with WooCommerce, Ninja Forms, BuddyPress, and others. While the number of sites using it isn’t large, many have a large audience, allowing the flaw to affect a significant number of Internet users.
Also Read: 4 Reasons to Outsource Penetration Testing Services
According to a report by Wordfence’s Threat Intelligence team, an unauthenticated actor could leverage the flaw tracked as “CVE-2022-0218” to modify the email template to contain arbitrary data of the attacker’s choosing.
Additionally, threat actors can use the same vulnerability to send phishing emails to anyone registered on the compromised sites.
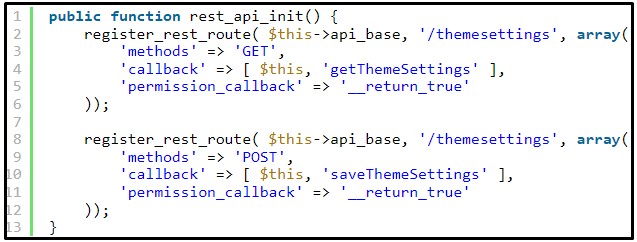
The problem lies in the plugin’s registration of two REST-API routes used to retrieve and update email template settings.
These API endpoints aren’t adequately protected from unauthorized access, so even unauthenticated users can call and execute the functions.
As Wordfence explains in detail in its report:
The plugin registers the /themesettings endpoint, which calls the saveThemeSettings function or the getThemeSettings function depending on the request method.
The REST-API endpoint did use the permission_callback function, however, it was set to __return_true which meant that no authentication was required to execute the functions.
Therefore, any user had access to execute the REST-API endpoint to save the email’s theme settings or retrieve the email’s theme settings.
Apart from the possibility of phishing attacks, an adversary could also inject malicious JavaScript into the mail template, which would execute anytime the site administrator accessed the HTML mail editor.
This could potentially open the way to adding new admin accounts, redirect the site’s visitors to phishing sites, inject backdoors into the theme files, and even complete site takeover.
Also Read: Vulnerability Assessment vs Penetration Testing: And Why You Need Both
Wordfence discovered and disclosed the vulnerability to the plugin’s developer on December 23, 2021, but they only got a response on January 10, 2022.
The security update that addressed the vulnerability came on January 13, 2022, with the release of version 3.1.
As such, all WordPress site owners and administrators are advised to verify that they’re running the latest version of the ‘WP HTML Mail’ plugin.