KEEP IN TOUCH
Subscribe to our mailing list to get free tips on Data Protection and Cybersecurity updates weekly!







Security researchers analyzed nine popular WiFi routers and found a total of 226 potential vulnerabilities in them, even when running the latest firmware.
The tested routers are made by Asus, AVM, D-Link, Netgear, Edimax, TP-Link, Synology, and Linksys, and are used by millions of people.
The front-runners in terms of the number of vulnerabilities are the TP-Link Archer AX6000, having 32 flaws, and the Synology RT-2600ac, which has 30 security bugs.
Also Read: Data Protection Framework: Practical Guidance for Businesses
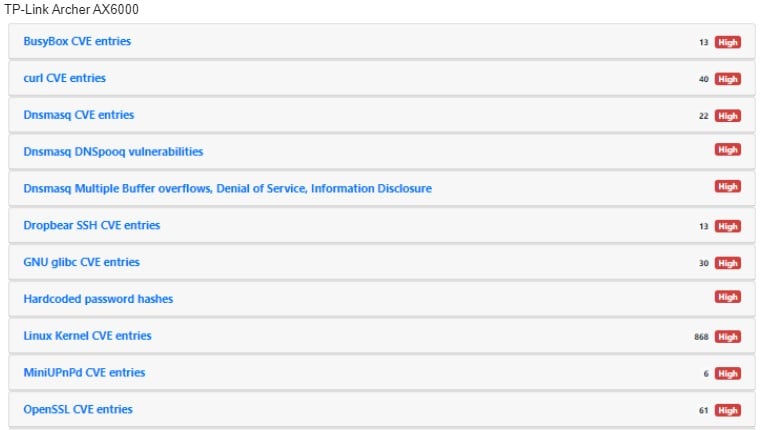
Researchers at IoT Inspector carried out the security tests in collaboration with CHIP magazine, focusing on models used mainly by small firms and home users.
“For Chip’s router evaluation, vendors provided them with current models, which were upgrade to the latest firmware version,” Florian Lukavsky, CTO & Founder at IoT Inspector, told BleepingComputer via email.
“The firmware versions were automatically analyzed by IoT Inspector and checked for more than 5,000 CVEs and other security issues.”
Their findings showed that many of the routers were still vulnerable to publicly disclosed vulnerabilities, even when using the latest firmware, as illustrated in the table below.
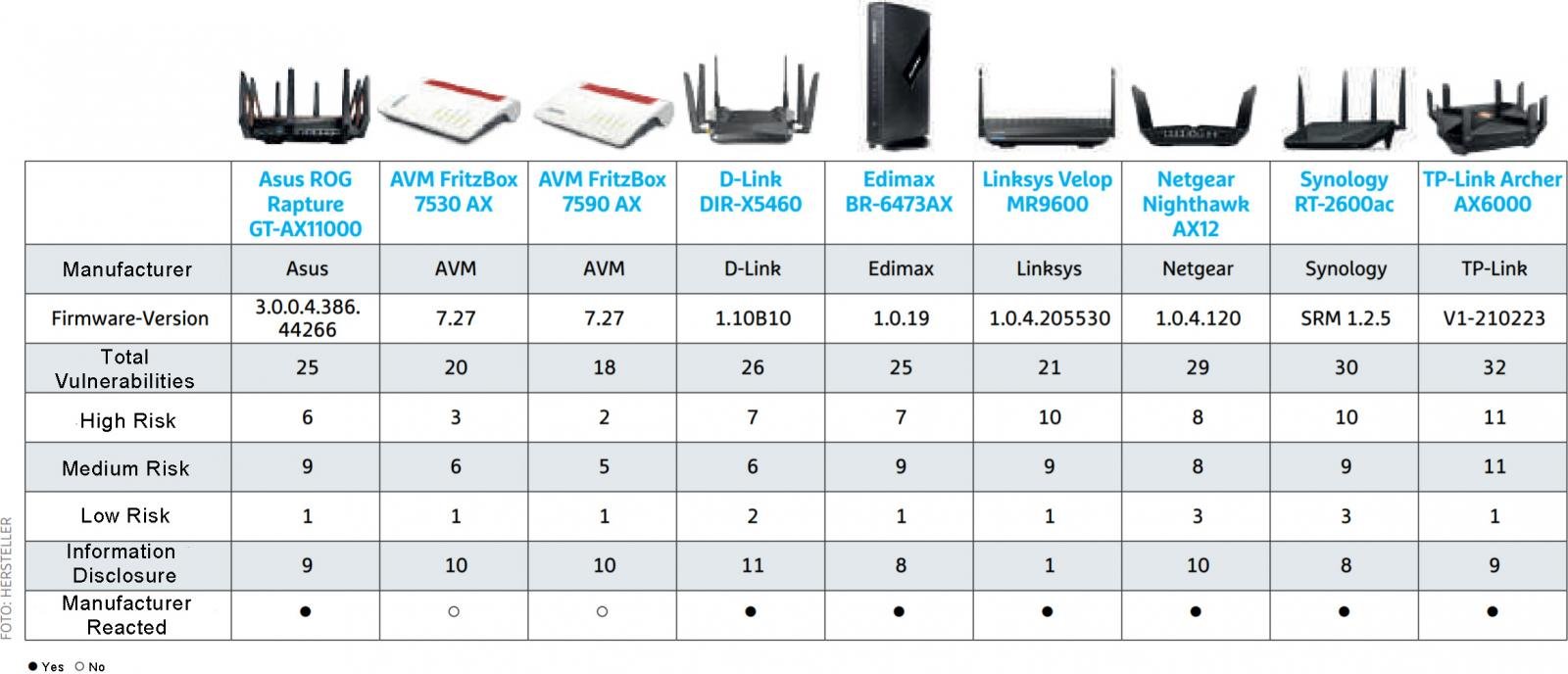
While not all flaws carried the same risk, the team found some common problems that affected most of the tested models:
Jan Wendenburg, the CEO of IoT Inspector, noted that one of the most important ways of securing a router is to change the default password when you first configure the device.
Also Read: Top 10 Exceptional And Creative Website Design Guidelines
“Changing passwords on first use and enabling the automatic update function must be standard practice on all IoT devices, whether the device is used at home or in a corporate network.” explained Wendenburg.
“The greatest danger, besides vulnerabilities introduced by manufacturers, is using an IoT device according to the motto ‘plug, play and forget’.”
