KEEP IN TOUCH
Subscribe to our mailing list to get free tips on Data Protection and Cybersecurity updates weekly!







Hackers believed to work for the North Korean government have compromised the email account of a staff member of Russia’s Ministry of Foreign Affairs (MID) and deployed spear-phishing attacks against the country’s diplomats in other regions.
One of the targets was Sergey Alexeyevich Ryabko, the deputy foreign minister for the Russian Federation, among other things responsible for bilateral relations with North and South America.
The phishing campaign started since at least October 19, 2021, deploying Konni malware, a remote administration tool (RAT) associated with the cyber activity from North Korean hackers known as APT37 (or StarCruft, Group123, Operation Erebus, and Operation Daybreak).
Also Read: Top 25 Data Protection Statistics That You Must Be Informed
Cybersecurity firm Cluster25 last week published research about a phishing campaign towards the end of December 2021 that delivered Konni RAT to individuals in the Russian diplomatic apparatus.
The researchers found that the hackers used the New Year theme as a decoy in emails to staff at the Russian embassy in Indonesia.
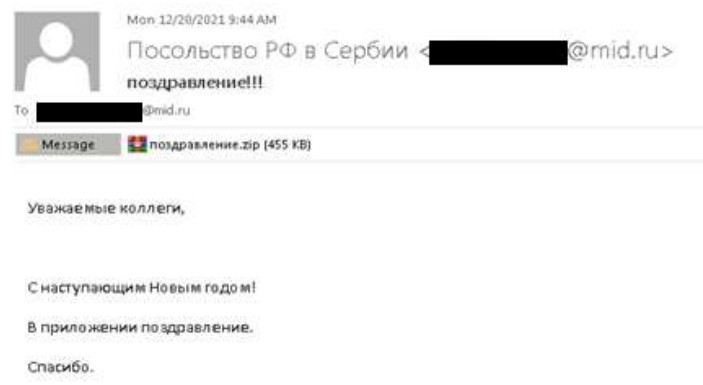
It was a congratulatory message that appeared to be from fellow diplomats at the Russian embassy in Serbia sending a ZIP archive with a holiday screensaver.
When extracted, the file was an executable that ultimately delivered the Konni RAT disguised as Windows service “scrnsvc.dll.”
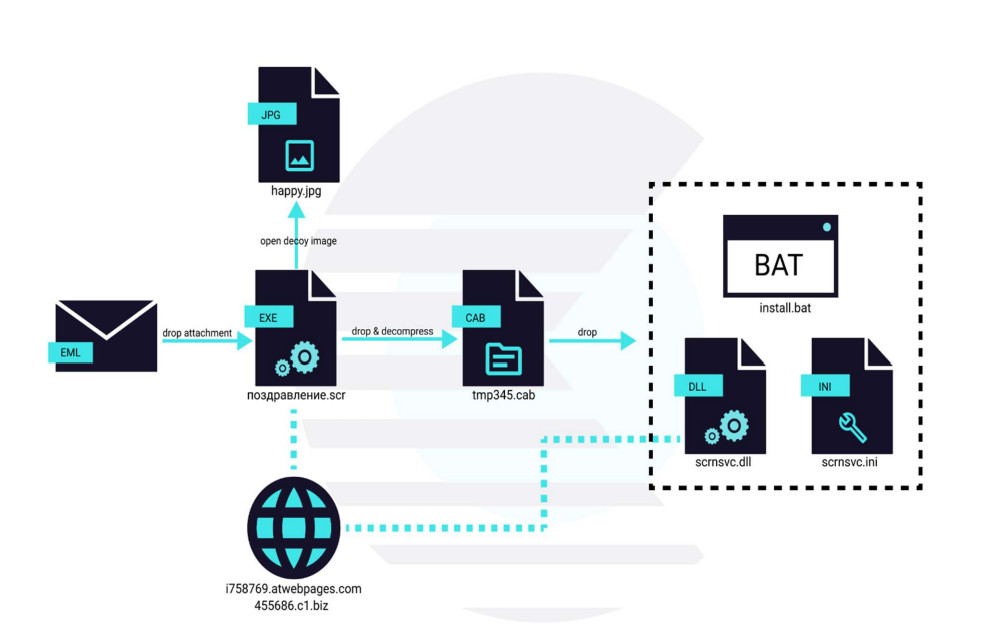
Researchers at Lumen’s Black Lotus Labs were also tracking these spear-phishing campaigns that had started at least two months earlier, the likely goal being to harvest credentials of an active MID account.
