KEEP IN TOUCH
Subscribe to our mailing list to get free tips on Data Protection and Cybersecurity updates weekly!







US universities are being targeted in multiple phishing attacks designed to impersonate college login portals to steal valuable Office 365 credentials.
The lures used in the latest campaigns include COVID-19 Delta and Omicron variants and various themes on how these allegedly impact the educational programs.
These campaigns are believed to be conducted by multiple threat actors starting in October 2021, with Proofpoint sharing details on the tactics, techniques, and procedures (TTPs) used in the phishing attacks.
Also Read: 5 Tips In Using Assessment Tools To A Successful Businesses
The phishing attack begins with an email that pretends to be information about the new Omicron variant, COVID-19 test results, additional testing requirements, or class changes.
These emails urge the recipient to click on an attached HTM file, which takes them to a cloned login page for their university’s login portal.

The samples published by Proofpoint look very convincing in terms of their appearance, and URLs use a similar naming pattern that includes the .edu top-level domain.
For example, a phishing attack targeting students of Arkansas State University used an URL of sso2[.]astate[.]edu[.]boring[.]cf.
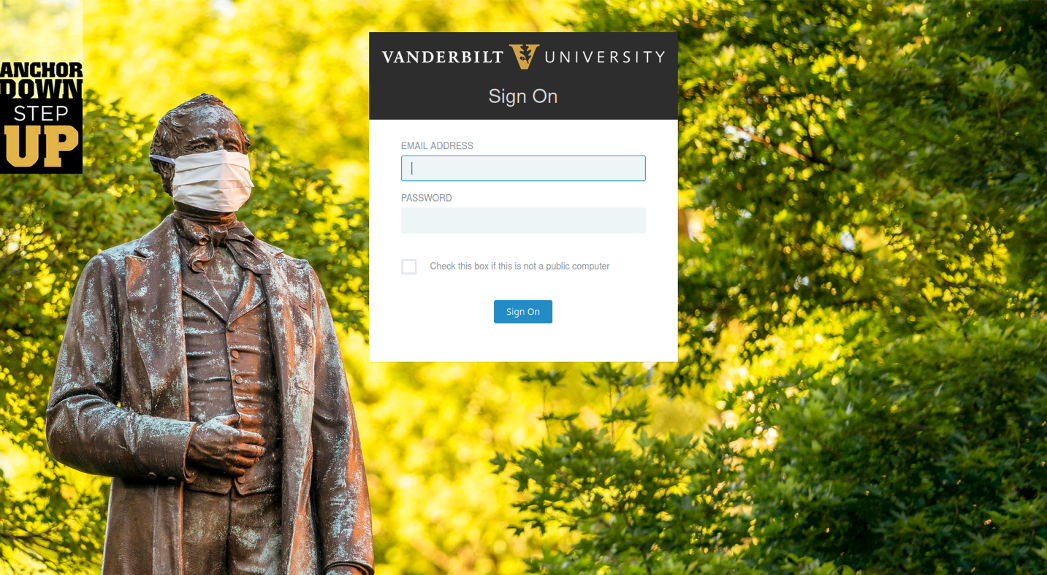
Other examples of malicious domains set up to support the phishing campaign are given below:
HTM attachments are having great success in phishing lately because they enable actors to smuggle malware and assemble it on the target device. In this case, however, the HTM contains a link to a credential-stealing site.
Also Read: Intrusion Into Privacy All About Law And Legal Definition
In some cases (marked with an asterisk), these destinations are legitimate WordPress sites that were compromised to steal credentials, so no alarms will be raised by internet security or email protection tools when the victim lands on them.
Based on the URLs shared by Proofpoint, some of the universities targeted in these attacks include the University of Central Missouri, Vanderbilt, Arkansas State University, Purdue, Auburn, West Virginia University, and the University of Wisconsin-Oshkosh.
To bypass MFA (multi-factor authentication) protection on targeted university login pages, the threat actors have also created landing pages that spoof a DUO MFA page, which is used to steal the one-time passcodes sent to students and faculty.
After a victim enters their credentials on the spoofed login page, the victim is requested to enter the code they received via SMS on their phone so that actors can snatch it and use it directly to take over the account.
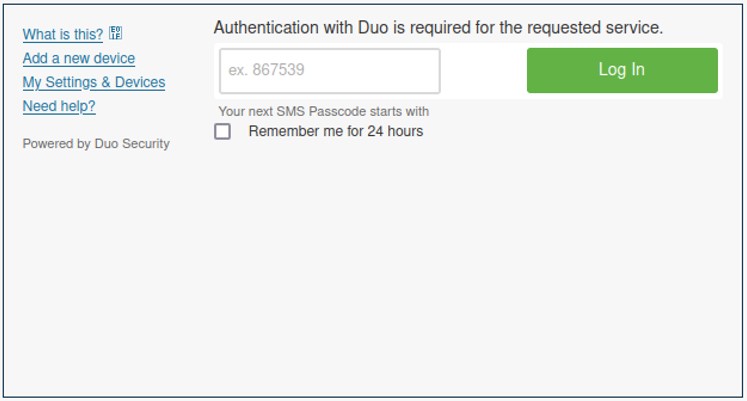
This step requires immediate action since OTPs have short expiration times.
Office 365 credentials can be used by malicious actors to access the corresponding email account, send messages to other users in the workgroup, divert payments, and further the phishing to steal more valuable accounts.
Additionally, the actor can access and exfiltrate sensitive information stored in the account’s OneDrive and SharePoint folders.
These phishing attacks could potentially lead to damaging BEC incidents and highly-disruptive ransomware infections for universities.
HTM files are opened in a browser, so technically, you can never be 100% safe. Do not give in to the curiosity if you receive one as an attachment in an unsolicited email.
Just mark the message as spam and delete it.