KEEP IN TOUCH
Subscribe to our mailing list to get free tips on Data Protection and Cybersecurity updates weekly!







Microsoft says threat actors could use a macOS vulnerability to bypass Transparency, Consent, and Control (TCC) technology to access users’ protected data.
The Microsoft 365 Defender Research Team has reported the vulnerability dubbed powerdir (tracked as CVE-2021-30970) to Apple on July 15, 2021, via the Microsoft Security Vulnerability Research (MSVR).
TCC is security tech designed to block apps from accessing sensitive user data by allowing macOS users to configure privacy settings for the apps installed on their systems and devices connected to their Macs, including cameras and microphones.
Also Read: Management Training PDF for Effective Managers and Leaders
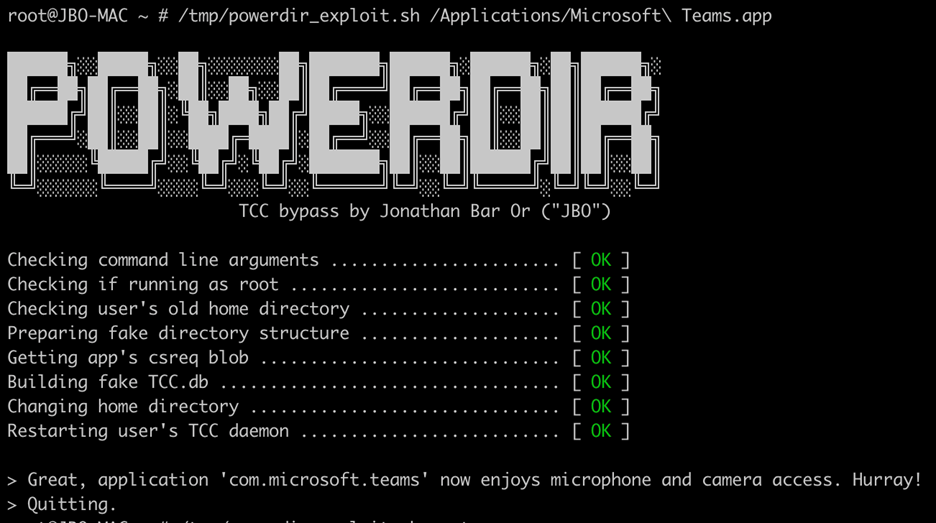
While Apple has restricted TCC access only to apps with full disk access and set up features to automatically block unauthorized code execution, Microsoft security researchers found that attackers could plant a second, specially crafted TCC database that would allow them to access protected user info.
“We discovered that it is possible to programmatically change a target user’s home directory and plant a fake TCC database, which stores the consent history of app requests,” said Jonathan Bar Or, a principal security researcher at Microsoft.
“If exploited on unpatched systems, this vulnerability could allow a malicious actor to potentially orchestrate an attack based on the user’s protected personal data.
“For example, the attacker could hijack an app installed on the device—or install their own malicious app—and access the microphone to record private conversations or capture screenshots of sensitive information displayed on the user’s screen.”
Apple has also patched other TCC bypasses reported since 2020, including:
Apple has fixed the vulnerability in security updates released last month, on December 13, 2021. “A malicious application may be able to bypass Privacy preferences,” the company explained in the security advisory.
Also Read: PDPA Laws And Regulations; A Systematic Guidelines In Singapore
Apple addressed the logic issue behind the powerdir security flaw bug with improved state management.
“During this research, we had to update our proof-of-concept (POC) exploit because the initial version no longer worked on the latest macOS version, Monterey,” Jonathan Bar Or added.
“This shows that even as macOS or other operating systems and applications become more hardened with each release, software vendors like Apple, security researchers, and the larger security community, need to continuously work together to identify and fix vulnerabilities before attackers can take advantage of them.”
Microsoft has previously reported finding a security flaw dubbed Shrootless that would allow an attacker to bypass System Integrity Protection (SIP) and perform arbitrary operations, elevate privileges to root, and install rootkits on vulnerable devices.
The company’s researchers also discovered new variants of macOS WizardUpdate malware (aka UpdateAgent or Vigram), updated with new evasion and persistence tactics.
Last year, in June, Redmond revealed critical firmware bugs in some NETGEAR router models that hackers could use to breach and move laterally within enterprise networks.