Also Read: Completed DPIA Example: 7 Simple Helpful Steps To Create
To achieve their objective, the attackers relied on spoofed hostnames for email services common in Russia, Mail.ru and Yandex.
Another campaign started around November 7, delivering URLs for downloading an archive with documents asking for information on the vaccination status.
The archive also included an executable posing as legitimate software used for checking the Covid-19 vaccination status, which executed a malware loader that infected the system with Konni.
According to Black Lotus Labs researchers, the campaign in December also spotted by Cluster25 was the third one from the same threat actor and used the compromised MID account “mskhlystova@mid[.]ru” to send out malicious emails.
The recipients of the malicious messages were the Russian embassy in Indonesia and Russian politician Sergey Alexeyevich Ryabkov, currently serving as Deputy Foreign Minister.
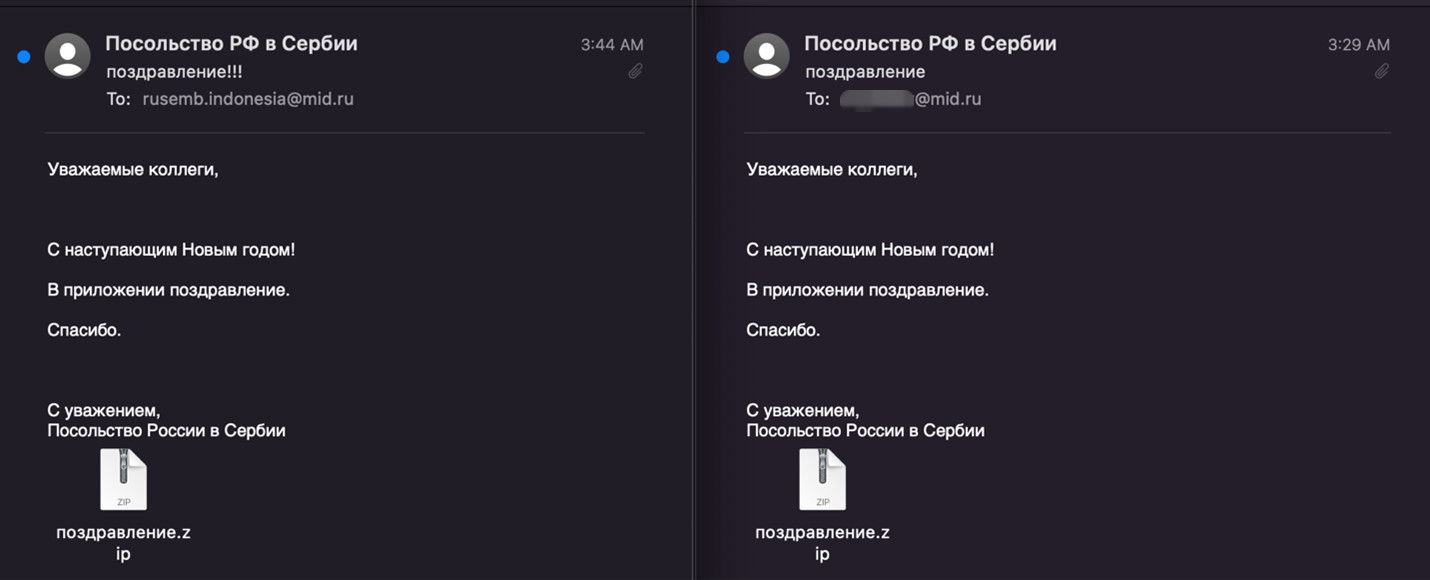
Looking at the email headers revealed that the source of the messages was the same IP address, 152.89.247[.]26, used for the phishing campaign in October, Black Lotus Labs found.
Technical analysis of the infection chain from Lumen’s researchers confirmed Cluster25’s findings, including the evasion technique of hiding a payload in a “401 unauthorized” server error response.

Black Lotus Labs researchers say that this was a highly targeted campaign that “downloaded a first-stage agent which is nearly identical to the agent” discovered by Malwarebytes in a Konni attack against Russian targets.
Both cybersecurity outfits are confident in attributing the spear-phishing campaigns against the Russian diplomatic entities to the Konni advanced persistent threat.