KEEP IN TOUCH
Subscribe to our mailing list to get free tips on Data Protection and Cybersecurity updates weekly!







“Domain spoofing remains a huge threat to programmatic” and “FT warns advertisers after discovering high levels of domain spoofing“. These are some of the headlines that we come to see from our timelines or tabloids from time to time, reminding us that domain spoofing is not something that you can just brush off.
According to the 2019 Thales Access Management Index, domain or website spoofing has increased in the last year, resulting in $1.3 billion in damages. It also has long-term consequences for a company’s reputation, consumer trust, and income.
Domain spoofing is a serious threat to your business, but fortunately, there are practices you can harness to protect your business from this menace. But before we delve into it, let us first define what domain spoofing is.
When an attacker seems to utilize a firm’s domain to impersonate a company or one of its workers, this is known as domain spoofing. This can be accomplished by sending emails with fictitious domain names that look authentic or by creating websites with slightly altered characters that appear to be correct.
A spoofed website or email will frequently use logos or other forms of exact visual design to effectively mimic the styling and branding of a legitimate company or organization. Users will often be asked to provide financial information or other sensitive data, with the expectation that it will be transferred to the correct place.
Also Read: PDPA compliance for the healthcare sector

Email Spoofing: It is forging an email header to make it appear as if the message came from someone or somewhere different from the actual source. Users don’t want to open an email if they don’t trust the source; hence, email spoofing is employed in phishing and spam campaigns. Email spoofing aims to persuade recipients to open or even reply to a solicitation.
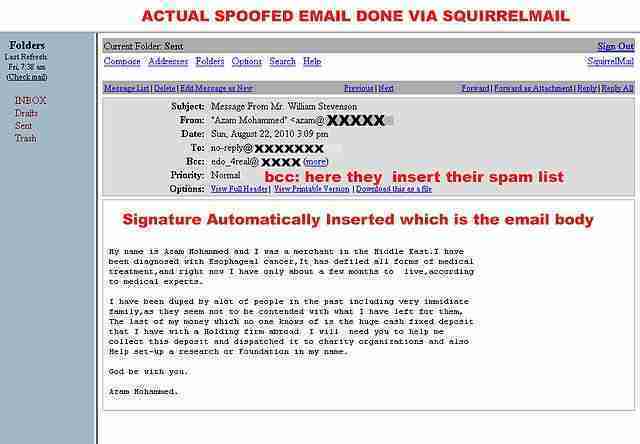
Website spoofing: The process of creating a phony website with the intent of misleading users, earning their trust, and impersonating the identity of a legitimate group or organization is known as website spoofing. The spoof website will frequently duplicate the target website’s design and, in some cases, the URL with alternate characters. In a more complex attack, the perpetrator may create a ‘shadow’ version of the Internet by routing all users’ online traffic through the attacker’s console. This type of attack collects all of the victim’s personal data.
A cloaked URL is another approach employed by domain spoofing attackers. The URL can appear authentic while concealing the actual website’s address by employing domain forwarding or inserting control characters.
Email spoofing is possible because the Simple Mail Transfer Protocol (SMTP) does not provide a mechanism for address authentication. Although email address authentication protocols and mechanisms have been specified to battle email spoofing, adoption of those mechanisms has been slow. In addition, poorly designed mail servers provide no email security protection against cybercriminals.
To protect businesses from email spoofing, they can use email address authentication mechanisms like the Sender Policy Framework (SPF), Domain-based Message Authentication, Reporting and Conformance (DMARC), DomainKeys Identified Mail (DKIM), and the Sender ID Framework (SIDF).
SPF (Sender Policy Framework) is an email validation system that allows domain administrators to grant specific hosts permission to use a domain in email. This protected list of recognized domain names can be used to check validity.
DMARC (Domain-based Message Authentication, Reporting, and Conformance) is an email authentication mechanism with reporting and enforcement features. Reporting and enforcement are the two pillars of this system. DMARC can automate authentication verification and promptly alert administrators to fake email domains through reporting. When bogus domains are used, DMARC prevents emails from being sent to the mailbox.
DKIM stands for DomainKeys Identified Mail, and it is a method of validating the domain name identification of a message. A digital signature is applied to an email when it is created to confirm its legitimacy. DKIM does not have filtering capabilities, but it can be used to ensure the message’s legitimacy.
SID (Sender ID) is a protocol based on SPF and pushed by Microsoft. It is incorporated into exchange servers and reads the SMTP header. To verify the sender’s address, the service consults DNS records.

According to the Federal Trade Commission, domain spoofing assaults affect over 96 percent of businesses today in some way. With this, having the appropriate solutions to protect against the threat of an attack is a must for any individual or company. ,
Furthermore, experts recommend that users only access financial and other sensitive sites directly through the main page or other verified gateway to avoid being scammed by a spoof website.
Also Read: How ransomware infects a system and ways to prepare against it