The researchers didn’t publish many technical details about their findings, except for one case concerning the extraction of the encryption key for D-Link router firmware images.
The team found a way to gain local privileges on a D-Link DIR-X1560 and get shell access via the physical UART debug interface.
Next, they dumped the whole filesystem using built-in BusyBox commands and then located the binary responsible for the decryption routine.
By analyzing the corresponding variables and functions, the researchers eventually extracted the AES key used for the firmware encryption.
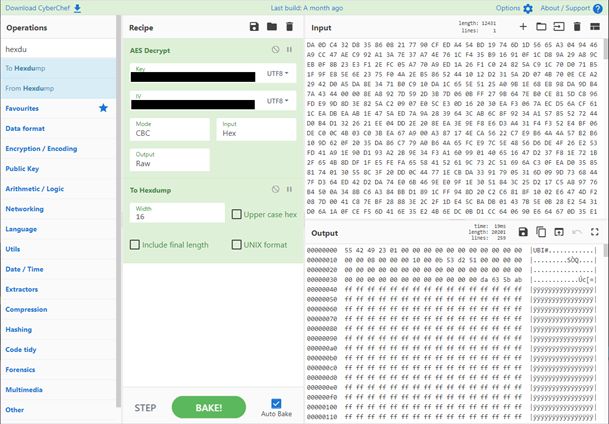
Using that key, a threat actor can send malicious firmware image updates to pass verification checks on the device, potentially planting malware on the router.
Such problems can be solved with full-disk encryption that secures locally stored images, but this practice is not common.
All of the affected manufacturers responded to the researchers’ findings and released firmware patches.
CHIP’s author Jörg Geiger commented that the router vendors addressed most of the security flaws identified by the working group, but not all of them.
The researchers have told Bleeping Computer that the unpatched flaws are mostly lower importance vulnerabilities. However, they clarified that no follow-up tests were done to confirm that the security updates fixed the reported issues.
The vendor responses to CHIP (translated) were the following:
If you are using any of the models mentioned in the report, you are advised to apply the available security updates, enable “automatic updates”, and change the default password to one that is unique and strong.
Additionally, you should disable remote access, UPnP (Universal Plug and Play), and the WPS (WiFi Protected Setup) functions if you’re not actively using them.
Bleeping Computer has contacted all of the affected manufacturers requesting a comment on the above, and we will update this piece as soon as we receive their response.