KEEP IN TOUCH
Subscribe to our mailing list to get free tips on Data Protection and Cybersecurity updates weekly!







The Opera browser team is working on a new clipboard monitoring and protection system called Paste Protection, which aims to prevent content hijacking and snooping.
Opera introduced the new feature in development version 83, and Bleeping Computer has tested it on developer version 84, where it’s still present.
Also Read: Top 3 Common Data Protection Mistakes, Revealed
Paste Protection works automatically, monitoring the clipboard for sensitive data and locking it once it is added.
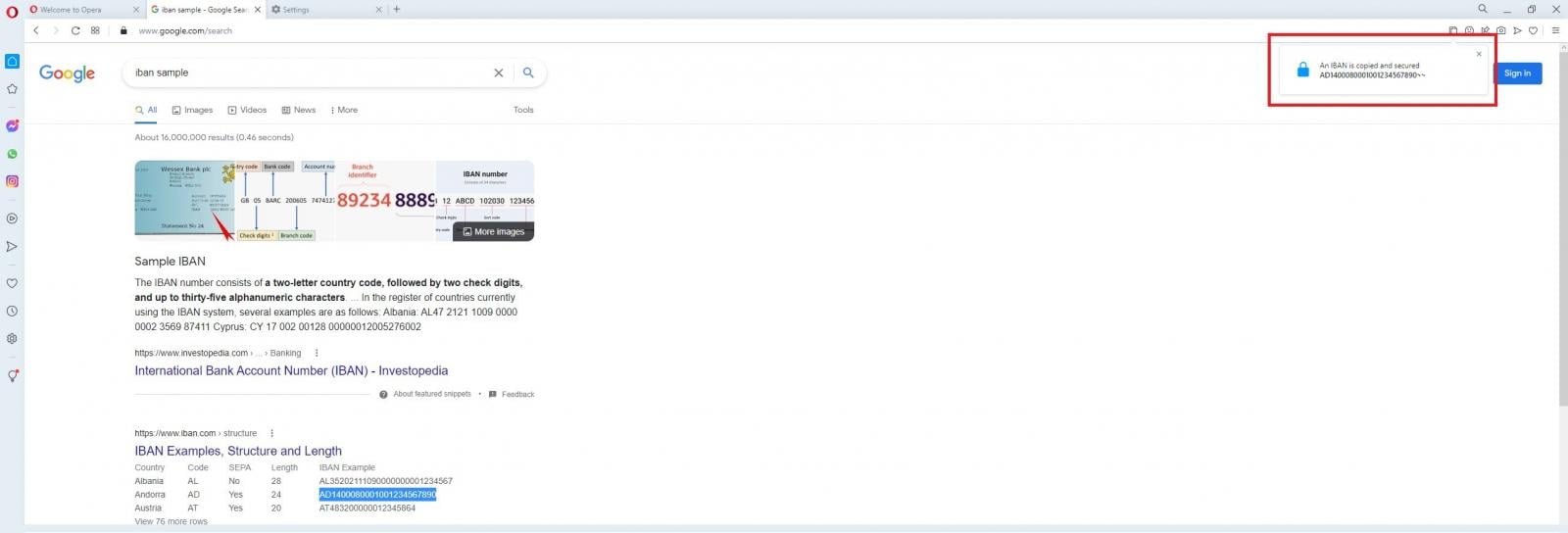
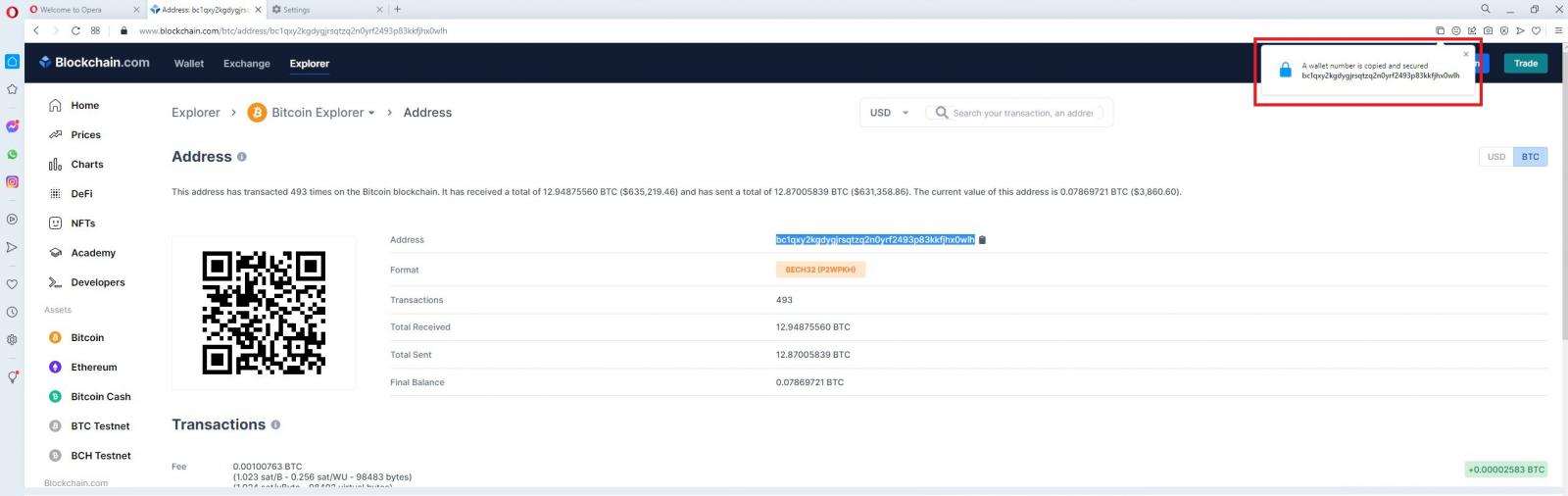
When the user copies a sensitive piece of information, a pop-up appears on the right corner to warn them that the content has been secured.
According to the few details the developers shared at this early development phase, the browser will display a new warning if an external application manages to change the clipboard content.
At this point, Opera hasn’t disclosed precisely which data and in what form is identified as sensitive, so we resorted to testing.
IBAN and Bitcoin wallet addresses qualify as sensitive data that require protection, but strangely, credit card numbers, email addresses, long passwords, and SSNs aren’t treated as such.
More types of data will likely be added to the Paste Protection monitoring scheme when the feature is ready to be rolled out in future stable Opera versions.
The latest available Opera stable version is 82, so the new security feature may land on the next release, scheduled for January 2022.
Also Read: The Financial Cost of Ransomware Attack
We have reached out to Opera to learn more about the upcoming feature, and we will update this post as soon as we have a response.
Clipboard protection is an important security feature that all web browsers should copy as it protects users from various malware infections that attempt to hijack a clipboard.
Clipboard hijackers are malware that replaces a copied cryptocurrency wallet address, which is the intended payment destination, with one controlled by the threat actor. Most people don’t memorize cryptocurrency addresses, so the coins or tokens will be sent to the threat actors’ wallets. Users only realize the mistake when the assets don’t appear at the intended address.
However, it’s too late by then, and there is no way to recover the funds.
Secondly, information disclosure through clipboard data capturing is a common feature in many information-stealers, so that the data exfiltration channel is also shut.
Even if Opera’s new feature finds widespread adoption among other browsers, it is still advisable to manually validate the contents of pasted data, especially when performing financial transactions.