KEEP IN TOUCH
Subscribe to our mailing list to get free tips on Data Protection and Cybersecurity updates weekly!





A new Zloader campaign exploits Microsoft’s digital signature verification to deploy malware payloads and steal user credentials from thousands of victims from 111 countries.
The campaign orchestrated by a threat group known as MalSmoke appears to have started in November 2021, and it’s still going strong, according to Check Point researchers who have spotted it.
Zloader (aka Terdot and DELoader) is a banking malware first spotted back in 2015 that can steal account credentials and various types of sensitive private information from infiltrated systems.
More recently, Zloader has been used to drop further payloads on infected devices, including ransomware payloads such as Ryuk and Egregor,
Also Read: Best Privacy Certification: 3 Simple Steps On How To Achieve
MalSmoke has explored various ways of distributing the info-stealing malware, ranging from spam mail and malvertising to using adult content lures.
In the most recent campaign, tracked and analyzed by researchers at Check Point, the infection begins with delivering a “Java.msi” file that’s a modified installer of Atera.
Atera is a legitimate enterprise remote monitoring and management software widely used in the IT sector. As such, AV tools are unlikely to warn the victim, even if the installer is slightly modified.
It is unclear how the threat actors tricked the victims into downloading the malicious file, but it could be through cracks found on pirated software resources or spear-phishing emails.
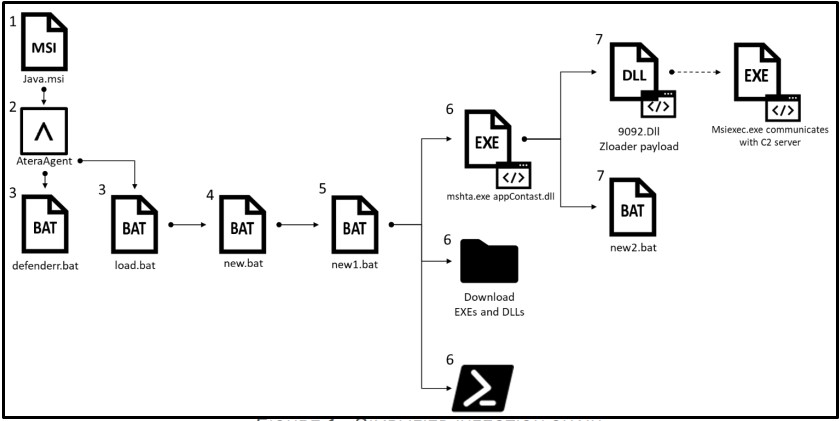
Upon execution, Atera creates an agent and assigns the endpoint to an email address under the threat actor’s control.
The attackers then gains full remote access to the system, which allows them to execute scripts and upload or download files, most notably Zloader malware payloads.
Also Read: Computer Misuse Act Singapore: The Truth And Its Offenses
Atera’s remote monitoring solution comes with 30 days of a free trial, which is more than enough for the adversaries to carry out the attack.
The batch scripts included in the malicious installer perform some user-level checks to ensure they have admin privileges, add folder exclusions to Windows Defender, and disable tools such as “cmd.exe” and the task manager.
Next, the following additional files are downloaded into the %AppData% folder:
Zloader is executed with “regsvr32.exe” and injected into the “msiexec.exe” process, which communicates with the C2 server (lkjhgfgsdshja[.]com).
Finally, the “new2.bat” script edits the registry to set the privileges of all applications to the administrator level. For this change to take effect, a restart is required, so the malware forces the infected system to reboot at this point.
Check Point analysts have confirmed that the appContast.dll, which executes the Zloader payload and the registry-editing script carries a valid code signature, so the OS essentially trusts it.
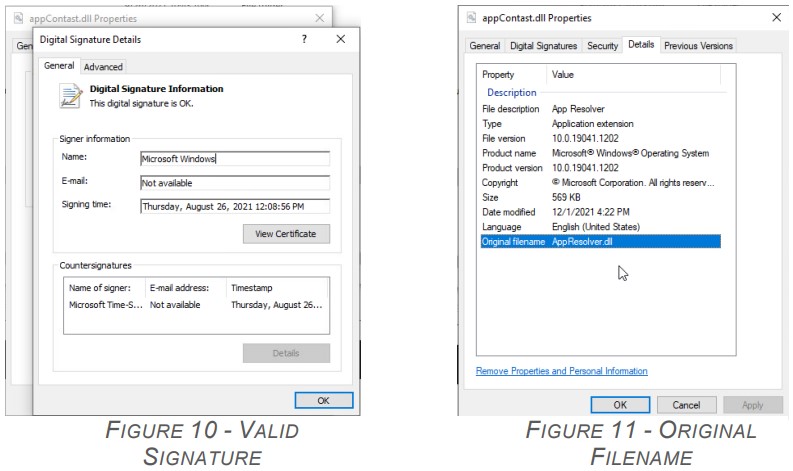
The analysts compared the modified DLL with the original one (Atera’s) and found slight modifications in the checksum and the signature size.
These subtle changes aren’t enough to revoke the validity of the e-signature, but at the same time, allow someone to append data onto the signature section of a file.
