KEEP IN TOUCH
Subscribe to our mailing list to get free tips on Data Protection and Cybersecurity updates weekly!






Security analysts have discovered and linked MoonBounce, “the most advanced” UEFI firmware implant found in the wild so far, to the Chinese-speaking APT41 hacker group (also known as Winnti).
APT41 is a notorious hacking group that has been active for at least a decade and is primarily known for its stealthy cyber-espionage operations against high-profile organizations from various industry sectors.
The discovery of MoonBounce is the work of researchers at Kaspersky, who have published a detailed technical report on their findings.
Also Read: Got A Notice of Data Breach? Don’t Panic!
UEFI (Unified Extensible Firmware Interface) is a technical specification that helps interface operating system (OS) and firmware software in computer systems.
Being able to plant malicious code called “UEFI bootkit,” in the firmware is an excellent way to remain hidden from AVs and any security tools running on the OS level.
This has been done multiple times before, with two recent examples being the FinFisher malware and the ESPecter backdoor.
Generally, these tools hijack the booting sequence and initialize before the OS security components. They are very persistent because they nest in areas that can’t be erased, like a reserved space on the disk.
In the case of MoonBounce, the implanting location is on the SPI flash memory of the motherboard, so not even a hard disk replacement can uproot it.
The laced firmware component is CORE_DXE, which is called during the early phase of the UEFI boot sequence.
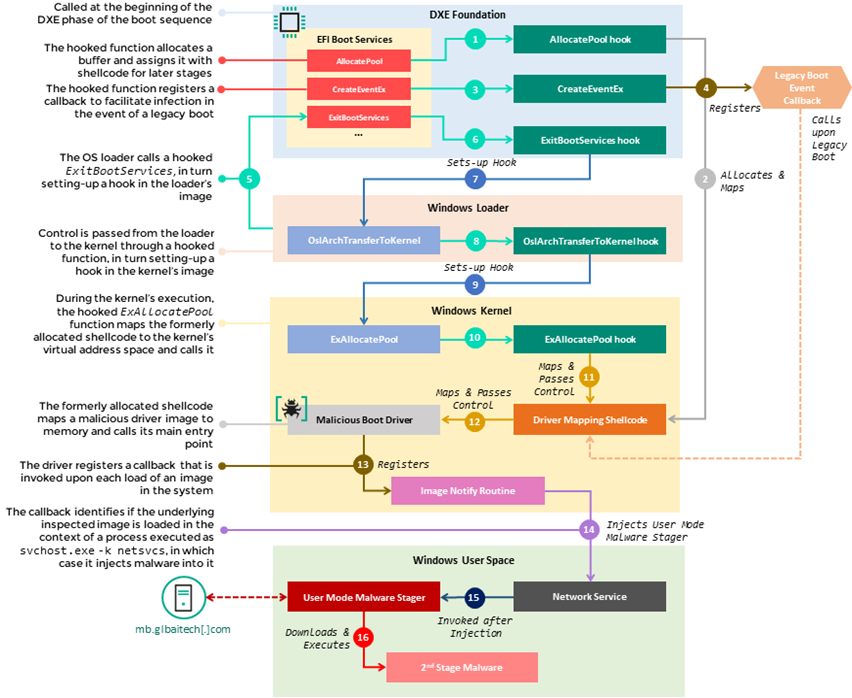
“The source of the infection starts with a set of hooks that intercept the execution of several functions in the EFI Boot Services Table, namely AllocatePool, CreateEventEx, and ExitBootServices,” explains Kaspersky in the report.
Also Read: A Review of PDPC Undertakings July 2021 Cases
“Those hooks are used to divert the flow of these functions to malicious shellcode that is appended by the attackers to the CORE_DXE image, which in turn sets up additional hooks in subsequent components of the boot chain, namely the Windows loader.”
“This multistage chain of hooks facilitates the propagation of malicious code from the CORE_DXE image to other boot components during system startup, allowing the introduction of a malicious driver to the memory address space of the Windows kernel.”
This driver runs during the OS kernel initiation and injects the malware into an svchost.exe process. The malware has fully initialized as soon as the computer is up and running.
Next, it communicates to a hardcoded C2 URL address and attempts to fetch the next stage payload, which will run in memory.
Kaspersky couldn’t retrieve that payload for analysis or figure out how exactly the actors infected the UEFI firmware in the first place.
The telemetry data reveals that these attacks were highly targeted, and Kaspersky only detected the firmware rootkit in a single case.
