KEEP IN TOUCH
Subscribe to our mailing list to get free tips on Data Protection and Cybersecurity updates weekly!







Lenovo laptops, including ThinkPad and Yoga models, are vulnerable to a privilege elevation bug in the ImControllerService service allowing attackers to execute commands with admin privileges.
The flaws are tracked as CVE-2021-3922 and CVE-2021-3969 and affect the ImControllerService component of all Lenovo System Interface Foundation versions below 1.1.20.3. When viewing the Windows services screen, this service has a display name of “System Interface Foundation Service.”
The particular service is a component of Lenovo System Interface Foundation, which helps Lenovo devices communicate with universal apps like Lenovo Companion, Lenovo Settings, and Lenovo ID. The service is preinstalled by default on numerous Lenovo Models, including Yoga and ThinkPad devices.
Also Read: The Scope Of Singapore Privacy: How We Use It In A Right Way
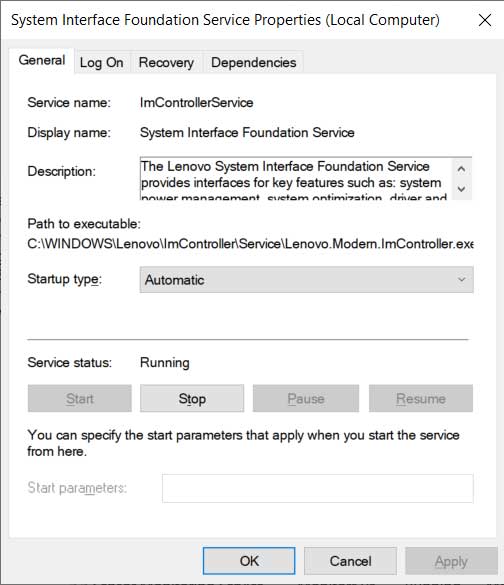
“The Lenovo System Interface Foundation Service provides interfaces for key features such as: system power management, system optimization, driver and application updates, and system settings to Lenovo applications including Lenovo Companion, Lenovo Settings and Lenovo ID,” reads the description of the Windows service.
“If you disable this service, Lenovo applications will not work properly.”
The discovery of the vulnerabilities was the work of researchers at NCC Group, who reported their findings to Lenovo on October 29, 2021.
The computer maker released the security updates on November 17, 2021, while the relevant advisory was published on December 14, 2021.
Also Read: 10 Best, Secured And Trusted Disposal Contractor In Singapore
Because ImController needs to fetch and install files from Lenovo servers, execute child processes, and perform system configuration and maintenance tasks, it runs with SYSTEM privileges.
SYSTEM privileges are the highest user rights available in Windows and allow someone to perform almost any command on the operating system. Essentially, if a user gains SYSTEM privileges in Windows, they gain complete control over the system to install malware, add users, or change almost any system setting.
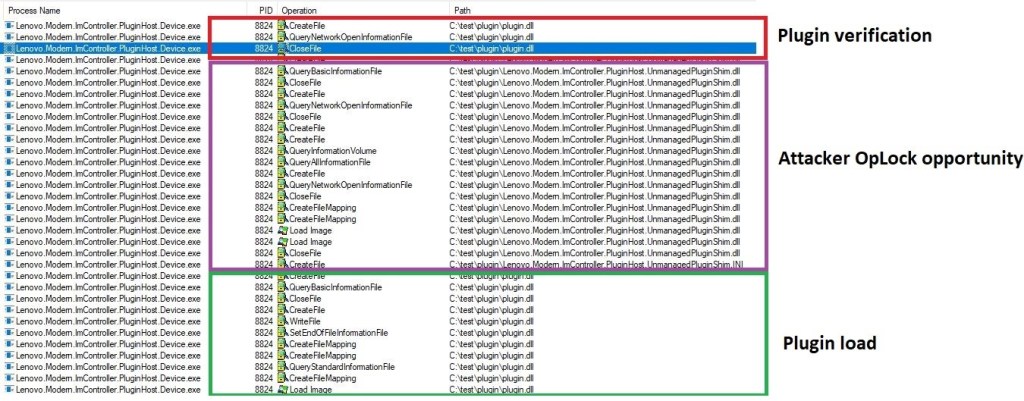
This Windows service will spawn further child processes, which open named pipe servers that the ImController service used to communicate with the child process. When ImController needs one of these services to execute a command, it will connect to the named pipe and issue XML serialized commands that should be executed.
Unfortunately, the service doesn’t handle the communications between privileged child processes securely and fails to validate the source of XML serialized commands. This means that any other process, even malicious ones, can connect to the child process to issue their own commands.
As such, an attacker leveraging this security gap can send an instruction to load a ‘plugin’ from an arbitrary location on the filesystem.
“The first vulnerability is a race condition between an attacker and the parent process connecting to the child process’ named pipe,” explains NCC Group
“An attacker using high-performance filesystem synchronization routines can reliably win the race with the parent process to connect to the named pipe.”
The researchers underline that their proof of concept code never failed to connect to the named pipe before the parent service could do so, which means the exploit is very reliable.
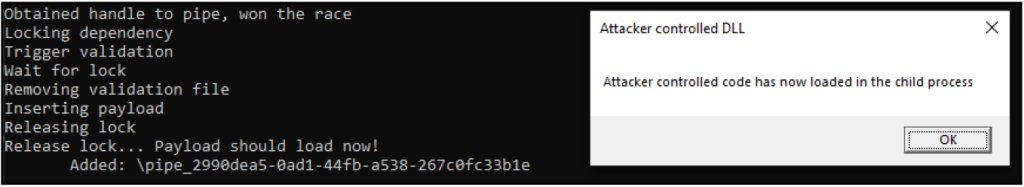
The second flaw is a time-of-check to time-of-use (TOCTOU) vulnerability which enables an attacker to stall the loading process of a validated ImControllerService plugin and replace it with a DLL of their choosing.
Once the lock is released and the loading procedure continues, the DLL is executed, leading to privilege escalation.
All Windows users with Lenovo laptops or desktops running the ImController version 1.1.20.2 or older are advised to upgrade to the latest available version (1.1.20.3).
To determine what version you’re running, follow these steps:
Removing the ImController component, or the Lenovo System Interface Foundation, from your device is not officially recommended because it may affect some functions on your device, even if it’s not considered essential.