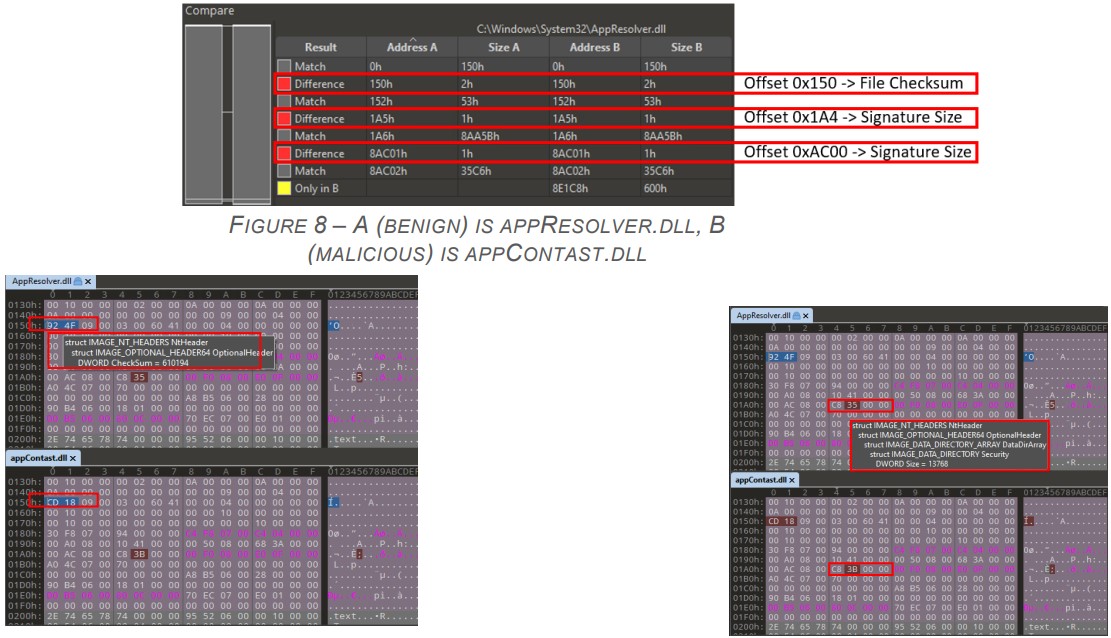
Microsoft has known about this security gap since 2012 (CVE-2020-1599, CVE-2013-3900, and CVE-2012-0151) and has attempted to fix it by releasing increasingly stricter file verification policies. However, for some reason, these remain disabled by default.
You can find instructions on fixing this issue yourself by enabling stricter policies as detailed in this legacy advisory.
Alternatively, you may paste the lines below into Notepad, save the file with the .reg extension and run it.
Windows Registry Editor Version 5.00
[HKEY_LOCAL_MACHINE\Software\Microsoft\Cryptography\Wintrust\Config]
"EnableCertPaddingCheck"="1"
[HKEY_LOCAL_MACHINE\Software\Wow6432Node\Microsoft\Cryptography\Wintrust\Config]
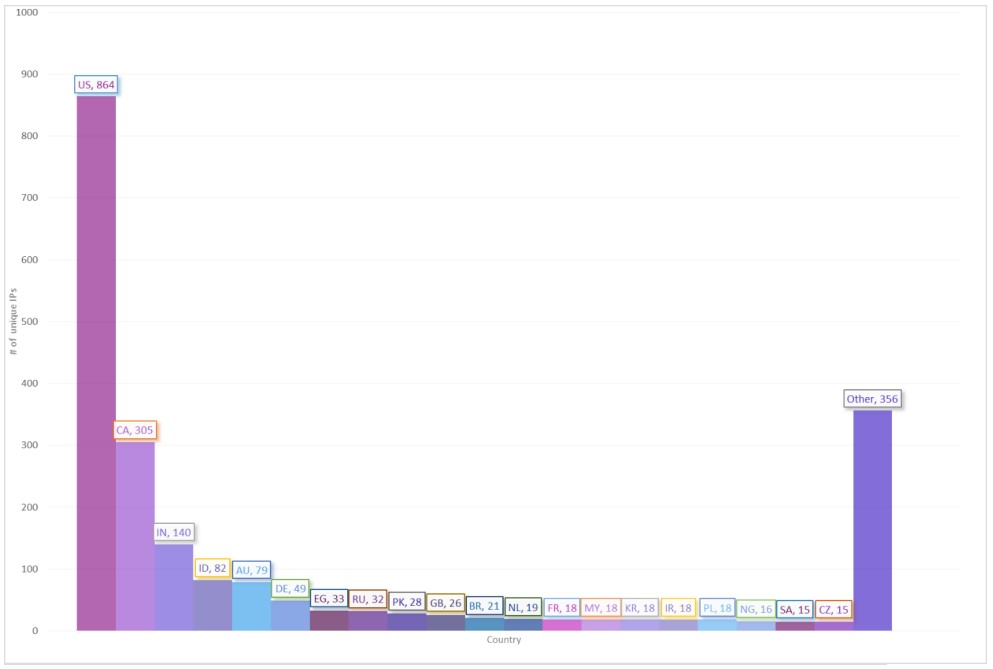
"EnableCertPaddingCheck"="1"As of January 2, 2021, the latest Zloader campaign has infected 2,170 unique systems, with 864 having US-based IP addresses and 305 more from Canada.
Although the number of victims doesn’t seem alarmingly large, these attacks are highly-targeted and can cause significant damage to each victim.
Because the infection vector is unknown, the best way to protect against this threat is to follow the policy tightening recommendations and use the IoCs (indicators of compromise) provided by Check Point’s researchers for pro-active threat detection.