KEEP IN TOUCH
Subscribe to our mailing list to get free tips on Data Protection and Cybersecurity updates weekly!







Approximately 300,000 MikroTik routers are vulnerable to critical vulnerabilities that malware botnets can exploit for cryptomining and DDoS attacks.
MikroTik is a Latvian manufacturer of routers and wireless ISPs who has sold over 2,000,000 devices globally.
In August, the Mēris botnet exploited vulnerabilities in MikroTik routers to create an army of devices that performed a record-breaking DDoS attack on Yandex. MikroTik explained that the threat actors behind the attack exploited vulnerabilities fixed in 2018 and 2019, but users hadn’t applied.
Researchers have found that far too many remain vulnerable to three critical remote code execution flaws that can lead to a complete device takeover despite all of these warnings and attacks.
As illustrated in a report published by Eclypsium today, the situation remains highly problematic.
Also Read: Vulnerability Assessment vs Penetration Testing: And Why You Need Both
Researchers from Eclypsium scanned the Internet for MikroTik devices that are still vulnerable to the following four CVEs:
The devices need to run RouterOS version 6.45.6 or older to be eligible for exploitation and have their WinBox protocol exposed to the Internet.
After scanning the Internet, Eclypsium found approximately 300,000 IP addresses for MikroTik routers that meet the above criteria and are vulnerable to at least one of the vulnerabilities mentioned above.
These devices have considerable horsepower, making them enticing targets for cryptomining and distributed denial-of-service attacks.
“First of all, they are plentiful with more than 2,000,000 devices deployed worldwide, and also particularly powerful and feature-rich devices,” explained the Eclypsium researchers.
Also Read: When to Appoint a Data Protection Officer
“In addition to serving SOHO environments, MikroTik routers and wireless systems are regularly used by local ISPs. The same horsepower that can make MikroTik enticing to an ISP, can also be enticing to an attacker.”
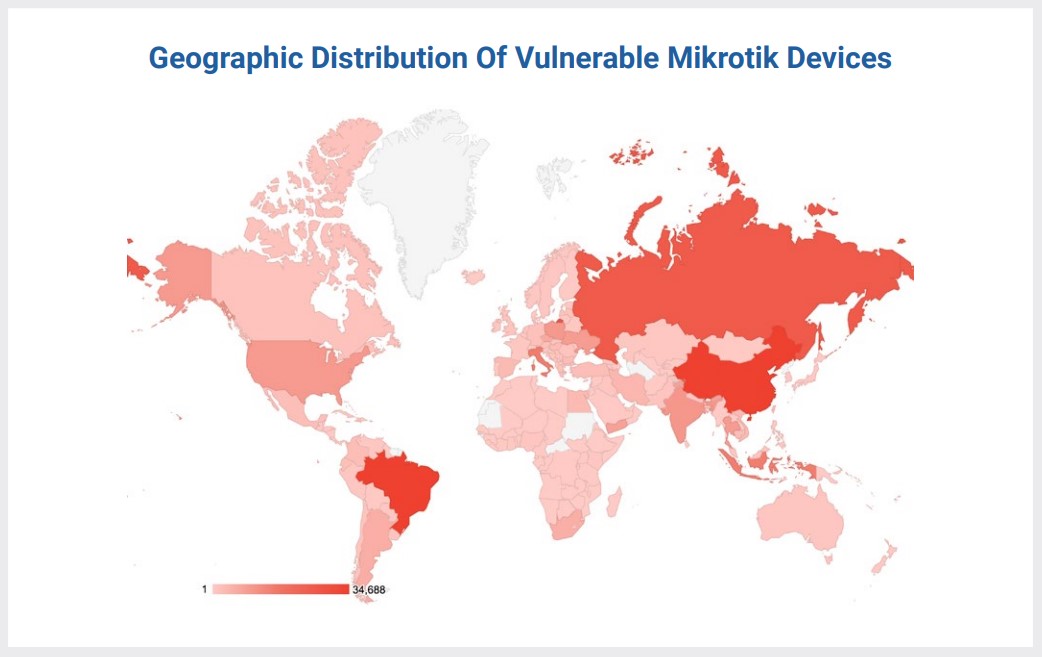
Most of the discovered devices are in China, Brazil, Russia, and Italy, while the United States has a significant number of exploitable devices too.
