KEEP IN TOUCH
Subscribe to our mailing list to get free tips on Data Protection and Cybersecurity updates weekly!







Microsoft says the first Secured-core certified Windows Server and Microsoft Azure Stack HCI devices are now available to protect customers’ networks from security threats, including ransomware attacks.
Secured-core devices are marketed as a solution to the increasing number of firmware vulnerabilities attackers can exploit to bypass a Windows machines’ Secure Boot and the lack of visibility at firmware level in today’s endpoint security solutions.
All Secured-core devices come with built-in protection for threats that abuse firmware and driver security flaws are since October 2019. They can help defend against malware designed to take advantage of driver security flaws to disable security solutions.
Also Read: What is Pentest Report? Here’s A Walk-through
The newly certified Secured-core servers use Secure boot and the Trusted Platform Module 2.0 to ensure that only trusted will be able to load on boot.
They also leverage Dynamic Root of Trust Measurement (DRTM) to launch the operating system into a trusted state, blocking malware attempts to tamper with the system.
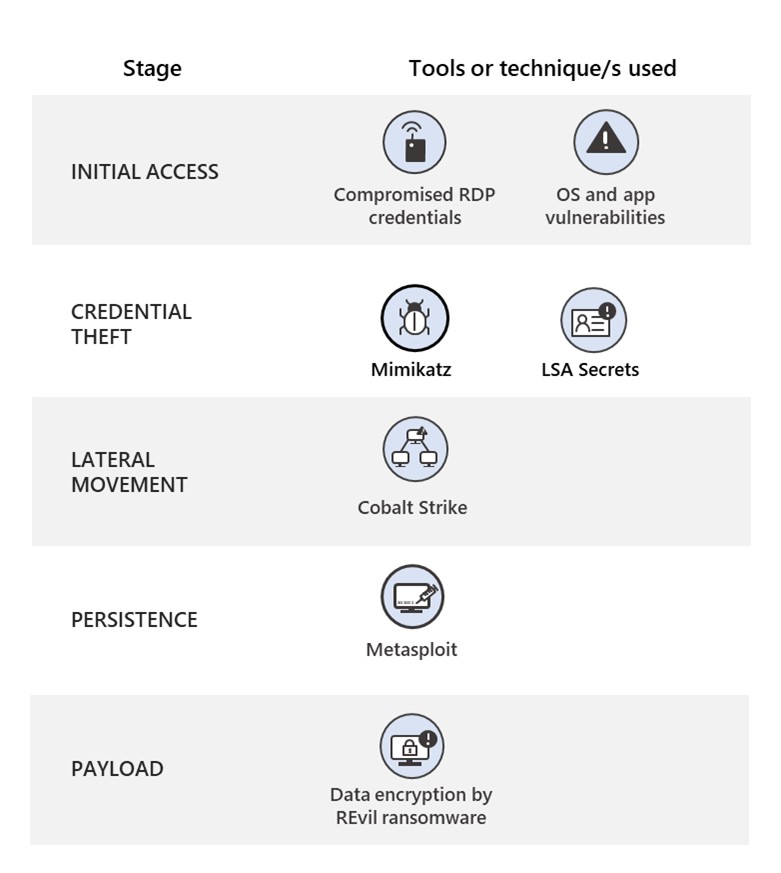
Secured-core servers also use Hypervisor-Protected Code Integrity (HVCI) to block all executables and drivers (such as Mimikatz) not signed by known and approved authorities from launching.
“Additionally, since Virtualization-based security (VBS) is enabled out of the box, IT administrators can easily enable features, such as Credential Guard, which safeguard the credentials in an isolated environment that is invisible to attackers,” Microsoft said.
By blocking credential theft attempts, Secured-core servers can help make it much harder for threat actors (including ransomware gangs such as REvil) to move laterally through the network, thus stopping their attacks before they can gain persistence and deploy their payloads.
For instance, Secured-core servers would have stopped RobbinHood Ransomware operators from exploiting a vulnerable GIGABYTE driver to elevate privileges and install malicious unsigned Windows drivers.
This made it possible to terminate antivirus and security software processes on compromised systems to bypass anti-ransomware defenses and deploy their payloads across the victim’s network.
Also Read: The PDPA Data Breach August 2020: A Recap of 8 Alarming Cases
Dozens of models with Secured-core server functionality are now available in the Azure Stack HCI catalog and the Windows Server Catalog lists.
You can manage the servers’ configuration and status together with all Windows clients on the network through the locally deployed and browser-based Windows Admin Center app.
“The Windows Admin Center UI allows you to easily configure the six features that encompass Secured-core server: Hypervisor Enforced Code Integrity, Boot Direct Memory Access (DMA) Protection, System Guard, Secure Boot, Virtualization-based security, and Trusted Platform Module 2.0,” Microsoft added.
Redmond first announced that Windows Server 2022 will expand Secured-core to the Windows Server platform when the new release entered preview in March.