KEEP IN TOUCH
Subscribe to our mailing list to get free tips on Data Protection and Cybersecurity updates weekly!







Threat actors are distributing altered KMSpico installers to infect Windows devices with malware that steals cryptocurrency wallets.
This activity has been spotted by researchers at Red Canary, who warn that pirating software to save on licensing costs isn’t worth the risk.
KMSPico is a popular Microsoft Windows and Office product activator that emulates a Windows Key Management Services (KMS) server to activate licenses fraudulently.
According to Red Canary, many IT departments using KMSPico instead of legitimate Microsoft software licenses are much bigger than one would expect.
“We’ve observed several IT departments using KMSPico instead of legitimate Microsoft licenses to activate systems,” explained Red Canary intelligence analyst Tony Lambert.
“In fact, we even experienced one ill-fated incident response engagement where our IR partner could not remediate one environment due to the organization not having a single valid Windows license in the environment.”
Also Read: The Competency Framework: A Guide for Managers and Staff
KMSPico is commonly distributed through pirated software and cracks sites that wrap the tool in installers containing adware and malware.
As you can see below, there are numerous sites created to distribute KMSPico, all claiming to be the official site.
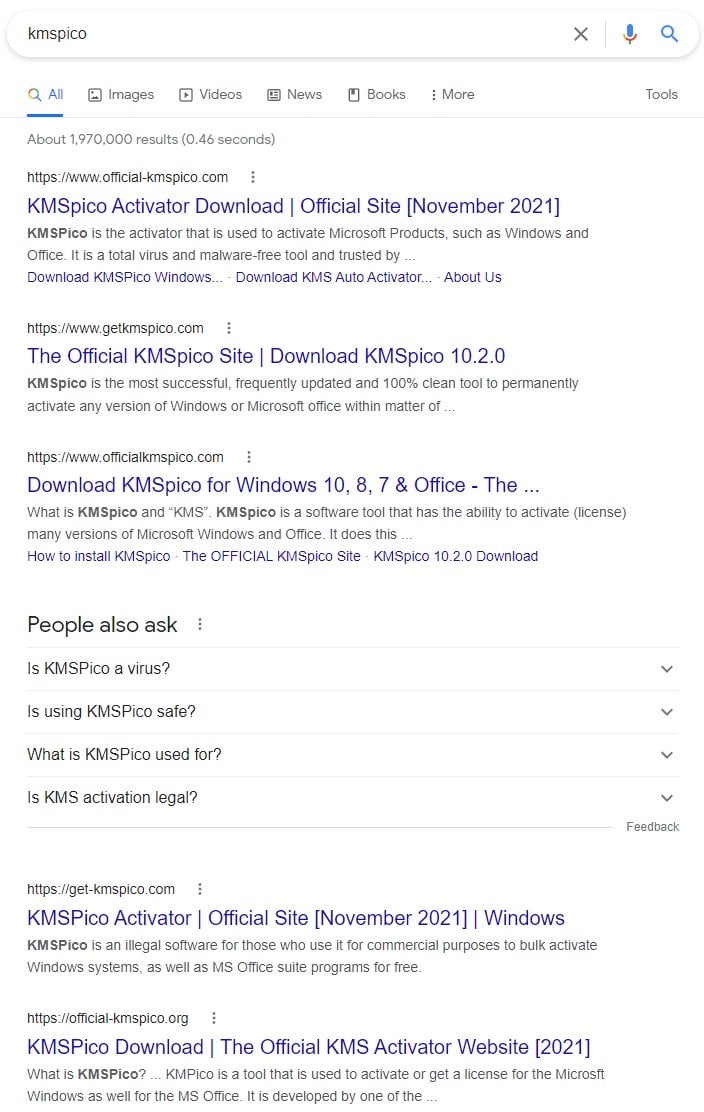
A malicious KMSPico installer analyzed by RedCanary comes in a self-extracting executable like 7-Zip and contains both an actual KMS server emulator and Cryptbot.
“The user becomes infected by clicking one of the malicious links and downloads either KMSPico, Cryptbot, or another malware without KMSPico,” explains a technical analysis of the campaign,
“The adversaries install KMSPico also, because that is what the victim expects to happen, while simultaneously deploying Cryptbot behind the scenes.”
The malware is wrapped by the CypherIT packer that obfuscates the installer to prevent it from being detected by security software. This installer then launches a script that is also heavily obfuscated, which is capable of detecting sandboxes and AV emulation, so it won’t execute when run on the researcher’s devices.
Also Read: Personal Data Protection Act Australia
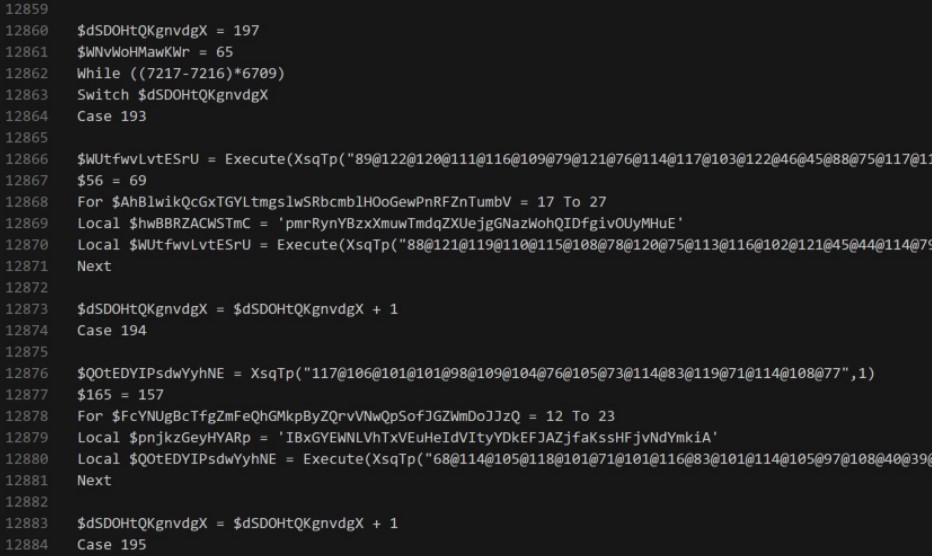
Moreover, Cryptobot checks for the presence of “%APPDATA%\Ramson,” and executes its self-deletion routine if the folder exists to prevent re-infection.
The injection of the Cryptbot bytes into memory occurs through the process hollowing method, while the malware’s operational features overlap with previous research findings.
In summary, Cryptbot is capable of collecting sensitive data from the following apps:
Because Cryptbot’s operation doesn’t rely on the existence of unencrypted binaries on the disk, detecting it is only possible by monitoring for malicious behavior such as PowerShell command execution or external network communication.
Red Canary shares the following four key points for threat detection:
In summary, if you thought that KSMPico is a smart way to save on unnecessary licensing costs, the above illustrates why that’s a bad idea.
The reality is that the loss of revenue due to incident response, ransomware attacks, and cryptocurrency theft from installing pirated software could be more than the cost of the actual Windows and Office licenses.