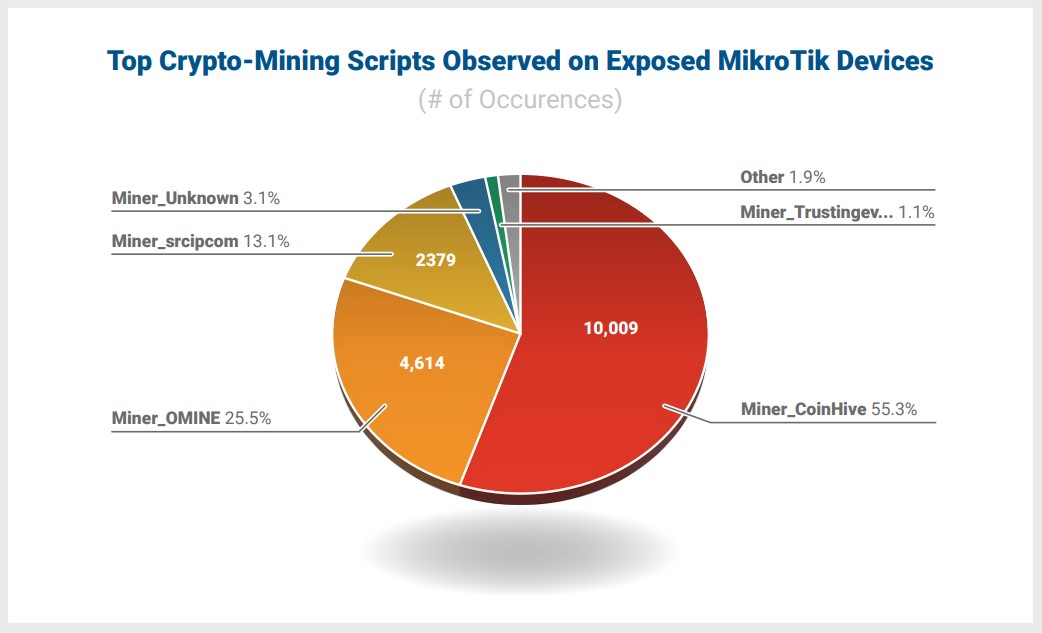
Interestingly, the researchers found that coin-miners had infected about 20,000 of these devices, with roughly half of them attempting to connect to the now-offline CoinHive.
Unfortunately, even with repeated warnings and 2-year-old security updates to resolve these vulnerabilities, too many routers are not updated to the latest software.
Furthermore, devices exploited before the security updates must be analyzed and passwords reset, as installing the updates will not resolve a prior compromise.
The official MikroTik advice towards all its customers can be summed in the following:
In addition to these guidelines, Eclypsium has released a free MikroTik assessment tool that can check if a device is vulnerable to CVE-2018-14847 and if a scheduler script exists, an indication of Mēris compromise.
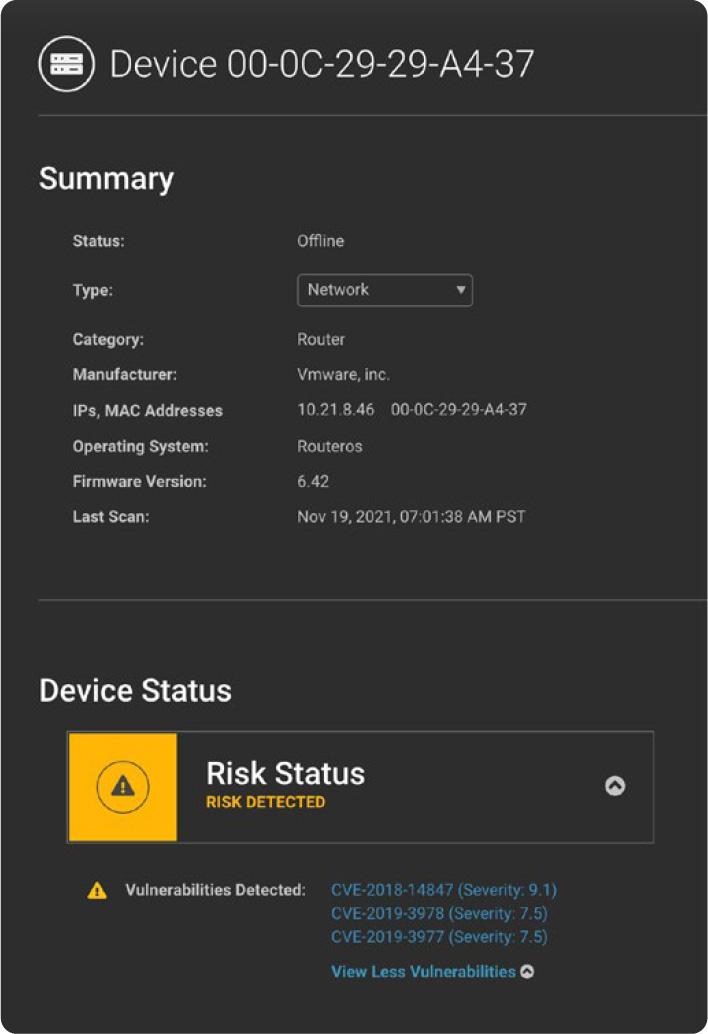
MikroTik owners must address the flaws on their devices, as the malware can harm the devices due to extensive cryptomining and make the device a physical part of malicious operations.
Bleeping Computer has reached out to MikroTik for a comment on the above, and got the following response:
Eclypsium report deals with the same old vulnerabilities we have mentioned in our previous security blogs. As far as we know – there are no new vulnerabilities in RouterOS. Furthermore, RouterOS has been recently independently audited by several third parties. They all arrived at the same conclusion.
Unfortunately, closing the old vulnerability does not immediately protect the affected routers. We don’t have an illegal backdoor to change the user’s password and check their firewall or configuration. These steps must be done by the users themselves.
We try our best to reach out to all users of RouterOS and remind them to do software upgrades, use secure passwords, check their firewall to restrict remote access to unfamiliar parties, and look for unusual scripts. Unfortunately, many users have never been in contact with MikroTik and are not actively monitoring their devices. We cooperate with various institutions worldwide to look for other solutions as well.
Meanwhile, we want to stress the importance of keeping your RouterOS installation up to date once again. That is the essential step to avoid all kinds of vulnerabilities.