KEEP IN TOUCH
Subscribe to our mailing list to get free tips on Data Protection and Cybersecurity updates weekly!







Apple has addressed a macOS vulnerability that unsigned and unnotarized script-based apps could exploit to bypass all macOS security protection mechanisms even on fully patched systems.
If they circumvent automated notarization security checks (which scans for malicious components and code-signing issues), the applications are allowed to launch by Gatekeeper, a macOS security feature designed to verify if downloaded apps are notarized and developer-signed.
Once malicious script-based apps targeting the bypass flaw (CVE-2021-30853) are launched on a target’s system, they can be used by attackers to download and deploy second-stage malicious payloads.
Apple has addressed this vulnerability in macOS 11.6 through a security update released in September 2021 that adds improved checks.
The CVE-2021-30853 Gatekeeper bypass bug was discovered and reported to Apple by Box Offensive Security Engineer Gordon Long.
He found that specially-crafted script-based applications downloaded from the Internet would launch without showing an alert even though automatically quarantined.
The “specially-crafted” part requires creating an app that uses a script starting with a shebang (!#) character but leaving the rest of the line empty, which tells the Unix shell to run the script without specifying a shell command interpreter.
This leads to a Gatekeeper bypass because the syspolicyd daemon automatically commonly invoked by the AppleSystemPolicy kernel extension to perform security checks (signing and notarization) no longer gets triggered for inspection when launching a script without specifying an interpreter.
Basically, if the script used a shebang (!#) but did not explicitly specify an interpreter, it would bypass Gatekeeper security checks.
“The syspolicyd daemon will perform various policy checks and ultimately prevent the execution of untrusted applications, such as those that are unsigned or unnotarized,” explained security researcher Patrick Wardle.
“But, what if the AppleSystemPolicy kext decides that the syspolicyd daemon does not need to be invoked? Well then, the process is allowed! And if this decision is made incorrectly, well then, you have a lovely File Quarantine, Gatekeeper, and notarization bypass.”
As revealed by Wardle, threat actors can exploit this flaw by tricking their targets into opening a malicious app that can also be camouflaged as a benign-looking PDF document.
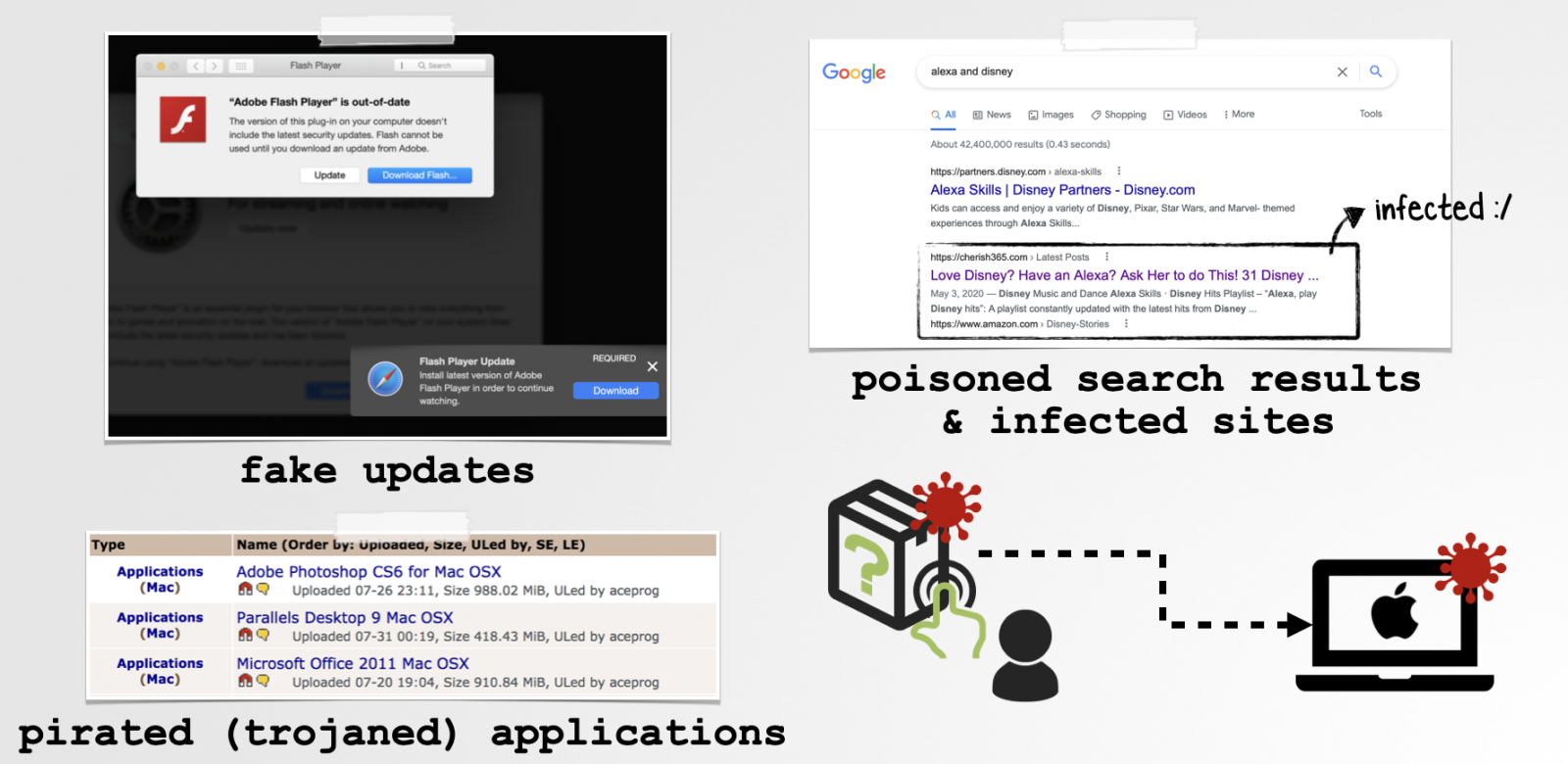
Such malicious payloads can be delivered on targets’ systems via many methods, including poisoned search results, fake updates, and trojaned applications downloaded from sites linking to pirated software.
This is not the first macOS bug fixed by Apple that would enable threat actors to completely circumvent OS security mechanisms such as Gatekeeper and File Quarantine on fully patched Macs.
In April, Apple patched a zero-day vulnerability exploited in the wild by Shlayer malware operators to bypass macOS automated security checks and deploy additional payloads on compromised Macs.
The Shlayer threat actors began targeting macOS users with unsigned and unnotarized malware that exploited the zero-day bug (tracked as CVE-2021-30657) starting with January 2021, as the Jamf Protect detection team discovered.
Microsoft also discovered a macOS vulnerability in October, dubbed Shrootless and tracked as CVE-2021-30892), that could be used to bypass System Integrity Protection (SIP) and perform arbitrary operations, elevate privileges to root, and install rootkits on compromised devices.
“A malicious application may be able to modify protected parts of the file system,” Apple said in a security advisory issued after patching the Shrootless bug.