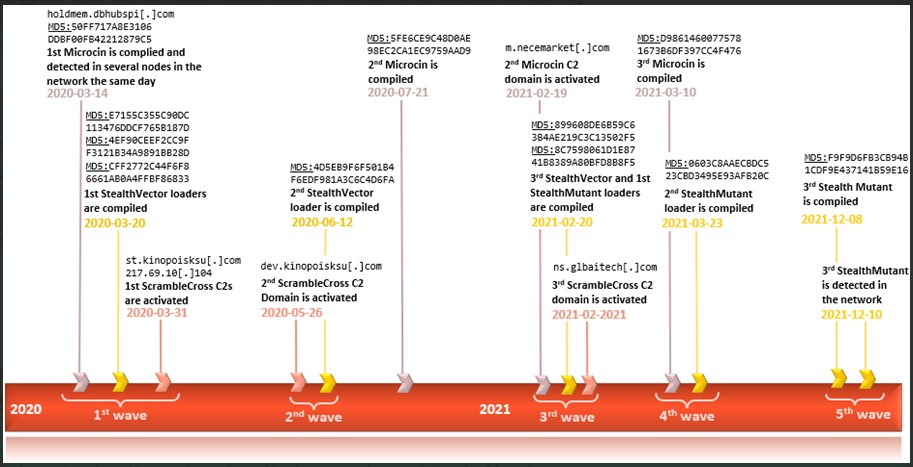
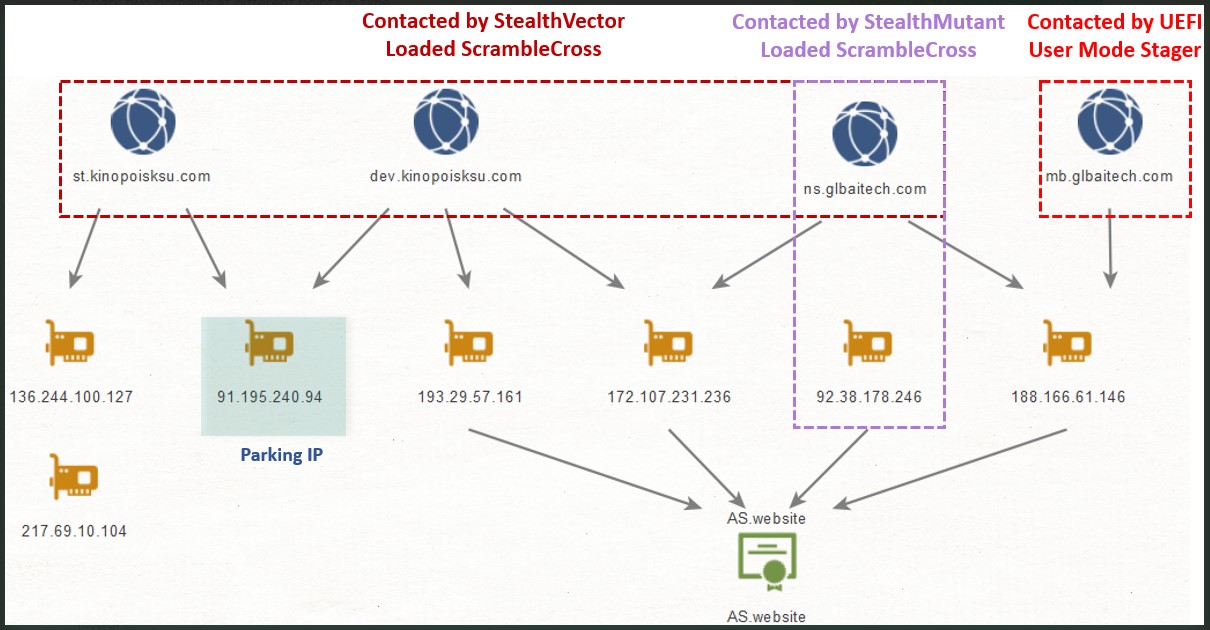
However, Kaspersky found multiple malware samples and loaders in other machines in the same network, but those were non-UEFI implants.
Examples include the Microcin backdoor, the Mimikat credential stealer, the Go implant, the StealthMutant loader, and the ScrambleCross malware.
As for who was targeted, the security firm mentions an organization in control of several enterprises dealing with transportation technology.
The adversaries’ main goal was to establish a lengthy foothold within the network and conduct cyber-espionage by exfiltrating valuable data to the C2 server.
In this context, the APT41 operators performed analytical network reconnaissance and moved laterally where possible while at the same time wiping traces of their malicious activity.
Kaspersky found plenty of evidence linking MoonBounce to APT41, ranging from the deployment of the ScrambleCross malware itself to unique certificates retrieved from its C2 servers which match previous FBI reports on APT41 activity.
While the U.S. Department of Justice identified and charged five APT41 members in September 2020, the existence of MoonBounce and the operation around it proves the threat actors weren’t discouraged by the legal pressure.
APT41 remains a sophisticated threat actor who can develop evasive tools that bypass even the most impenetrable corporate networks.
With UEFI threats now getting more traction, Kaspersky advises potential to take the following measures to defend against attackers using MoonBounce or similar malware: