KEEP IN TOUCH
Subscribe to our mailing list to get free tips on Data Protection and Cybersecurity updates weekly!







A dark web marketplace named ‘2easy’ is becoming a significant player in the sale of stolen data “Logs” harvested from roughly 600,000 devices infected with information-stealing malware.
“Logs” are archives of data stolen from compromised web browsers or systems using malware, and their most important aspect is that they commonly include account credentials, cookies, and saved credit cards.
2easy launched in 2018 and has experienced rapid growth since last year when it only sold data from 28,000 infected devices and was considered a minor player.
Based on an analysis by researchers at Israeli dark web intelligence firm KELA, the sudden growth is attributed to the market’s platform development and the consistent quality of the offerings that have resulted in favorable reviews in the cybercrime community.
Also Read: A Closer Look: The Personal Information Protection Law in China
The market is fully automated, which means someone can create an account, add money to their wallets, and make purchases without interacting with the sellers directly.
The logs are made available for purchase for as low as $5 per item, roughly five times less than the average Genesis prices and three times less than the average cost of bot logs on the Russian Market.
Moreover, based on actor feedback analysis from multiple dark web forums, 2easy logs consistently offer valid credentials that provide network access to many organizations.
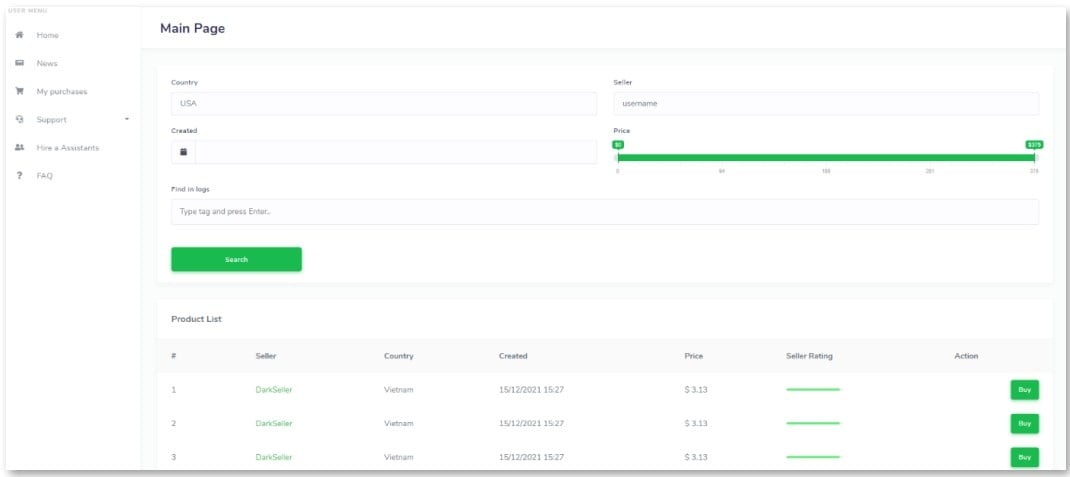
Besides the cost and validity, 2easy’s GUI is user-friendly and powerful at the same time, enabling actors to perform the following functions on the site:
The only downside compared to other platforms is that 2easy doesn’t give prospective buyers a preview of a sold item, such as the redacted IP address or OS version for the device the data was stolen.
Also Read: Battling Cyber Threats in 4 Simple Ways
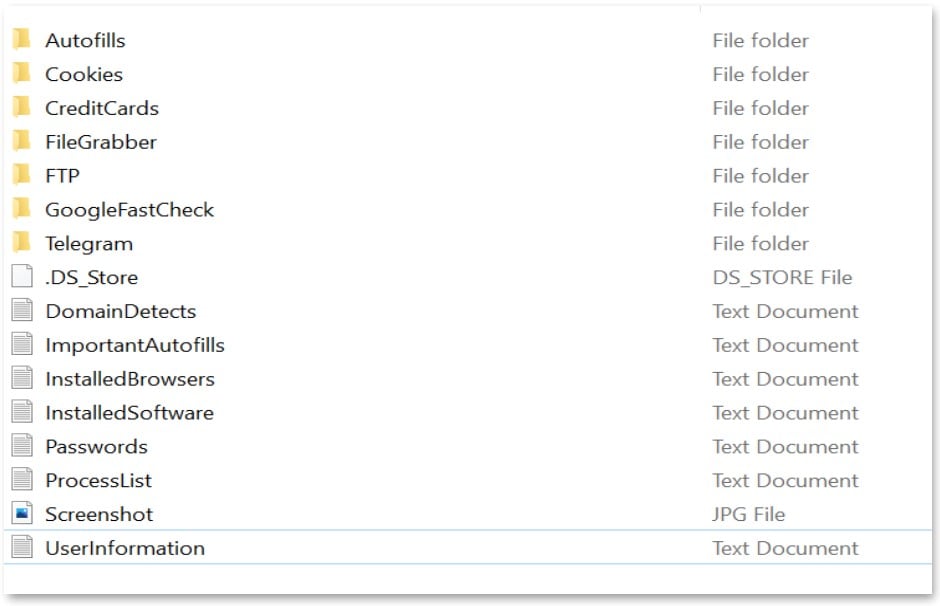
Each item purchased on 2easy comes in an archive file containing the stolen logs from the selected bot.
The content-type depends on the info-stealing malware used for the job and its capabilities, as each strain has a different focus set.
However, in 50% of the cases, the sellers use RedLine as their malware of choice, which can steal passwords, cookies, credit cards stored in web browsers, FTP credentials, and more, as shown below.
Five out of the 18 sellers active on 2easy use RedLine exclusively, while another four use it in conjunction with other malware strains like Raccoon Stealer, Vidar, and AZORult.
Logs containing credentials are essentially keys to doors, whether those doors lead to your online accounts, financial information, or even entry to corporate networks.
Threat actors sell this information for as little as $5 per piece, but the damage incurred to compromised entities could be counted in the millions.
“Such an example can be observed through the attack of Electronic Arts that was disclosed in June 2021,” explains KELA’s report
“The attack reportedly began with hackers who purchased stolen cookies sold online for just $10 and continued with hackers using those credentials to gain access to a Slack channel used by EA.”
“Once in the Slack channel, those hackers successfully tricked one of EA’s employees to provide a multi-factor authentication token, which enabled them to steal multiple source codes for EA games.”
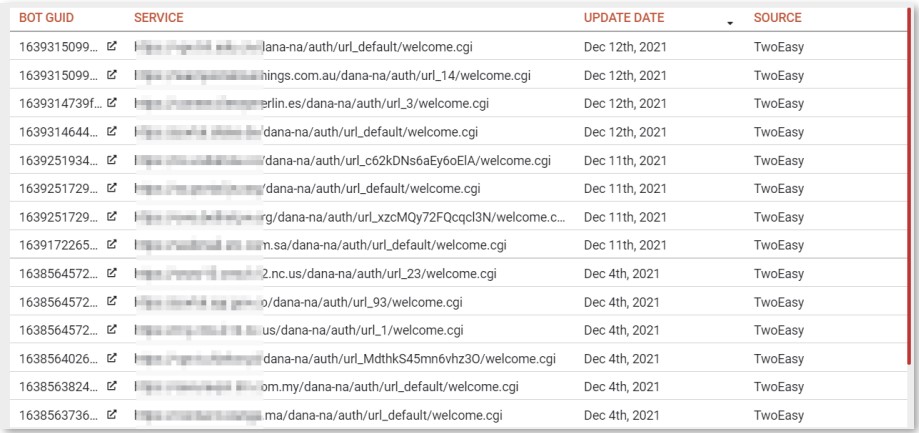
The initial access broker market is on the rise and is directly linked to catastrophic ransomware infections, while log marketplaces like 2easy are a part of the same ecosystem.
Millions of account credentials are offered for purchase on the dark web, so appropriate security measures that treat accounts as potentially compromised are needed.
Examples of those measures include multi-factor authentication steps, frequent password rotation, and applying the principle of least privilege for all users.